An Intrusion Detection System can be deployed depending upon the size of the network. There are dozens of quality commercial IDSs, but many companies and small businesses cannot afford them. Snort is a flexible, lightweight, and popular Intrusion Detection System that can be deployed according to the needs of the network, ranging from small to large networks, and provides all the features of a paid IDS. Snort does not cost anything but that does not mean that it cannot provide the same functionalities as an elite, commercial IDS. Snort is considered a passive IDS, which means it sniffs network packets, compares with the ruleset, and, in the case of detecting a malicious log or entry (i.e., detecting an intrusion), generates an alert or places an entry in a log file. Snort is used for monitoring the operations and activities of routers, firewalls, and servers. Snort provides a user-friendly interface, containing a chain of rulesets that can be very helpful to a person who is unfamiliar with IDSs. Snort generates an alarm in case of an intrusion (buffer overflow attacks, DNS poisoning, OS fingerprinting, port scans, and much more), giving an organization greater visibility of the network traffic and making it much easier to meet security regulations.
Installing Snort
Before you install Snort, there are some open-source softwares or packages that you should install first to get the best out of this program.
- Libpcap: A packet sniffer like Wireshark that is used to capture, monitor, and analyze network traffic. To install libpcap, use the following commands to download the packet from the official website, unzip the package, and then install it:
ubuntu@ubuntu:~$ tar -xzvf libpcap-<version number>
ubuntu@ubuntu:~$ cd libpcap-<version number>
ubuntu@ubuntu:~$ ./configure
ubuntu@ubuntu:~$ sudo make
ubuntu@ubuntu:~$ make install
- OpenSSH: A secure connectivity tool that provides a secure channel, even over an insecure network, to remotely log in via ssh protocol. OpenSSH is used to connect to systems remotely with admin privileges. OpenSSH can be installed using the following commands :
portable/openssh-8.3p1.tar.gz
ubuntu@ubuntu:~$ tar xzvf openssh-<version number>
ubuntu@ubuntu:~$ cd openssh-<version number>
ubuntu@ubuntu:~$ ./configure
ubuntu@ubuntu:~$ sudo make install
- MySQL: The most popular free and open-source SQL database. MySQL is used to store alerted data from Snort. SQL libraries are used by remote machines to communicate and access the database where Snort log entries are stored. MySQL can be installed using the following command:
- Apache Web Server: The most used web server on the internet. Apache is used to display the analysis console through the web server. It can be downloaded from the official website here: http://httpd.apache.org/, or by using the following command:
- PHP: PHP is a scripting language used in web development. A PHP parsing engine is required to run the Analysis console. It can be downloaded from the official website: https://www.php.net/downloads.php, or by using the following commands:
ubuntu@ubuntu:~$ tar -xvf php-<version number>.tar
ubuntu@ubuntu:~$ cd php-<version number>
ubuntu@ubuntu:~$ sudo make
ubuntu@ubuntu:~$ sudo make install
- OpenSSL: Used to secure communications over the network without worrying about third party fetching or monitoring the data sent and received. OpenSSL provides cryptographic functionality to the web server. It can be downloaded from the official website: https://www.openssl.org/.
- Stunnel: A program used to encrypt the arbitrary network traffic or connections inside the SSL and that works alongside OpenSSL. Stunnel can be downloaded from its official website: https://www.stunnel.org/, or it can be installed using the following commands:
ubuntu@ubuntu:~$ tar xzvf stunnel- <version number>
ubuntu@ubuntu:~$ cd stunnel- <version number>
ubuntu@ubuntu:~$ ./configure
ubuntu@ubuntu:~$ sudo make install
- ACID: An abbreviation for Analysis Control for Intrusion Detection. ACID is a query-supported search interface used to find matching IP addresses, patterns given, a specific command, a payload, signatures, specific ports, etc., from all logged alerts. It provides in-depth functionality of packet analysis, allowing identification of what exactly the attacker was trying to accomplish and the type of payload used in the attack. ACID can be downloaded from its official website: https://www.sei.cmu.edu/about/divisions/cert/index.cfm.
Now that all the required basic packages are installed, Snort can be downloaded from the official website, snort.org, and can be installed using the following commands:
ubuntu@ubuntu:~$ tar xvzf snort- <version number>
ubuntu@ubuntu:~$ cd snort- <version number>
ubuntu@ubuntu:~$ ./configure
ubuntu@ubuntu:~$ sudo make && --enable-source-fire
ubuntu@ubuntu:~$ sudo make install
Next, run the following command to check whether Snort is installed and the version of Snort you are using:
,,_ -*> Snort! <*-
o" )~ Version number ''''
Copyright (C) 1998-2013 Sourcefire, Inc., et al.
Using libpcap version 1.8.1
Using PCRE version: 8.39 2016-06-14
Using ZLIB version: 1.2.11
After the installation is successful, the following files should have been created on the system:
/usr/bin/snort: This is Snort’s binary executable.
/usr/share/doc/snort: Contains the Snort documentation and manpages.
/etc/snort: Contains all the rulesets of Snort and it is also its configuration file.
Using Snort
To use Snort, first, you must configure the Home_Net value and give it the value of the IP address of the network that you are protecting. The IP address of the network can be obtained using the following command:
From the results, copy the value of the inet address of the desired network. Now, open the Snort configuration file /etc/snort/snort.conf using the following command:
You will see an output like this:
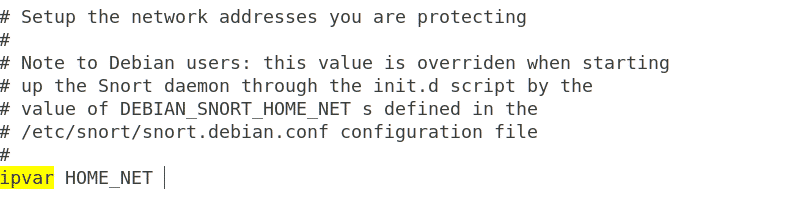
Find the line “ipvar HOME_NET.” In front of ipvar HOME_NET, write the IP address copied before and save the file. Before running Snort, another thing you must do is run the network in promiscuous mode. You can do so by using the following command:
Now, you are ready to run Snort. To check its status and test the configuration file, use the following command:
4150 Snort rules read
3476 detection rules
0 decoder rules
0 preprocessor rules
3476 Option Chains linked into 290 Chain Headers
0 Dynamic rules
+++++++++++++++++++++++++++++++++++++++++++++++++++
+-------------------[Rule Port Counts]---------------------------------------
| tcp udp icmp ip
| src 151 18 0 0
| dst 3306 126 0 0
| any 383 48 145 22
| nc 27 8 94 20
| s+d 12 5 0 0
+----------------------------------------------------------------------------
+-----------------------[detection-filter-config]------------------------------
| memory-cap : 1048576 bytes
+-----------------------[detection-filter-rules]-------------------------------
| none
-------------------------------------------------------------------------------
+-----------------------[rate-filter-config]-----------------------------------
| memory-cap : 1048576 bytes
+-----------------------[rate-filter-rules]------------------------------------
| none
-------------------------------------------------------------------------------
+-----------------------[event-filter-config]----------------------------------
| memory-cap : 1048576 bytes
+-----------------------[event-filter-global]----------------------------------
| none
+-----------------------[event-filter-local]-----------------------------------
| gen-id=1 sig-id=3273 type=Threshold tracking=src count=5 seconds=2
| gen-id=1 sig-id=2494 type=Both tracking=dst count=20 seconds=60
| gen-id=1 sig-id=3152 type=Threshold tracking=src count=5 seconds=2
| gen-id=1 sig-id=2923 type=Threshold tracking=dst count=10 seconds=60
| gen-id=1 sig-id=2496 type=Both tracking=dst count=20 seconds=60
| gen-id=1 sig-id=2275 type=Threshold tracking=dst count=5 seconds=60
| gen-id=1 sig-id=2495 type=Both tracking=dst count=20 seconds=60
| gen-id=1 sig-id=2523 type=Both tracking=dst count=10 seconds=10
| gen-id=1 sig-id=2924 type=Threshold tracking=dst count=10 seconds=60
| gen-id=1 sig-id=1991 type=Limit tracking=src count=1 seconds=60
+-----------------------[suppression]------------------------------------------
| none
-------------------------------------------------------------------------------
Rule application order: activation->dynamic->pass->drop->sdrop->reject->alert->log
Verifying Preprocessor Configurations!
[ Port Based Pattern Matching Memory ]
+- [ Aho-Corasick Summary ] -------------------------------------
| Storage Format : Full-Q
| Finite Automaton : DFA
| Alphabet Size : 256 Chars
| Sizeof State : Variable (1,2,4 bytes)
| Instances : 215
| 1 byte states : 204
| 2 byte states : 11
| 4 byte states : 0
| Characters : 64982
| States : 32135
| Transitions : 872051
| State Density : 10.6%
| Patterns : 5055
| Match States : 3855
| Memory (MB) : 17.00
| Patterns : 0.51
| Match Lists : 1.02
| DFA
| 1 byte states : 1.02
| 2 byte states : 14.05
| 4 byte states : 0.00
+----------------------------------------------------------------
[ Number of patterns truncated to 20 bytes: 1039 ]
pcap DAQ configured to passive.
Acquiring network traffic from "wlxcc79cfd6acfc".
--== Initialization Complete ==--
,,_ -*> Snort! <*-
o" )~ Version number
Copyright (C) 1998-2013 Sourcefire, Inc., et al.
Using libpcap version 1.8.1
Using PCRE version: 8.39 2016-06-14
Using ZLIB version: 1.2.11
Rules Engine: SF_SNORT_DETECTION_ENGINE Version 2.4 <Build 1>
Preprocessor Object: SF_IMAP Version 1.0 <Build 1>
Preprocessor Object: SF_FTPTELNET Version 1.2 <Build 13>
Preprocessor Object: SF_REPUTATION Version 1.1 <Build 1>
Preprocessor Object: SF_SDF Version 1.1 <Build 1>
Preprocessor Object: SF_SIP Version 1.1 <Build 1>
Preprocessor Object: SF_SSH Version 1.1 <Build 3>
Preprocessor Object: SF_GTP Version 1.1 <Build 1>
Preprocessor Object: SF_SSLPP Version 1.1 <Build 4>
Preprocessor Object: SF_DCERPC2 Version 1.0 <Build 3>
Preprocessor Object: SF_SMTP Version 1.1 <Build 9>
Preprocessor Object: SF_POP Version 1.0 <Build 1>
Preprocessor Object: SF_DNS Version 1.1 <Build 4>
Preprocessor Object: SF_DNP3 Version 1.1 <Build 1>
Preprocessor Object: SF_MODBUS Version 1.1 <Build 1>
Snort successfully validated the configuration!
Snort exiting
Snort Rulesets
The greatest power of Snort lies in its rulesets. Snort has the ability to employ a large number of rulesets to monitor network traffic. In its latest version, Snort comes with 73 different types and over 4150 rules for detecting anomalies, contained in the folder “/etc/snort/rules.”
You can look at the types of rulesets in Snort using the following command:
attack-responses.rules community-smtp.rules icmp.rules shellcode.rules
backdoor.rules community-sql-injection.rules imap.rules smtp.rules
bad-traffic.rules community-virus.rules info.rules snmp.rules
chat.rules community-web-attacks.rules local.rules sql.rules
community-bot.rules community-web-cgi.rules misc.rules telnet.rules
community-deleted.rules community-web-client.rules multimedia.rules tftp.rules
community-dos.rules community-web-dos.rules mysql.rules virus.rules
community-exploit.rules community-web-iis.rules netbios.rules web-attacks.rules
community-ftp.rules community-web-misc.rules nntp.rules web-cgi.rules
community-game.rules community-web-php.rules oracle.rules web-client.rules
community-icmp.rules ddos.rules other-ids.rules web-coldfusion.rules
community-imap.rules deleted.rules p2p.rules web-frontpage.rules
community-inappropriate.rules dns.rules policy.rules web-iis.rules
community-mail-client.rules dos.rules pop2.rules web-misc.rules
community-misc.rules experimental.rules pop3.rules web-php.rules
community-nntp.rules exploit.rules porn.rules x11.rules
community-oracle.rules finger.rules rpc.rules
community-policy.rules ftp.rules rservices.rules
community-sip.rules icmp-info.rules scan.rules
By default, when you run Snort in Intrusion Detection System mode, all these rules are deployed automatically. Let us now test the ICMP ruleset.
First, use the following command to run Snort in IDS mode:
-c /etc/snort/snort.conf


You will see several outputs on the screen, keep it that way.
Now, you will ping the IP of this machine from another machine using the following command:
Ping it five to six times, and then return to your machine to see if the Snort IDS detects it or not.
Needed and DF bit was set [**] [Classification: Misc activity] [Priority: 3]
{ICMP} <ip address of attacker’s mmachine> -> <this machine’s ip address>
08/24-01:21:55.178653 [**] [1:396:6] ICMP Destination Unreachable Fragmentation
Needed and DF bit was set [**] [Classification: Misc activity] [Priority: 3]
{ICMP} <ip address of attacker’s mmachine> -> <this machine’s ip address>
08/24-01:21:55.178653 [**] [1:396:6] ICMP Destination Unreachable Fragmentation
Needed and DF bit was set [**] [Classification: Misc activity] [Priority: 3]
{ICMP} <ip address of attacker’s mmachine> -> <this machine’s ip
address>
08/24-01:21:55.178653 [**] [1:396:6] ICMP Destination Unreachable Fragmentation
Needed and DF bit was set [**] [Classification: Misc activity] [Priority: 3]
{ICMP} <ip address of attacker’s mmachine> -> <this machine’s
ip address>
08/24-01:21:55.178653 [**] [1:396:6] ICMP Destination Unreachable Fragmentation
Needed and DF bit was set [**] [Classification: Misc activity] [Priority: 3]
{ICMP} <ip address of attacker’s mmachine> -> <this machine’s ip
address>
08/24-01:21:55.178653 [**] [1:396:6] ICMP Destination Unreachable Fragmentation
Needed and DF bit was set [**] [Classification: Misc activity] [Priority: 3]
{ICMP} <ip address of attacker’s mmachine> -> <this machine’s ip
address>
Here, we received an alert that someone is performing a ping scan. It even provided the IP address of the attacker’s machine.
Now, we will go to the IP address of this machine in the browser. We will see no alert, in this case. Try connecting to the ftp server of this machine using another machine as the attacker:
We still will not see any alert because these rulesets are not added in the default rules, and in these cases, no alert would be generated. This is when you must create your own rulesets. You can create rules according to your own needs and add them in the “/etc/snort/rules/local.rules” file, and then snort will automatically use these rules when detecting anomalies.
Creating a Rule
We will now create a rule for detecting a suspicious packet sent at port 80 so that a log alert is generated when this occurs:
There are two major parts of writing a rule, i.e., Rule Header and Rule Options. The following is a breakdown of the rule we have just written:
- Header
- Alert: The action specified to be taken on discovering the packet matching the rule’s description. There are several other actions that can be specified in place of the alert according to the user’s needs, i.e., log, reject, activate, drop, pass, etc.
- Tcp: Here, we have to specify the protocol. There are several types of protocols that can be specified, i.e., tcp, udp, icmp, etc., according to the user’s needs.
- Any: Here, the source network interface can be specified. If any is specified, Snort will check for all source networks.
- ->: The direction; in this case, it is set from source to destination.
- $HOME_NET: The place where the destination IP address is specified. In this case, we are using the one configured in the /etc/snort/snort.conf file at the beginning.
- 80: The destination port at which we are waiting for a network packet.
- Options:
- Msg: The alert to be generated or the message to be displayed in the case of capturing a packet. In this case, it is set to “HTTP Packet found.”
- sid: Used to identify Snort rules uniquely and systematically. The first 1000000 numbers are reserved, so you can start with 1000001.
- Rev: Used for easy rule maintenance.
We will add this rule in the “/etc/snort/rules/local.rules” file and see if it can detect HTTP requests on port 80.
found"; sid:10000001; rev:1;)” >> /etc/snort/rules/local.rules
We are all set. Now, you can open Snort in IDS mode using the following command:
-c /etc/snort/snort.conf
Navigate to the IP address of this machine from the browser.
Snort can now detect any packet sent to port 80 and will show the alert “HTTP Packet Found” on the screen if this occurs.
[Priority: 0] {TCP}<ip address>:52008 -> 35.222.85.5:80
08/24-03:35:22.979898 [**] [1:10000001:0] HTTP Packet found [**]
[Priority: 0] {TCP}<ip address>:52008 -> 35.222.85.5:80
08/24-03:35:22.979898 [**] [1:10000001:0] HTTP Packet found [**]
[Priority: 0] {TCP}<ip address>:52008 -> 35.222.85.5:80
08/24-03:35:22.979898 [**] [1:10000001:0] HTTP Packet found [**]
[Priority: 0] {TCP}<ip address>:52008 -> 35.222.85.5:80
08/24-03:35:22.979898 [**] [1:10000001:0] HTTP Packet found [**]
[Priority: 0] {TCP}<ip address>:52008 -> 35.222.85.5:80
08/24-03:35:22.979898 [**] [1:10000001:0] HTTP Packet found [**]
[Priority: 0] {TCP}<ip address>:52008 -> 35.222.85.5:80
08/24-03:35:22.979898 [**] [1:10000001:0] HTTP Packet found [**]
[Priority: 0] {TCP}<ip address>:52008 -> 35.222.85.5:80
We will also create a rule for detecting ftp login attempts:
Add this rule to the “local.rules” file using the following command:
(msg: "FTP packet found"; sid:10000002; rev:1;)” >> /etc/snort/rules/local.rules
Now, try logging in from another machine and take a look at the results of the Snort program.
{TCP}<ip address>:52008 -> 35.222.85.5:21
08/24-03:35:22.979898 [**] [1:10000002:0) FTP Packet found [**] [Priority: 0]
{TCP}<ip address>:52008 -> 35.222.85.5:21
08/24-03:35:22.979898 [**] [1:10000002:0) FTP Packet found [**] [Priority: 0]
{TCP}<ip address>:52008 -> 35.222.85.5:21
08/24-03:35:22.979898 [**] [1:10000002:0) FTP Packet found [**] [Priority: 0]
{TCP}<ip address>:52008 -> 35.222.85.5:21
08/24-03:35:22.979898 [**] [1:10000002:0) FTP Packet found [**] [Priority: 0]
{TCP}<ip address>:52008 -> 35.222.85.5:21
As seen above, we received the alert, which means that we have successfully created these rules for detecting anomalies on port 21 and port 80.
Conclusion
Intrusion Detection Systems like Snort are used for monitoring network traffic to detect when an attack is being carried out by a malicious user before it can hurt or affect the network. If an attacker is performing a port scan on a network, the attack can be detected, along with the number of attempts made, the attacker’s IP address, and other details. Snort is used to detect all types of anomalies, and it comes with a large number of rules already configured, along with the option for the user to write their own rules according to his or her needs. Depending on the size of the network, Snort can easily be set up and used without spending anything, as compared to other paid commercial Intrusion Detection Systems. The captured packets can be analyzed further using a packet sniffer, like Wireshark, to analyze and break down what was going in the mind of the attacker during the attack and the types of scans or commands performed. Snort is a free, open-source, and easy-to-configure tool, and it can be a great choice to protect any medium-sized network from attack.
from Linux Hint https://ift.tt/33tasGS




0 Comments