This feature is very useful for protocols supporting login authenticated connections such as ssh or ftp among others, preventing brute force attacks.
Getting started with UFW
To install UFW on Debian-based Linux distributions, run the command below.

ArchLinux users can get UFW from https://archlinux.org/packages/?name=ufw.
Once installed, enable UFW by running the following command.
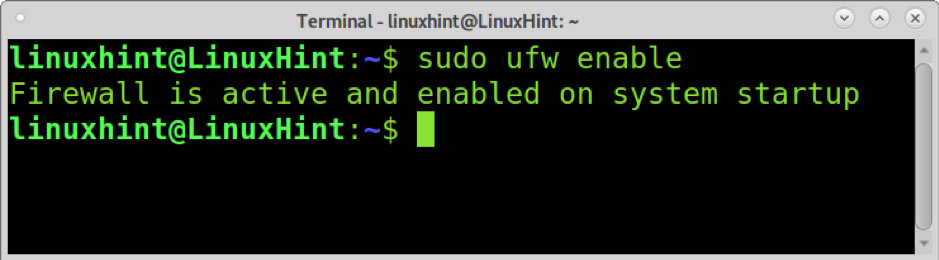
Note: you can disable UFW by running sudo ufw disable
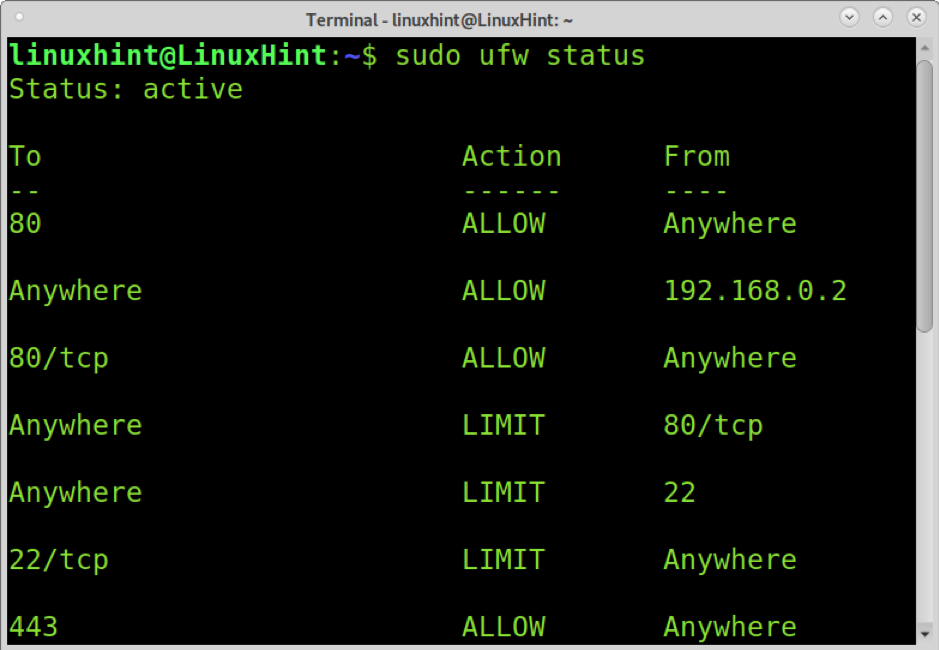
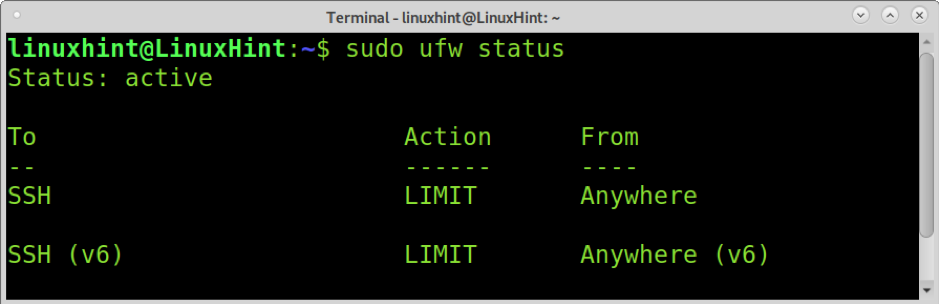
You can check UFW status by running the next example’s command. The Status will not only reveal if UFW is enabled, but it also prints source ports, destination ports, and the Action or rule to be executed by the firewall. The following screenshot shows some allowed and limited ports by Uncomplicated Firewall.
To reset UFW removing all Actions (rules), run the command below.

After a reset, running sudo ufw status again will show UFW is disabled.

To continue with this tutorial, enable it back.
Limiting ssh with UFW
As said previously, limiting a service using UFW will refuse connections from IP addresses that attempt to log in or connect more than 6 times in 30 seconds.
This UFW feature is very useful against brute force attacks.
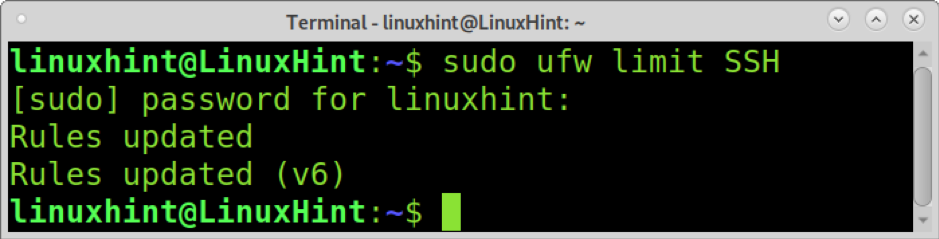
The syntax to limit a service using UFW is sudo ufw limit <service>.
To limit the ssh service, run the command below.
You can check if the service is limited by showing UFW status as shown previously and below.
The following example shows how to limit the FTP service in the same way.
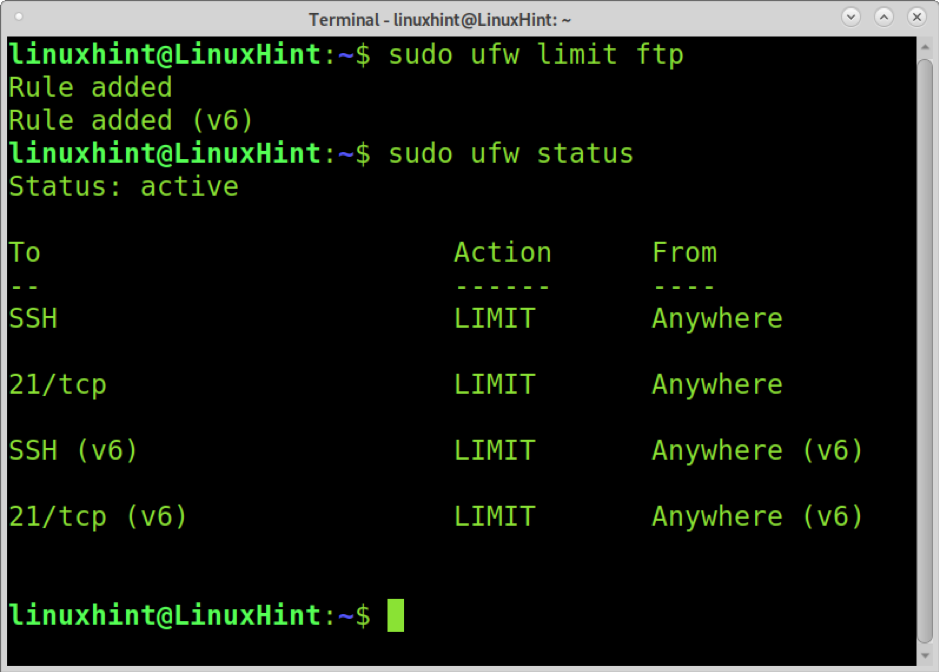
As you can see, both ftp and ssh are limited.
UFW is just an Iptables frontend. Rules behind our UFW commands are iptables or Netfilter rules from the kernel. The UFW rules described above are the following Iptables rules for ssh:
sudo iptables -A INPUT -p tcp --dport 2020 -m state --state NEW -m recent --set --name SSH
sudo iptables -A INPUT -p tcp --dport 22 -m state --state NEW -m recent --update --seconds 30 --hitcount 6 --rttl --name SSH -j DROP
How to limit ssh using UFW’s GUI (GUFW)
GUFW is the UFW (Uncomplicated Firewall) graphical interface. This tutorial section shows how to limit ssh using GUFW.
To install GUFW on Debian-based Linux distributions, including Ubuntu, run the following command.
Arch Linux users can get GUFW from https://archlinux.org/packages/?name=gufw.
Once installed, run GUFW with the command below.
A graphical window will show up. Press the Rules button next to the home icon.
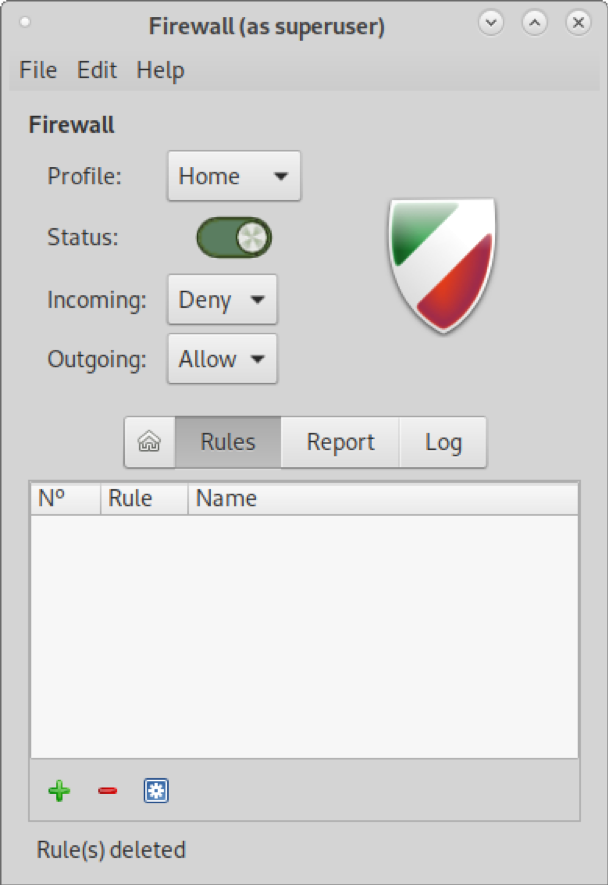
On the rules screen, press the + icon at the bottom of the window.
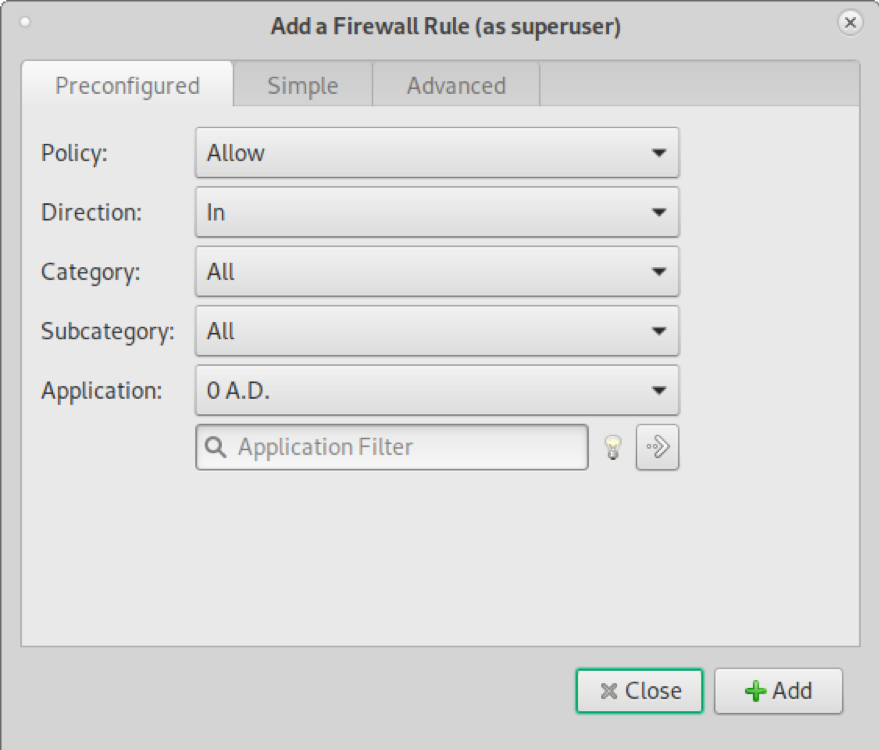
The window shown in the screenshot below will show up.
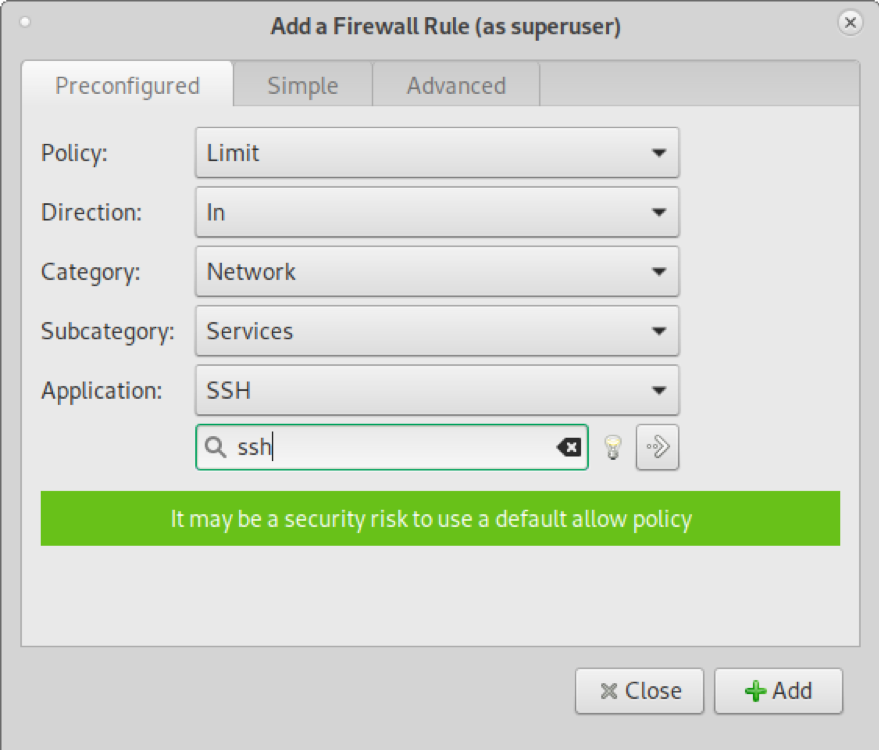
On the policy drop-down menu, select Limit. On Category, select Network. In the Subcategory dropdown menu, choose Services. In the Application Filter search box, type “ssh” as shown in the following screenshot. Then press the Add button.
As you can see, after adding the rule, you’ll see the rules added.

You can check rules were applied using UFW status.
To Action From
-- ------ ----
22/tcp LIMIT Anywhere
22/tcp (v6) LIMIT Anywhere (v6)
As you can see, the ssh service is limited both for IPv4 and IPv6 protocols.
Conclusion
As you can see, UFW is so simply applying rules through CLI becomes easier and a lot faster than using its GUI. Contrary to Iptables, any Linux user level can easily learn and implement rules to filter ports. Learning UFW is a nice way for new network users to get control of their network security and get knowledge on firewalls.
Applying the security measure explained in this tutorial is mandatory if your ssh service is enabled; almost all attacks against this protocol are brute force attacks which can be prevented by limiting the service.
You can learn additional ways to secure your ssh at Disabling root ssh on Debian.
I hope this tutorial explaining how to limit ssh using UFW was useful. Keep following Linux Hint for more Linux tips and tutorials.
from Linux Hint https://ift.tt/3ytLEwM




0 Comments