dnsenum Package
It is a multithreaded Perl script that helps to itemize the DNS information of the domain. It also helps to discover the IP blocks, especially those that are non-contiguous. It includes the following basic operations:
- Acquire the address of the host.
- Obtaining the name servers.
- Acquire the record of MX.
- Obtain the bind version, carry out axfr queries on the name servers.
- Now get the subdomains and extra names with the help of google scraping.
- The file with the subdomain brute force will also perform recursion on subdomains that are having the NS records.
- Now calculate C class of domain network range and carry out queries on them.
- Then perform the reverse lookups on the net ranges.
- Write the domain_ips.txt file for ip-blocks.
dnsmap Package
dnsmap was initially released in the year 2006 due to the inspiration of the fictional story of Paul Craig known as “the thief no one saw”. This can be available in the book named “Stealing the network-how to own the box”. The dnsmap helps the pentester in the process of gathering information for the security assessments. In this phase, the IP net-blocks, contact numbers, etc. of the targeted company are discovered by the security consultant. There is another technique which is called the brute-forcing of the subdomain, and it is helpful in the enumeration phase, especially when the rest of the methods like zone transfers do not work.
Fierce Package
Let us see what is not fierce. It is not a tool of DDoS, neither it is designed for scanning the entire internet and carry out the untargeted attacks. Also, it is not an IP scanner. The main purpose is to locate the targets, especially the inside and outsides network. Within a few minutes, fierce quickly scan the domains with the help of several tactics as fierce is a Perl script. Fierce does not carry out the exploitations; rather, someone did intentionally with the –connect switch.
DNS (Domain Name System)
DNS stands for the domain name system, and it is similar to the telephone directory that includes several names, addresses, and names. DNS is used for the internal as well as the external networks of the organizations. Hostnames of IP addresses are resolved by using the DNS protocol. Every computer has a host file that is located in the following directory when there was no DNS. C: \Windows\System32\drivers\etc.
Now let you see the DNS records for the following domains:
- Enumeration of DNS and zone transfer with the help of dnsenum
- Carry out the analysis of DNS with the help of Host utility
- Searching the subdomains using dnsmap
- Interrogation of DNS by the use of Fierce
Enumeration of DNS and zone transfer with the help of dnsenum
Dnsenum is a simple tool. The use of this tool is very easy as it resolves and enumerates the information of DNS for the particular target. Furthermore, it automatically carries out the zone transfers of the DNS with the help of the nameserver details. Let us see the detail:
In the first step, open the window of the new terminal. Then execute the following command: dnsenum. After doing this, it will show the help menu having a detailed description of the different operators and the way to use it.
By accessing the information that is quite sensitive, like what we have found, will lead to the network information for the particular target organization.
Then the following command is used to carry out the DNS enumeration on the domain zonetransfer.me. This is shown below:
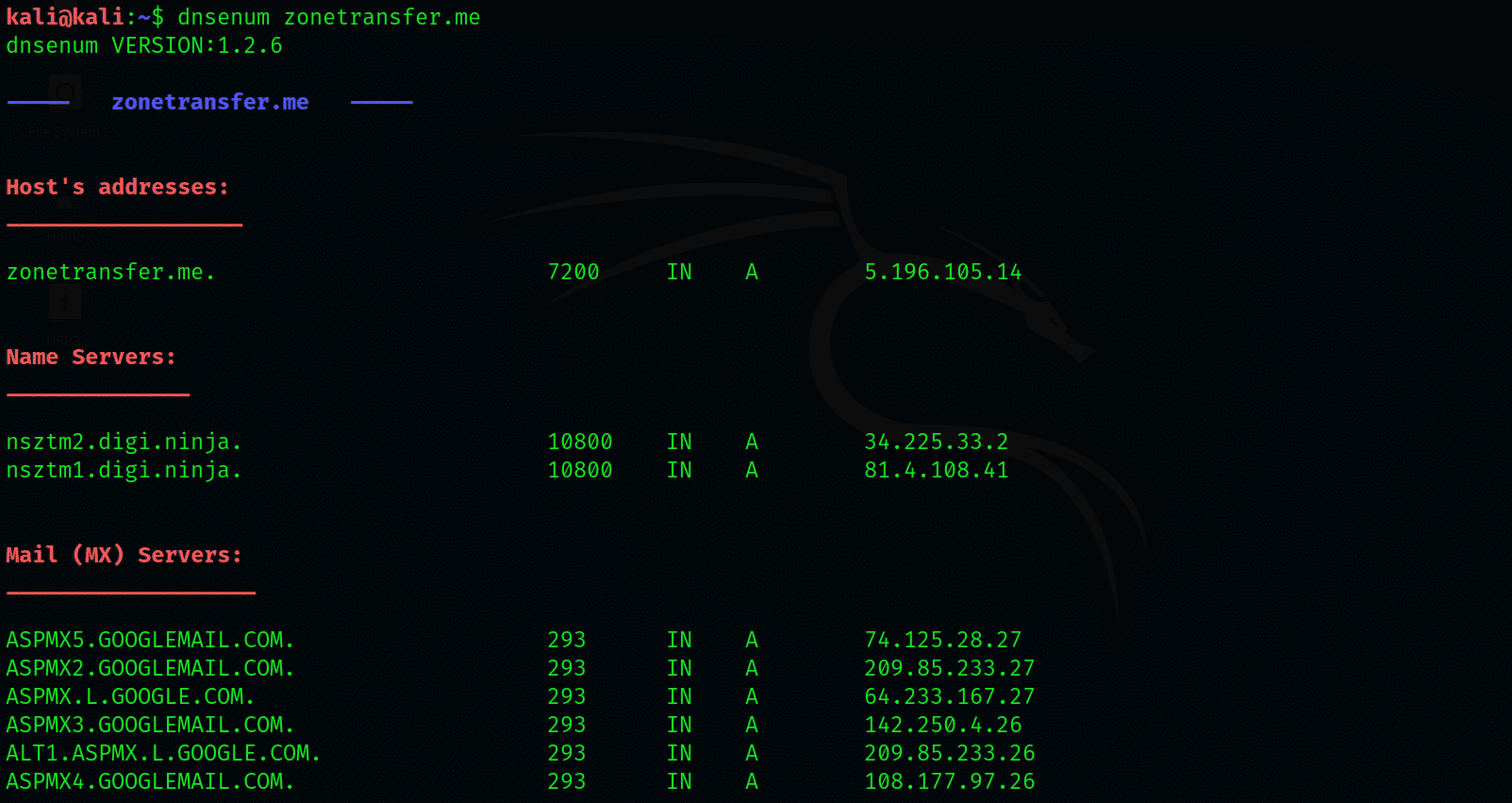
In the third step, DNS zone transfer is performed by dnsenum by using the nameservers that are obtained in the process of enumeration. The details of which are given below:
Carry out the analysis of DNS with the help of Host utility
The host utility is beneficial as it is quite inherent to the Linux operating system. By the use of this, we can obtain a lot of DNS information regarding the target domain. Let us see how it works:
In the first step, open the new terminal in the Kali Linux. Then execute the following command:
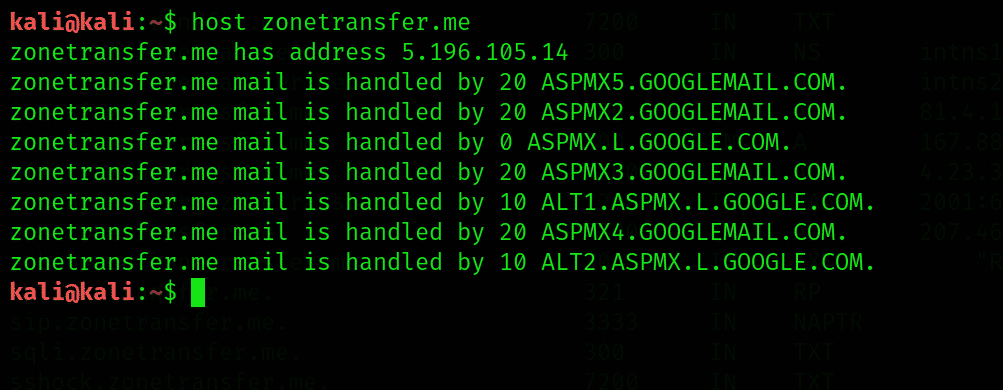
Here we will notice that the host tool will get the records of DNS like A and MX domain records.
Next, use the following command:
![]()
For enumeration to get the name servers of the domain. Here the –t operator helps to specify the records of DNS.
After getting the nameservers of a particular domain, we will use the gathered information. Now we will perform the DNS zone transfer for the domain by querying the nameservers with the help of the following command:
![]()
Searching the subdomains using dnsmap
Dnsmap works differently by enumerating the subdomains of the particular domain of organization and then query it on the kali Linus operating system as a built-in wordlist. The dnsamp will resolve the IP address as soon as the subdomain is found. With the help of the following command, we can find the subdomains of various organizations with their Ip addresses, as shown below:
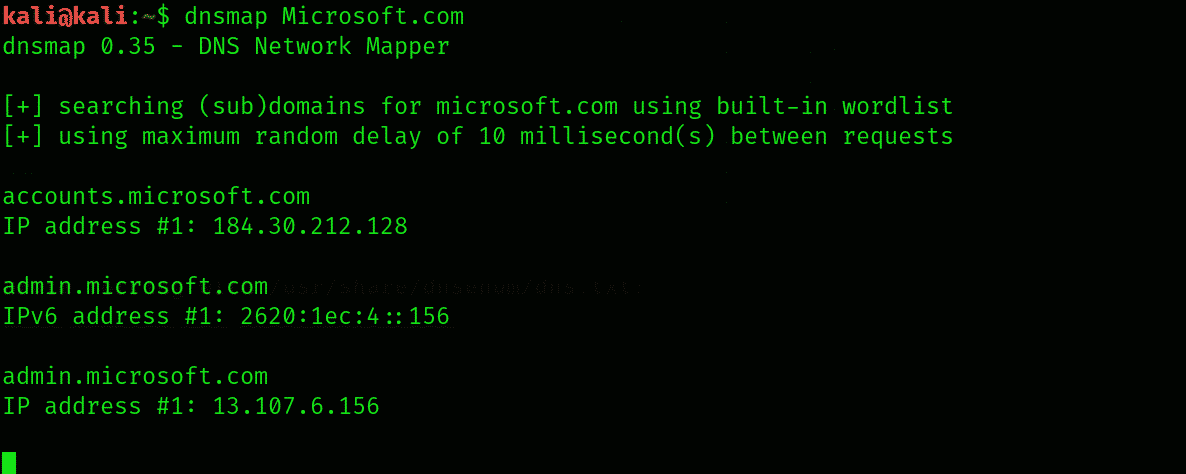
To find the hidden sensitive portal and directories, it is necessary to discover the subdomains of a particular organization.
Interrogation of DNS by the use of Fierce
Fierce is a DNS interrogation tool. It is taken as a semi light-weighted tool that performs the huge lookups for target domain having hostnames and IP spaces. The following command is used to execute it, as shown below:
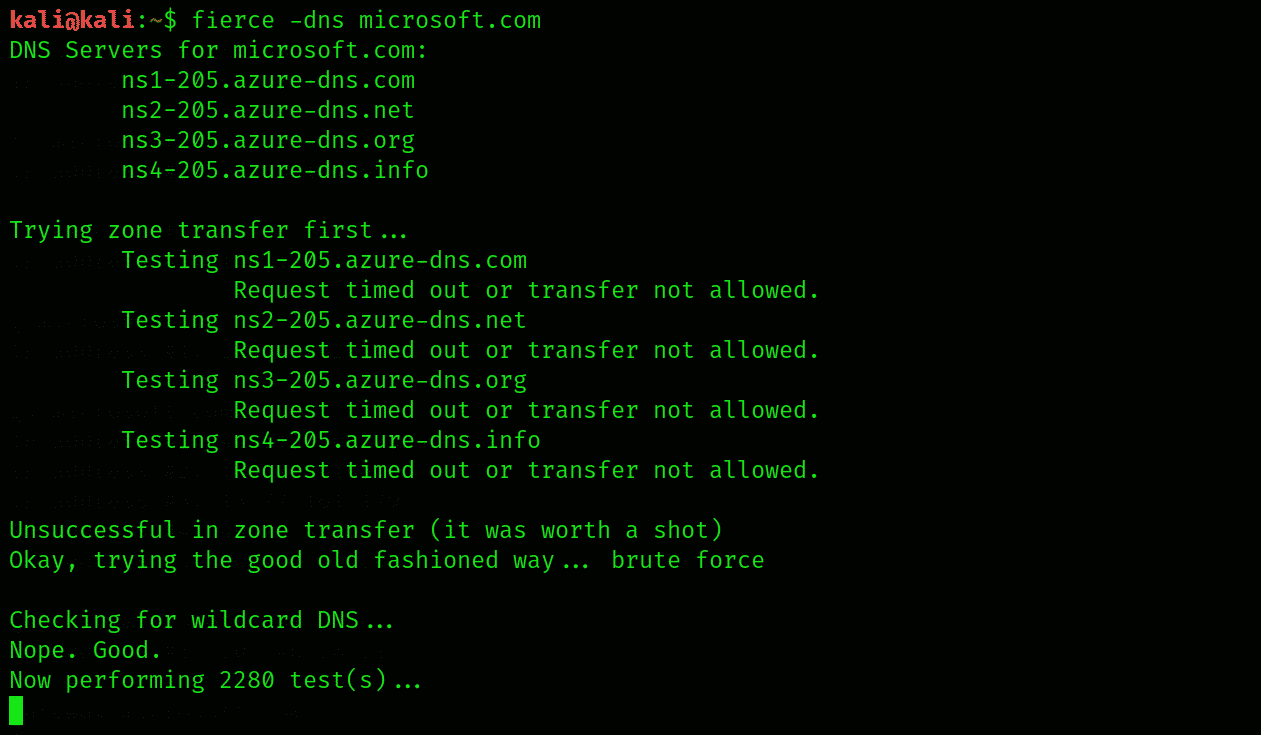
Fierce will get all the records of DNS and also discover the subdomains using their IP addresses of the particular domain. For the in-depth analysis of the target domain, this tool will take the extra time to complete the process.
Conclusion:
In this tutorial, I have shown you what DNS is and how the dnsenum tool in Kali Linux works. I have also shown you how to work on the Fierce tool and get all DNS records.
from Linux Hint https://ift.tt/2CQjrc9




0 Comments