Kali Linux ‘Live’ provides a Forensic mode where you can just plug in a USB containing a Kali ISO. Whenever a forensic need arises you are able to do what you need without installing anything extra using the Kali Linux Live (Forensic Mode). Booting into Kali (Forensic mode) does not mount system hard drives, hence the operations you perform on the system do not leave any trace.
How to Use Kali’s Live (Forensic Mode)
To use “Kali’s Live (Forensic Mode),” you will need a USB drive containing Kali Linux ISO. To make one, you can follow official guidelines from Offensive Security, here:
https://www.kali.org/docs/usb/kali-linux-live-usb-install/
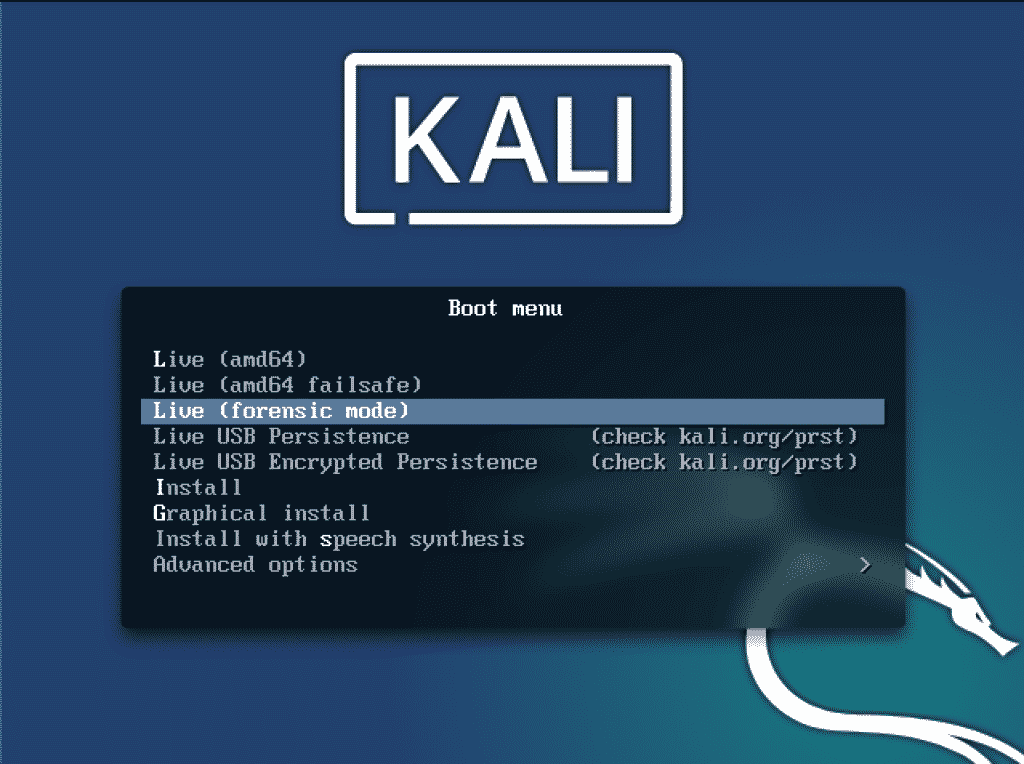
After preparing the Live Kali Linux USB, plug it in and restart your PC to enter the Boot loader. There, you will find a menu like this one:
Clicking on the Live (Forensic mode) will take you right into the forensics mode containing the tools and packages required for your forensic needs. In this article we will look at how to organize your digital forensics process using the Live (Forensic mode).
Copying Data
Forensics requires imaging of System Drives containing data. The first thing we need to do is make a bit-by-bit copy of the file, hard drive, or any other type of data on which we need to perform forensics. This is a very crucial step because if it is done wrong, then all the work can go to waste.
The regular backups of a drive or file do not work for us (the forensic investigators). What we need is a bit-by-bit copy of data on the drive. To do this, we will use the following dd command:
We need to make a copy of the drive sda1, so we will use the following command. It will make a copy of sda1 to sda2 512 byes at a time.
Hashing
With our copy of the drive, anyone can question its integrity and could think that we placed the drive intentionally. To generate proof that we have the original drive, we will use hashing. Hashing is used to assure the image integrity. Hashing will provide a hash for a drive, but if a single bit of data is changed, the hash will change and we will know if it has been replaced or is the original. To ensure the integrity of the data and that nobody can question its originality, we will copy the disk and generate an MD5 hash of it.
First, open dcfldd from the forensics toolkit.
The dcfld interface will look like this:
Now, we will use the following command:
/dev/sda: the drive you want to copy
/media/image.dd: the location and name of the image you want it to copy to
hash=md5: the hash you want to generate e.g md5, SHA1, SHA2, etc. In this case it is md5.
bs=512: number of bytes to copy at a time
One thing we should know is that Linux doesn’t provide drives names with a single letter like in windows. In Linux, hard drives are separated by hd designation, such as had, hdb, etc. For SCSI (small computer system interface) it is sd, sba, sdb, etc.
Now, we have the bit by bit copy of a drive on which we want to perform forensics. Here, forensic tools will come into play, and anyone with a knowledge of using these tools and can work with them will come in handy.
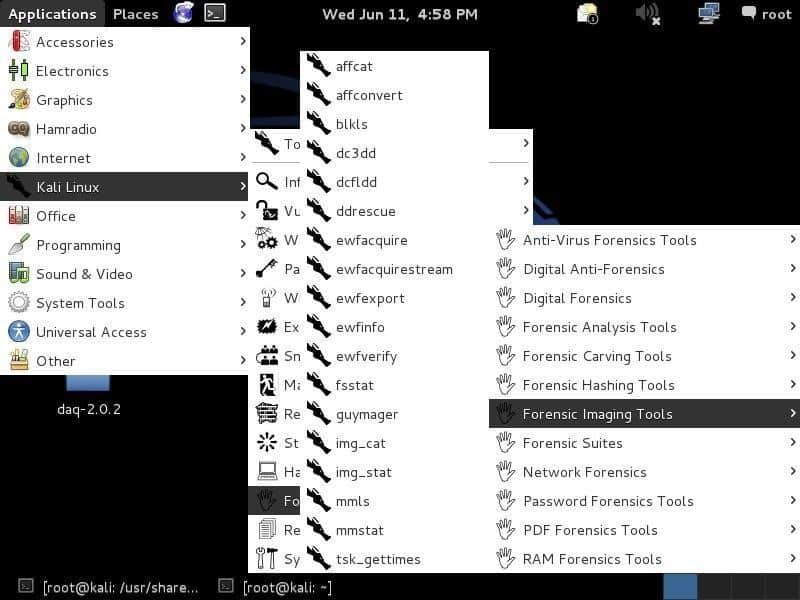
Tools
Forensics mode already contains famous open-source ToolKits and packages for forensic purposes. It is good to understand Forensics to inspect the crime and backtrack to whoever has done it. Any knowledge of how to use these tools would come in handy. Here, we will take a quick overview of some tools and how to get familiar with them
Autopsy
Autopsy Is a tool utilized by the military, law enforcement, and different agencies when there is a forensic need. This bundle is presumably one of the most powerful ones accessible through open-source, it consolidates the functionalities of numerous other littler bundles that are progressively engaged in their methodology into one flawless application with an internet browser-based UI.
To use autopsy, open any browser and type: http://localhost:9999/autopsy
Now, how about we open any program and explore the location above. This will essentially take us to the nearby web server on our framework (localhost) and get to port 9999 where Autopsy is running. I am utilizing the default program in Kali, IceWeasel. When I explore that address, I get a page like the one seen below:
Its functionalities incorporate – Timeline investigation, keyword search, hash separating, data carving, media, and markers of a bargain. Autopsy accepts disk images in raw oe EO1 formats and give results in whatever format is required usually in XML, Html formats.
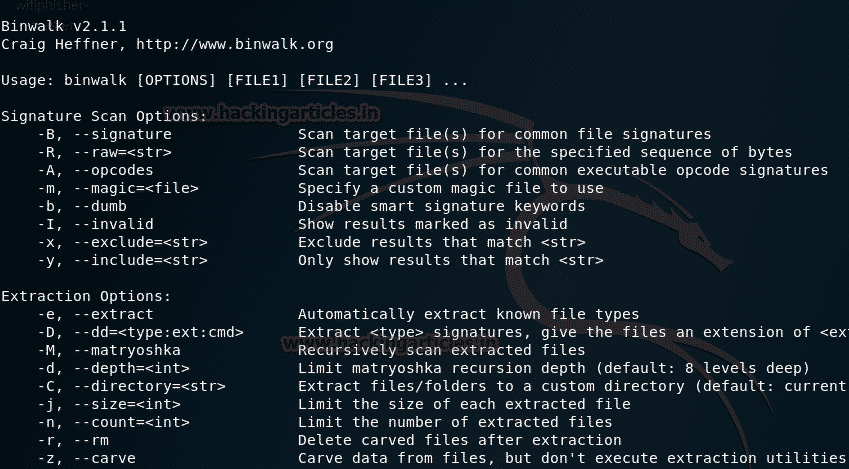
BinWalk
This tool is utilized while managing binary images, it has the ability of finding the inserted document and executable code by investigating the image file. It is an amazing asset for those who know what they are doing. When utilized right, you very well may discover delicate data covered up in firmware images that might reveal a hack or be used to discover an escape clause to misuse.
This tool is written in python and it uses the libmagic library, making it ideal for use with enchantment marks made for Unix record utility. To make things simpler for examiners, it contains an enchantment signature record which holds the most regularly discovered marks in firmware, which makes it simpler to spot inconsistencies.
Ddrescue
It duplicates information from one document or square gadget (hard drive, cd-rom, etc.) to another, attempting to protect the great parts first if there should arise an occurrence of read mistakes.
The essential activity of ddrescue is completely programmed. That is, you do not need to sit tight for a blunder, stop the program, and restart it from another position. If you utilize the mapfile highlight of ddrescue, the information is saved proficiently (just the required squares are perused). Likewise, you can intrude on the salvage whenever and continue it later at a similar point. The mapfile is a basic piece of ddrescue’s viability. Utilize it except if you know what you are doing.
To use it we will use the following command:
Dumpzilla
Dumpzilla application is created in Python 3.x and is used for extracting the measurable, fascinating data of Firefox, Ice-weasel, and Seamonkey programs to be examined. Because of its Python 3.x turn of events, it probably will not work appropriately in old Python forms with specific characters. The application works in an order line interface, so data dumps could be diverted by pipes with devices; for example, grep, awk, cut, sed. Dumpzilla allows users to picture the following areas, search customization and concentrate on certain areas:
- Dumpzilla can show live activities of users in tabs/windows.
- Cache data and thumbnails of previously opened windows
- User’s downloads, bookmarks, and history
- Browser’s saved passwords
- Cookies and session data
- Searches, email, comments
Foremost
Erase documents that may help unravel a computerized episode? Forget about it! Foremost is a simple-to-use, open-source bundle that can cut information out of arranged circles. The filename itself probably will not be recouped however the information it holds can be cut out. Foremost can recover jpg, png, bmp, jpeg, exe, mpg, ole, rar, pdf and a lot of other types of files.
foremost version 1.5.7 by Jesse Kornblum, Kris Kendall, and Nick Mikus.
$ foremost [-v|-V|-h|-T|-Q|-q|-a|-w-d] [-t <type>]
[-s <blocks>] [-k <size>]
[-b <size>] [-c <file>] [-o <dir>] [-i <file]
-V – display copyright information and exit
-t – specify file type. (-t jpeg,pdf …)
-d – turn on indirect block detection (for UNIX file-systems)
-i – specify input file (default is stdin)
-a – Write all headers, perform no error detection (corrupted files)
-w – Only write the audit file, do not write any detected files to the disk
-o – set output directory (defaults to output)
-c – set configuration file to use (defaults to foremost.conf)
-q – enables quick mode. Searches are performed on 512 byte boundaries.
-Q – enables quiet mode. Suppress output messages.
-v – verbose mode. Logs all messages to screen
Bulk Extractor
This is an exceptionally useful tool when an examiner is hoping to separate specific sort of information from the computerized proof record, this device can cut out email addresses, URL’s, installment card numbers, and so on. This tool takes a shot at catalogues, files, and disk images. The information can be halfway ruined, or it tends to be compacted. This device will discover its way into it.
This feature includes highlights which help make an example in the information that is found over and again, for example, URL’s, email ids and more and presents them in a histogram group. It has a component by which it makes a word list from the information discovered. This can help with splitting the passwords of scrambled documents.
RAM Analysis
We have seen memory analysis on hard drive images, but sometimes, we must capture data from live memory (Ram). Remember that Ram is a volatile memory source, which means it loses its data like open sockets, passwords, processes running as soon as it is turned off.
One of the many good things about memory analysis is the ability to recreate what the suspect was doing at the time of a mishap. One of the most famous tools for memory analysis is Volatility.
In Live (Forensics mode), first, we will navigate to Volatility using the following command:
As volatility is a Python script, enter the following command to see the help menu:
Before doing any work on this memory image, first we need to get to its profile by using the following command. The profile image helps volatility to know where in memory addresses the important information resides. This command will examine memory file for evidence of operating system and key information:
Volatility is a powerful memory analysis tool with tons of plugins that will help us investigate what the suspect was doing at the time of the computer seizure.
Conclusion
Forensics is increasingly becoming more and more essential in today’s digital world, where every day, many crimes are committed using digital technology. Having forensic techniques and knowledge in your arsenal is always an extremely useful tool to fight against cyber-crime on your own turf.
Kali is equipped with the tools needed to perform forensics, and by using Live (Forensic Mode), we do not have to keep it in our system all the time. Instead, we can just make a live USB or have Kali ISO ready in a peripheral device. In case forensic needs pop up, we can just plug in the USB, switch to Live (Forensic Mode) and get the job done smoothly.
from Linux Hint https://ift.tt/3ddtPaN






0 Comments