This tutorial explains how to execute the Xmas stealth scan technique using Nmap.
Nmap Xmas scan was considered a stealthy scan that analyzes responses to Xmas packets to determine the nature of the replying device.
Each operating system or network device replies in a different way to Xmas packets revealing local information, such as OS (Operating System), port state, and more.
Currently, many firewalls and Intrusion Detection Systems can detect Xmas packets, and it is not the best technique to carry out a stealth scan. Yet it is extremely useful to understand how it works.
After reading this tutorial, the user will understand how Xmas, NULL, and FIN scans work. All instructions below contain screenshots, making it easy for readers to understand how Nmap commands are executed.
About the Xmas Scan
Most firewalls are what are known as stateful firewalls. They have the capability to analyze packets on the fly, contrary to the stateless firewall, which only compares defined matching rules.
Normally stateless firewalls block SYN bits or headers from TCP packets when sent without ACK bits. The Xmas scan consists of clearing the SYN header from the TCP packet and replacing it with FIN, PSH, and URG bits (Or headers), bypassing the firewall.
In other words, TCP packet headers matching firewall rules are replaced with headers not matching rules.
The Xmas scan is an old stealth scan technique, but currently not reliable, detected by most firewalls and anti-intrusion measures. Yet, it is reproducible and highly educational to learn about the TCP structure.
In previous articles like our Nmap basics tutorial, Nmap six possible port states were described.
When we refer to the Xmas scan, there are only three possible port states:
- Open|filtered: Nmap can’t detect if the port is open or filtered. Even if the port is open, the Xmas scan will report it as open|filtered. It happens when no response is received (even after retransmissions).
- Closed: Nmap detects the port is closed; it happens when the response is a TCP RST packet.
- Filtered: Nmap detects a firewall filtering the scanned ports; it happens when the response is ICMP unreachable error (type 3, code 1, 2, 3, 9, 10, or 13). Based on the RFC standards Nmap or the Xmas scan is capable of interpreting the port state.
As can be understood from the previous list, the Xmas scan, just like NULL and FIN scans, can’t distinguish between open and filtered ports.
If the target does not expressly refuse the connection and just drops the packet without replying, without a rejection reply, the Xmas scan can’t be sure if the port is open or filtered.
When there is no apparent response from a firewall, ports may be defined as open|filtered.
The user can implement invasive flags to differentiate between open and filtered ports, but there is no sense in combining them with a stealth scan like Xmas.
Note: Today, in practice, all targets are likely to be detected as closed or filtered by the outdated Xmas technique.
Executing a Xmas Scan With Nmap
The syntax to execute a Xmas scan with Nmap is the following where the -sX flag instructs Nmap to launch a Xmas scan, -T controls the timing template (Explained below), and -v instructs verbosity.
The practical example below shows a Xmas scan against the router 192.168.0.1.
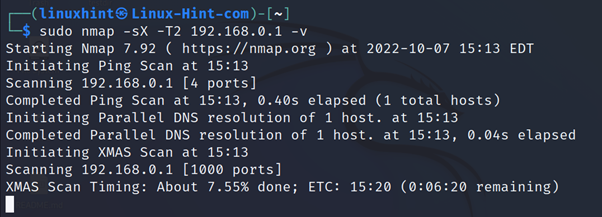
Timing templates (-T) define the aggressivity level, ranging from the slowest to the fastest scan types.
Timing Templates
| TEMPLATE | FLAG | FUNCTIONS |
| Paranoid | -T0 | Extremely slow, useful to bypass IDS |
| Sneaky | -T1 | Slow, also useful to bypass IDS (Intrusion Detection Systems) |
| Polite | -T2 | Neutral |
| Normal | -T3 | Default mode |
| Aggressive | -T4 | Fast scan |
| Insane | -T5 | Faster |
NULL and FIN Scans With Nmap
NULL and FIN scan types apply the same technique and are also useful against stateless firewalls.
While the Xmas scan clears the SYN flag or bit from the TCP packet and replaces it with FIN, PSH, and URG headers or flags, the NULL scan clears the SYN bit or header without replacing it. It only removes the SYN bit (Blocked by firewalls) from the TCP packet.
The FIN scan clears the SYN header and uses a FIN one.
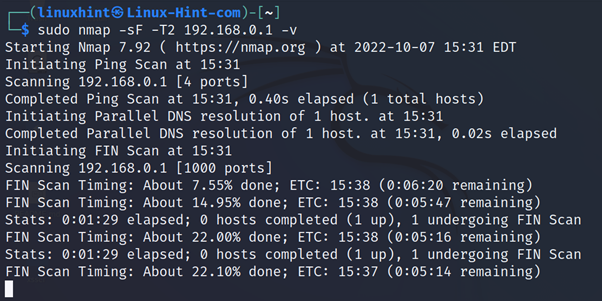
The following syntax belongs to a FIN scan specified with the -sF flag. Where <Template> must be replaced with one of the levels described in the previous table and <Target> with the actual target:
In the practical example below, the user launches a FIN scan against the host 192.168.0.1:
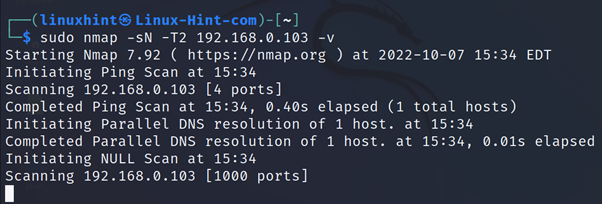
In the next example, the NULL scan is instructed with the -sN flag.
All these techniques exploited the same RFC rule to learn a port state according to the reply.
The SYN Stealth Scan
Other stealth scan techniques, like SYN scans, interrupt the communication before it gets established, preventing firewalls from logging the interaction or reacting before a scan.
The SYN scan, another stealthy scan method, is implemented with the -sS flag, as shown below:
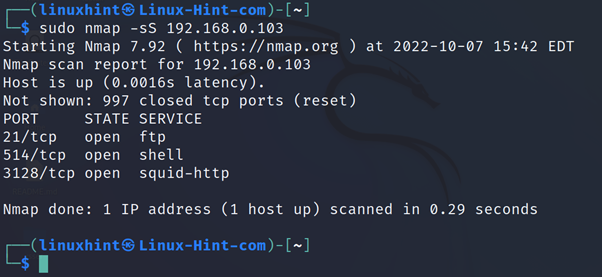
This scan type is deeply explained in our article Nmap Stealth Scan.
FIN, PSH, and URG Bits
Xmas and FIN scans use the following bits:
- PSH: TCP buffers allow data transference when you send more than a segment with the maximum size. If the buffer isn’t full, the flag PSH (PUSH) allows it to send it anyway by filling the header or instructing TCP to send packets. Through this flag, the application generating traffic informs the data must be sent immediately, and the destination is informed data must be sent immediately to the application.
- URG: This flag informs specific segments are urgent and must be prioritized. When the flag is enabled, the receiver will read a 16 bits segment in the header. This segment indicates the urgent data from the first byte. Currently, this flag is almost unused.
- FIN: RST packets were explained in the tutorial mentioned above (Nmap Stealth Scan). Contrary to RST packets, FIN packets, rather than informing on connection termination, requests it from the interacting host and wait until getting a confirmation to terminate the connection.
Iptables Rules Against Xmas Scans
Right today, all firewalls are protected against Xmas, NULL, and FIN scans. But firewall rules against such activity are helpful in understanding how packets are approached by firewalls.
iptables -A INPUT -p tcp --tcp-flags ALL ALL -j DROP
iptables -A INPUT -p tcp --tcp-flags ALL NONE -j DROP
iptables -A INPUT -p tcp --tcp-flags SYN,RST SYN,RST -j DROP
Conclusion
While the Xmas scan isn’t new, and most defense systems are capable of detecting it, becoming an obsolete technique against well-protected targets, it is a great way of introducing uncommon TCP segments like PSH and URG and understanding the way in which Nmap analyzes packets to get conclusions on targets.
More than an attack method, this scan is useful to test your firewall or Intrusion Detection System. The iptables rules previously mentioned should be enough to stop such attacks from remote hosts. This scan is very similar to NULL and FIN scans both in the way in which they work and low effectivity against protected targets.
As you can see, Xmas scans can be launched by any user independently of the knowledge level. Understanding them is pretty easy for anyone introduced to networking. Yet it is likely to fail as every exploit for any ancient security hole.
I hope you found this article useful in understanding Xmas scans with Nmap. Keep following Linux Hint for more tips and updates on Linux, networking, and security.
from https://ift.tt/MFJzSN3




0 Comments