Often, Linux is regarded as one of the most secure platforms that’s reliable and high-performing. It comes with various tricks to offer a secure yet robust environment. One such feature is SELinux (Security-Enhanced Linux). It’s a kernel-level security architecture that enables system admin to have more control over who accesses the computer.
In the case of RHEL/CentOS, the SELinux feature is enabled by default. For security reasons, it’s recommended to keep in enabled. However, in certain situations, you may need to disable it. For example, not every app may function properly when SELinux is enabled. In such a case, you may want to disable SELinux.
Check out how to disable SELinux on CentOS.
Disabling SELinux
SELinux has an interesting origin history. It was first developed by the United States National Security Agency, also known as NSA as a patch to the Linux kernel using Linux Security Modules. It was released to the open-source community back in 2000. SELinux was integrated as a part of the Linux kernel starting from 2003.
There are two types of disabling SELinux. It’s possible to disable SELinux either temporarily or permanently. Depending on what your situation needs, follow the appropriate method. Note that the system is relatively more vulnerable when SELinux is disabled, so think twice before making the switch.
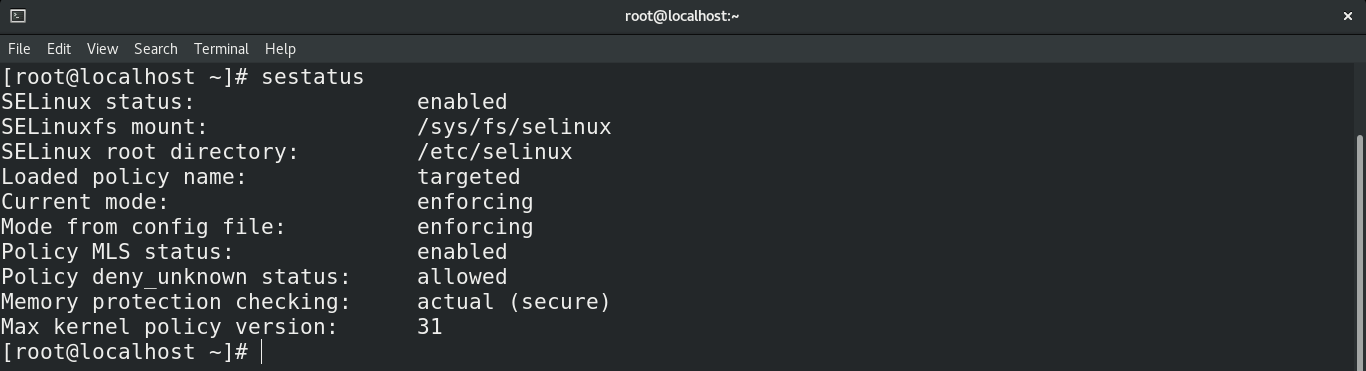
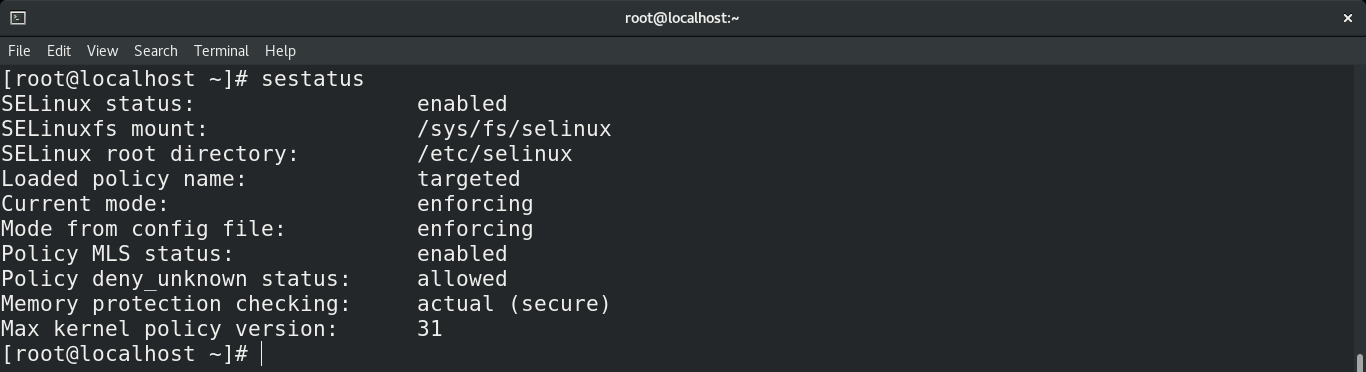
Checking SELinux status
First, check out the status of SELinux. Run the following command.
SELinux temporary disable
The following procedures will disable SELinux temporarily. Once the system boots, it’ll switch back to the default SELinux configuration.
The setenforce command is the default tool to set the SELinux status. If you set the SELinux mode using setenforce, then you don’t have to reboot the system. Run the following command to set SELinux to permissive.
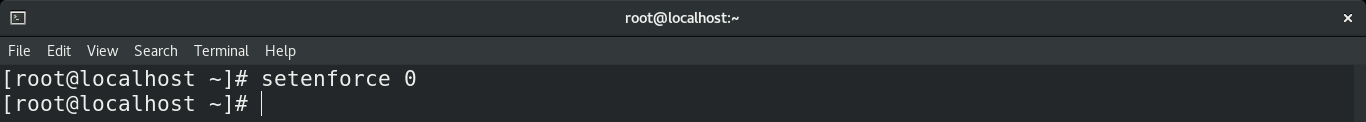
Instead of using the numerical value, you can also use the alternative term “Permissive”.

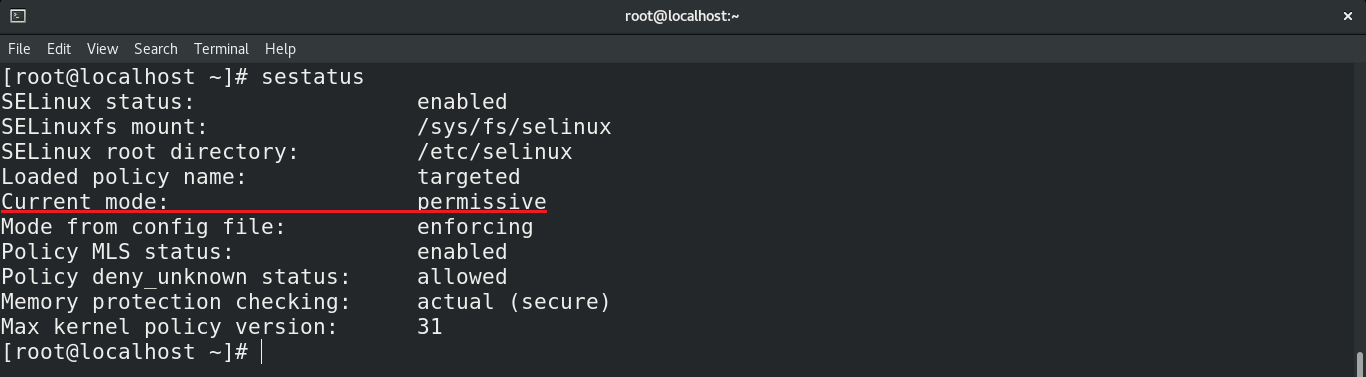
Check out the result of the setenforce command.
Another way is to manually edit the SELinux configuration file. Open the file in your favorite text editor. I’ll be opening it in Vim.
Change the value of “SELINUX” to permissive.
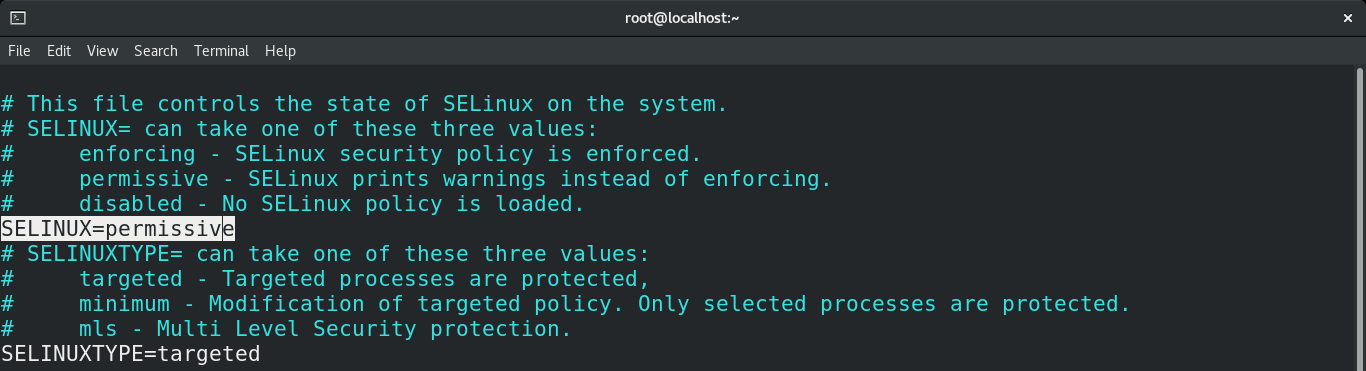
Save the file. You may want to reboot the system after making this change. Check the result of editing the configuration file.
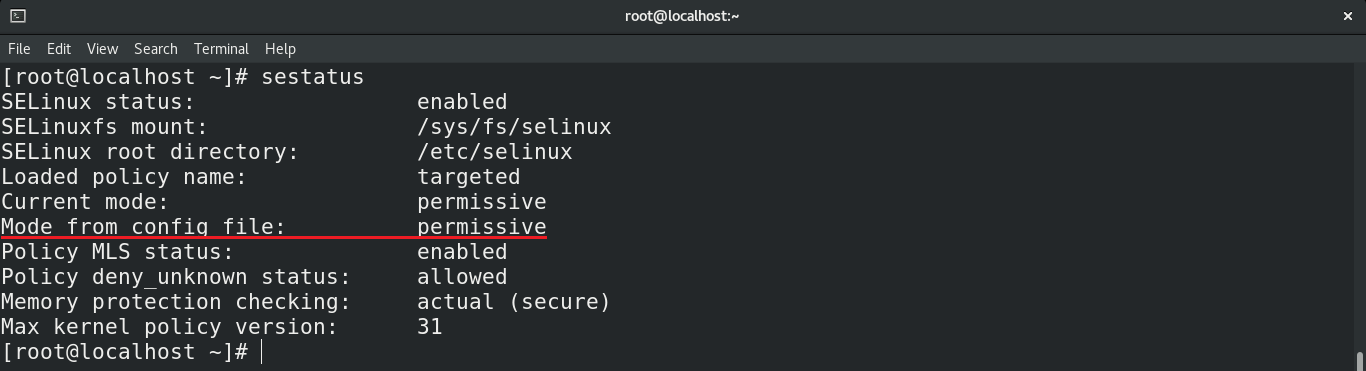
SELinux permanent disable
This method will permanently disable SELinux. To enable SELinux again, you have to manually revert back the changes performed in this method.
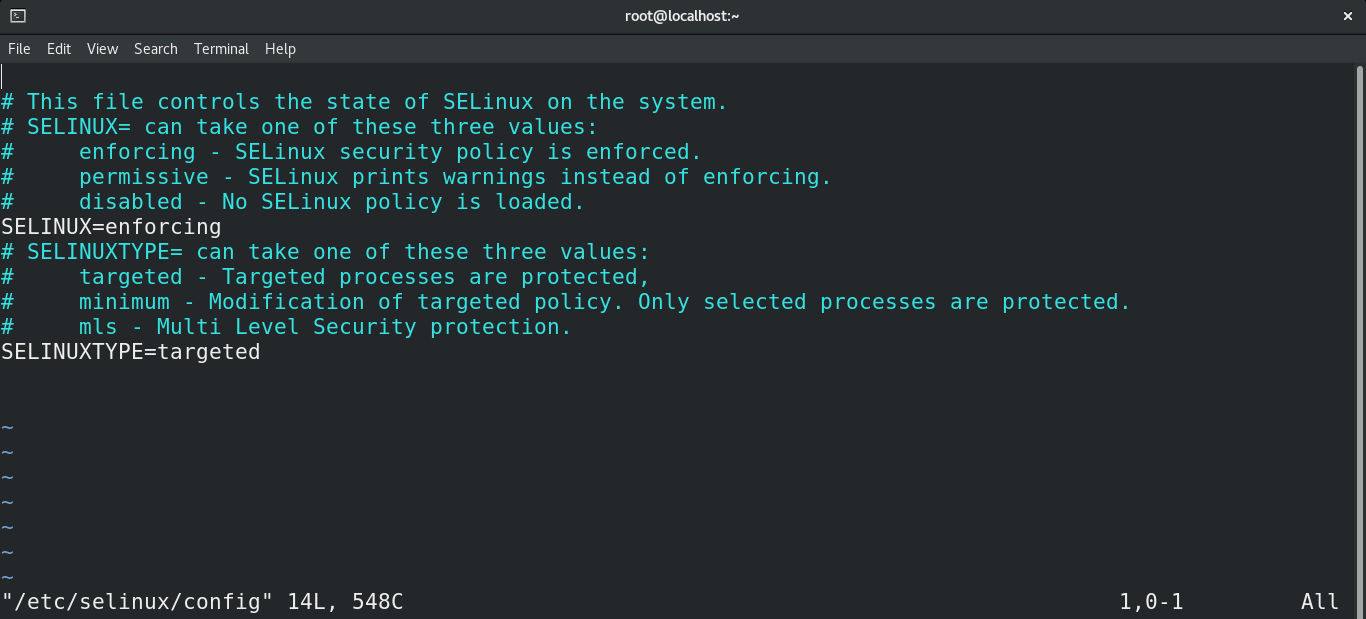
Open up the SELinux configuration file with your favorite text editor. In my case, I’ll be using Vim.
Here, the “SELINUX” variable determines the state of SELinux. As you can see, there are three possible Scroll down to the “SELINUX” variable and change its value to “disabled”.

Save the file and close the editor. The system needs a reboot to take the changes into effect. After rebooting, check out the SELinux status.

Enabling SELinux
Need to enable SELinux again? Depending on whichever method you followed, the way to enable SELinux will be different.
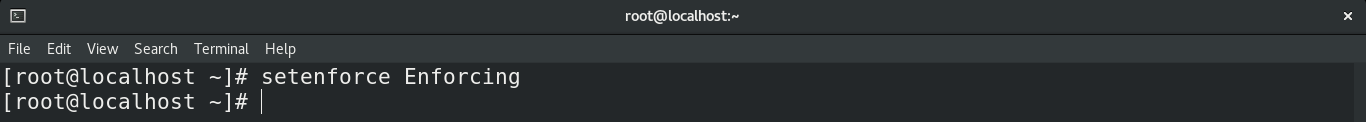
First, the temporary disable. If you used the setenforce command to disable SELinux, then a simple reboot of the system will bring the SELinux status back to default. If rebooting isn’t an option, then use the setenforce command again to manually re-assign the value.

As we’ve seen earlier, it’s also possible to use an alternative value with setenforce .
If you’ve manually edited the SELinux configuration file, then you have to revert it back manually. Open up the configuration file in a text editor.
Set the value of “SELINUX” back to “enforcing”. Then, save the file and reboot the system.
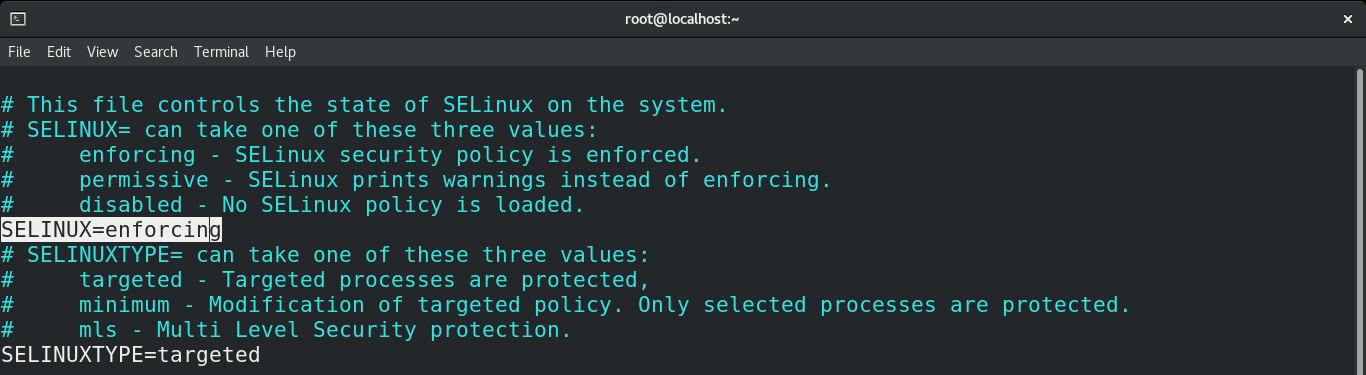
Check the SELinux status to verify the changes.
Final thought
Disabling SELinux is a very simple task. This method should also work with other distros that have SELinux support.
Interested in making your system more secure? Then check out the Linux security hardening checklist. It should act as a quick but useful introduction to the world of Linux security.
Happy computing!
from Linux Hint https://ift.tt/353DG1f




0 Comments