After reading this tutorial, you will know how to disable ssh password login enabling key authentication instead, increasing your system security. If you are looking for a way to disable the root login only, check this tutorial instead.
Disabling ssh password login:
The section of this tutorial about ssh focuses on the configuration file /etc/ssh/sshd_config, which like any other system configuration file, must be edited with root privileges.
Open the file /etc/ssh/sshd_config with root privileges. The command below can be used to open sshd_config using a nano text editor.
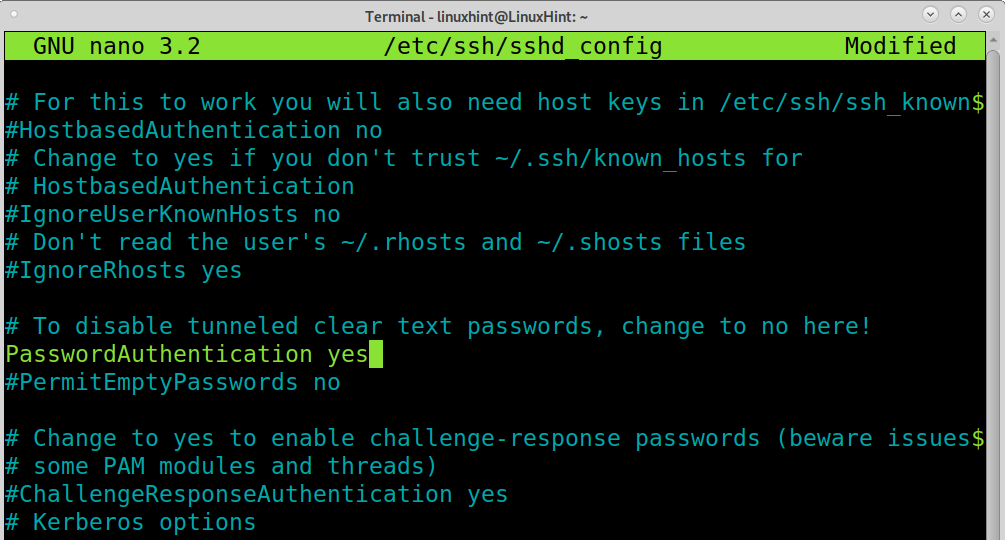
Scroll down the file and find the line containing “PasswordAuthentication yes” shown in the screenshot below. You can use the nano CTRL+W (Where) key combination to search the line containing “PasswordAuthentication”.
Edit the line leaving it as shown in the screenshot below, replacing yes with no.
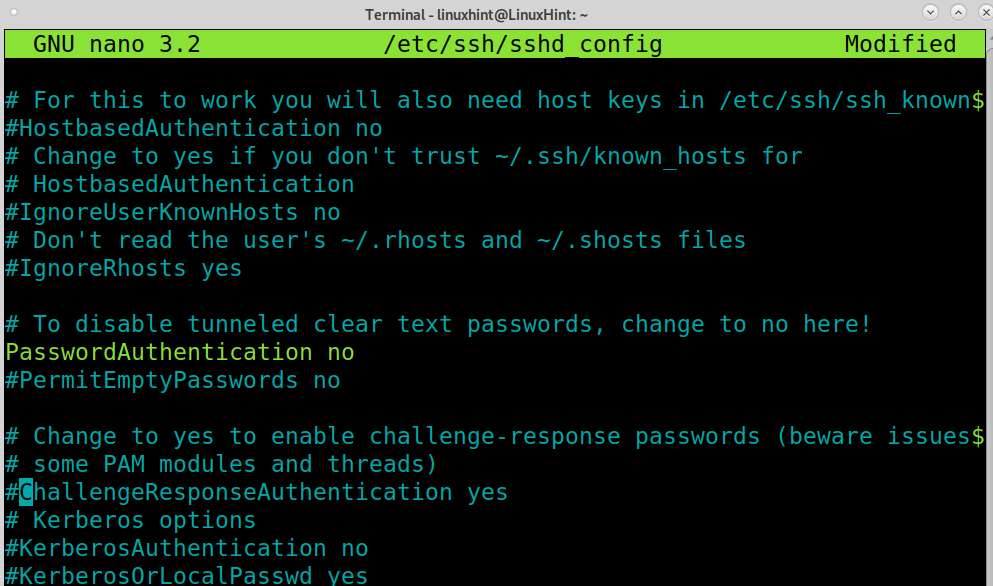
Now your ssh password login is configured to be disabled after you save the file and restart the ssh service. You can exit the file edition saving settings by pressing CTRL+X.
To restart the ssh service and apply changes, run the following command.
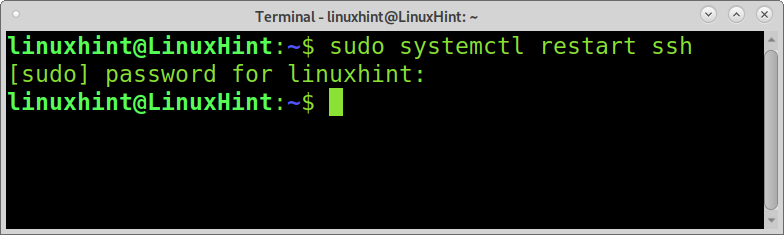
Now the password authentication is disabled for incoming ssh connections.
Note: If you only want to disable the password authentication method, you may probably prefer to delete the ssh service; if that’s what you want, there are instructions at the end of this section.
Enabling ssh key authentication:
Key authentication is different from the password authentication method. Depending on the environment, it has advantages and disadvantages over the default password login method.
When using key authentication, we talk about a technique including two different keys: a public key and a private key. In this case, the public key is stored in the server accepting logins; this public key can be decrypted only with the private key, stored in devices allowed to connect through ssh (clients).
Both public and private keys are generated simultaneously by the same device. In this tutorial, both public and private keys are generated by the client, and the public key is shared with the server. Before starting with this tutorial’s section, let’s numerate key authentication benefits over default password login.
Key authentication advantages:
- Strong generated key by default, stronger than most used human-made passwords
- The private key remains in the client; contrary to passwords, it can’t be sniffed
- Only devices storing the private key can connect (this can be considered a disadvantage too)
Password advantages over key authentication:
- You can connect from any device without a private key
- If the device is locally accessed, the password isn’t stored to be cracked
- Easier to distribute when allowing access to multiple accounts
To generate the public and private keys, login as the user you want to provide ssh access and generate the keys by running the command below.
After running ssh-keygen, you will be requested to type a passphrase to encrypt your private key. Most ssh accessible devices do not have a passphrase; you can leave it empty or type a passphrase encrypting your private key if it’s leaked.
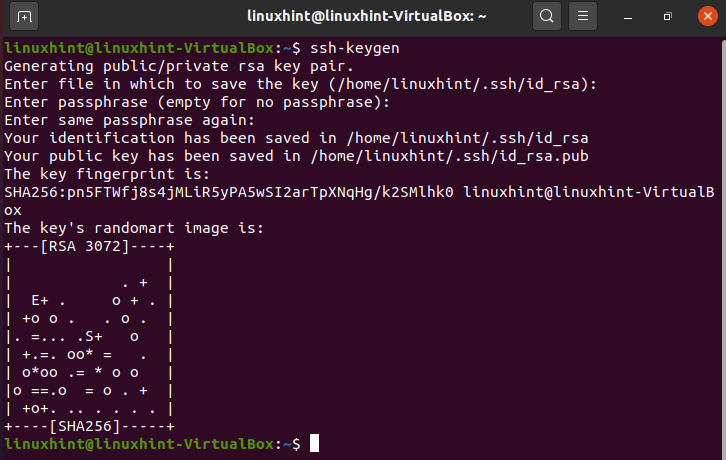
As you can see in the screenshot above, the private key is saved in the ~/.ssh/id_rsa file by default, located in the user’s home directory when creating the keys. The public key is stored in the file ~/.ssh/id_rsa.pub located in the same user directory.
Sharing or copying the public key to the server:
Now you have both public and private keys on your client device, and you need to transfer the public key to the server you want to connect to through key authentication.
You can copy the file in any way you prefer; this tutorial shows how to use the ssh-copy-id command to achieve it.
Once the keys are generated, run the command below, replacing linuxhint with your username and 192.168.1.103 with your server IP address, this will copy the generated public key to the server’s user ~/.ssh directory. You will be asked for the user password to save the public key, type it, and press ENTER.
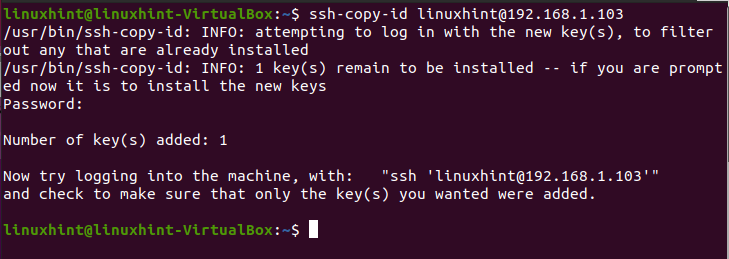
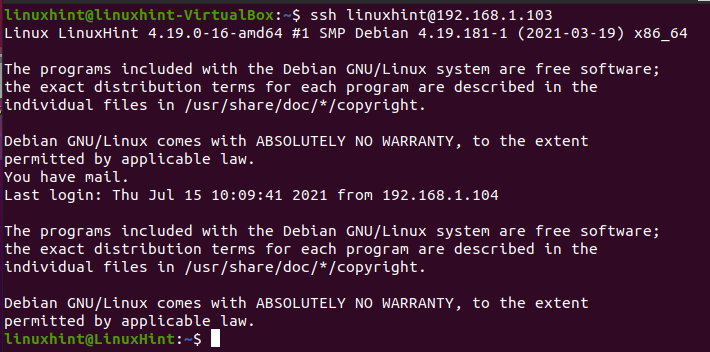
Once the public key was copied, you can connect to your server without a password by running the following command (replace username and password for yours).
Removing the ssh service:
Probably you want to remove the ssh at all; in such a case removing the service would be an option.
NOTE: After running the commands below on a remote system, you will lose ssh access.
To remove the ssh service, you can run the command below:
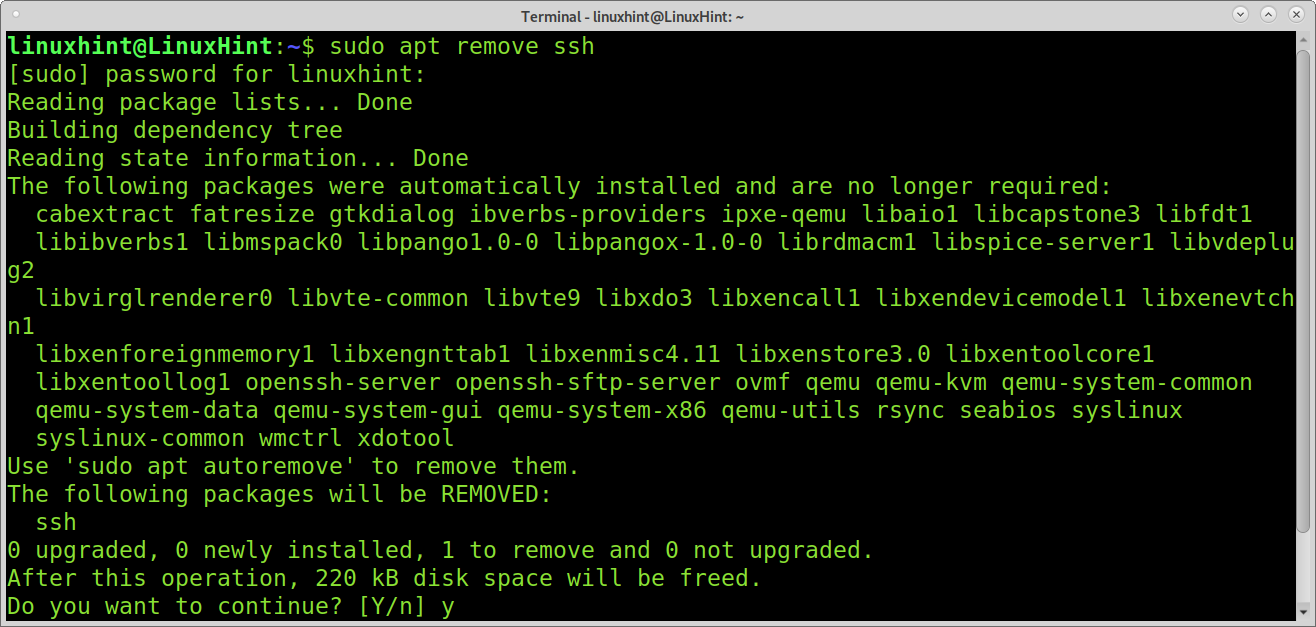
If you want to remove the ssh service, including configuration files run:
You can reinstall the ssh service by running:
Now your ssh service is back. Other methods to protect your ssh access may include changing the default ssh port, implementing firewall rules to filter the ssh port, and using TCP wrappers to filter clients.
Conclusion:
Depending on your physical environment and other factors like your security policy, the ssh key authentication method may be recommendable over password login. Since the password isn’t sent to the server to authenticate, this method is safer before Man in the Middle or sniffing attacks; it is also a great way to prevent ssh brute force attacks. The main problem of key authentication is the device must store the private key; it may be uncomfortable if you need to log in from new devices. On the other hand, this may be seen as a security advantage.
Additionally, administrators can use TCP wrappers, iptables, or UFW rules to define allowed or unallowed clients and change the default ssh port.
Some system administrators still prefer password authentication because it is faster to create and distribute between multiple users.
Users who never access the system through ssh may opt to remove this and all unused services.
I hope this tutorial showing how to disable password login in Linux was useful. Keep following Linux Hint for more Linux tips and tutorials.
from Linux Hint https://ift.tt/3zMpDK0




0 Comments