After reading this tutorial, you will know how to find and read UFW logs. For a complete UFW tutorial, you can read Working with Debian Firewalls (UFW).
To begin, you can enable UFW with the status verbose option to check if logging is enabled or disabled. Run the command below:
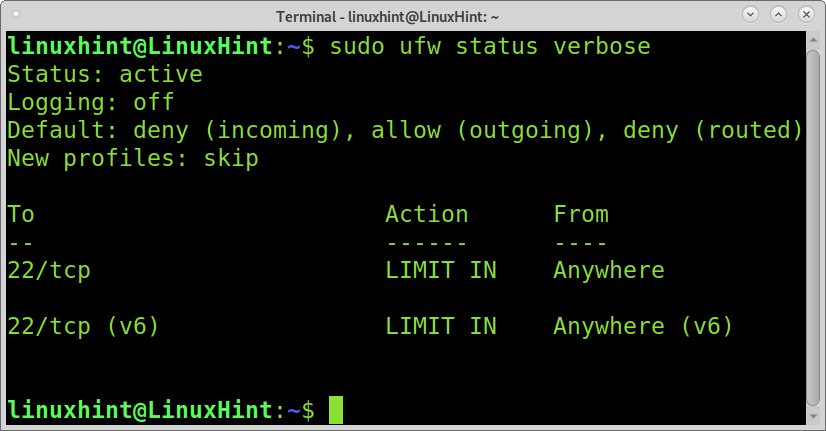
As you can see, logging is disabled (off). To enable logging on UFW, run the command below:
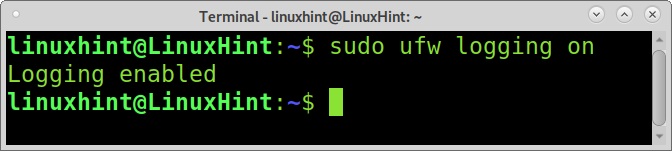
As you can see, logging has been enabled.
If you want to recheck it, run the ufw status verbose again as shown below:
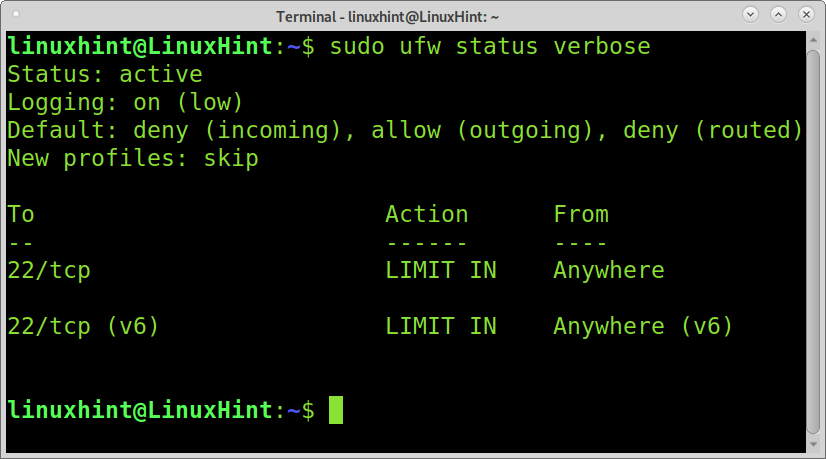
As you can see, logging is enabled, and between parentheses, you can read (low). This is because there are five different logging levels:
- Off: No managed logging.
- On (low): Logs all blocked or allowed packets by defined policies.
- On (medium): Same as above, and additionally, it includes packets not matching policies.
- On (High): Logs all rate-limiting and without rate limiting.
- On (Full): Logs all packets without rate limiting.
For example, if you want to change the logging level to medium, you can run the command below.
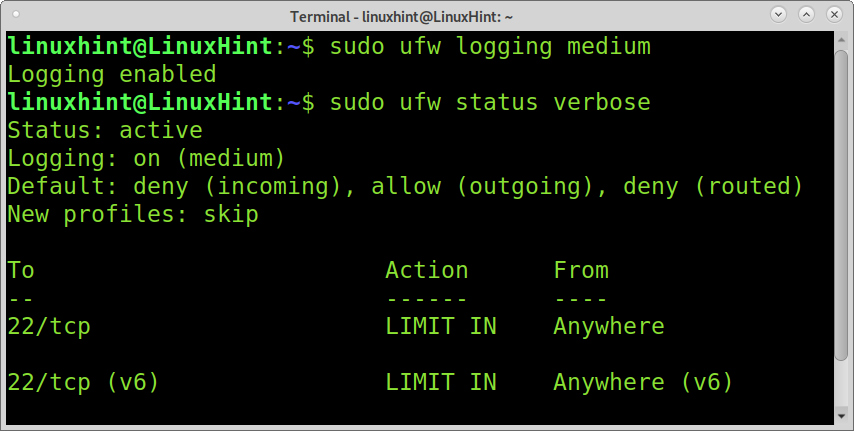
Note: In the command above, replace medium with another value for a different logging level.
Usually, logs are stored under the /var/log/ directory, and UFW isn’t the exception. To see UFW available logs, you can use the ls command and a to implement a wildcard, as shown in the following example.
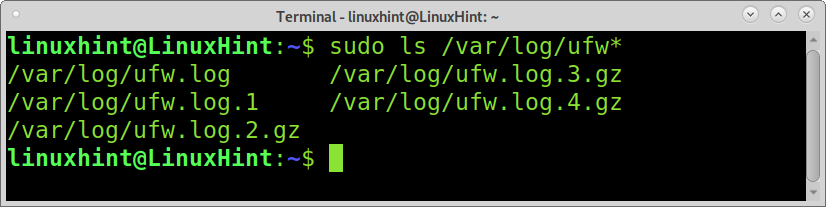
As you can see, there are several UFW Logs. Let’s see how to read and interpret them.
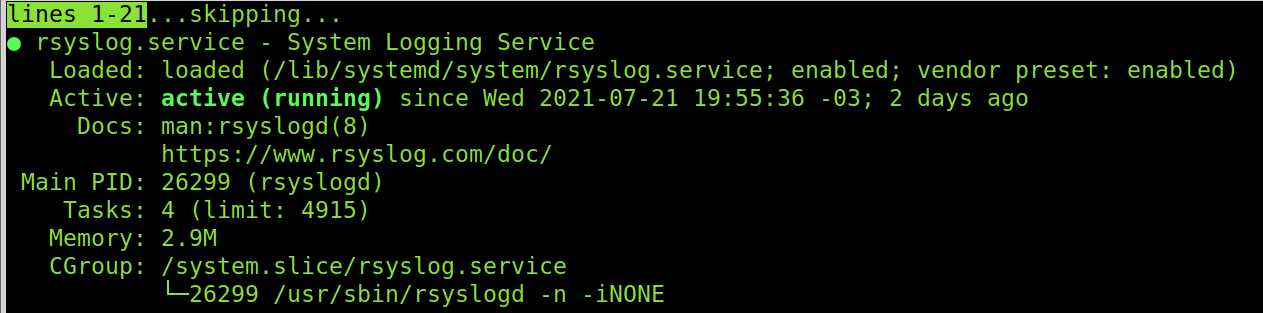
Note: for UFW logging to work, rsyslog must be enabled. You can check it by running the command below:
To simply read all logs without parameters, you can run:
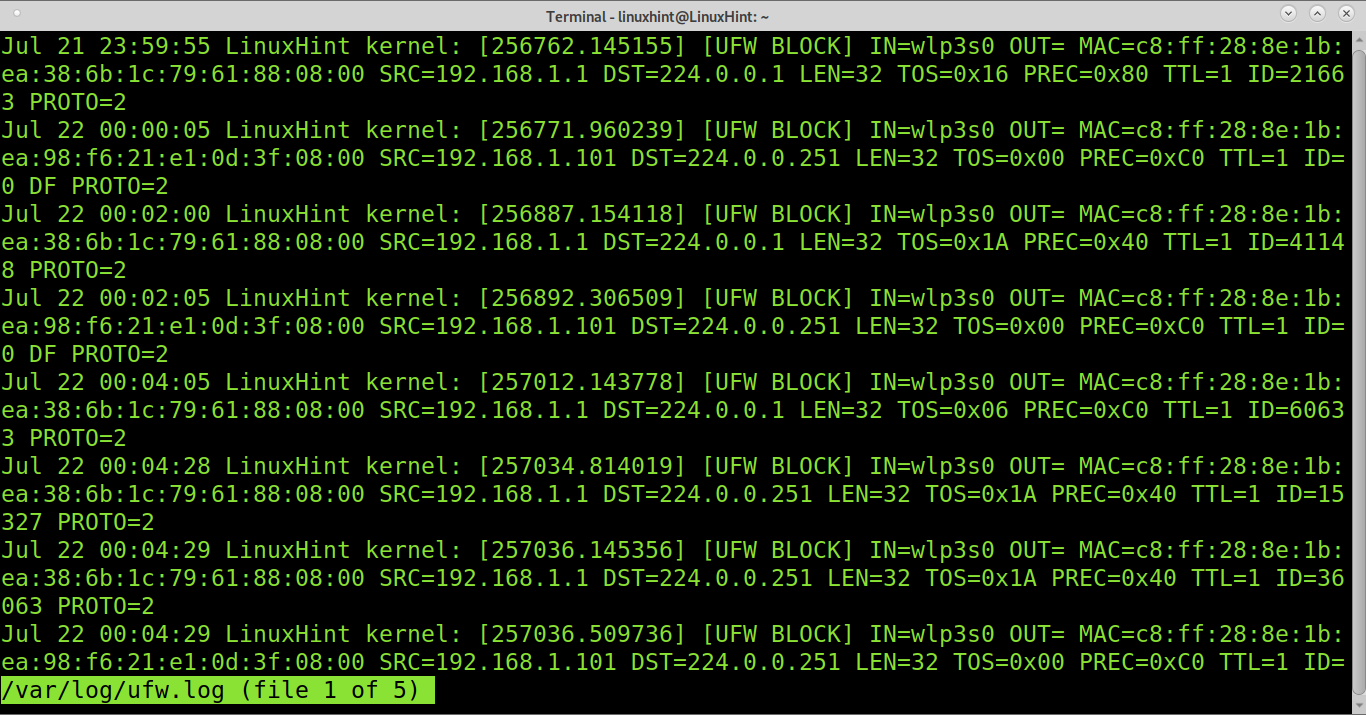
As you can see, there are many fields, and the following list provides each field’s meaning.
- IN= This field shows the device for incoming traffic.
- OUT= This field shows the device for outgoing traffic.
- MAC= This field shows the device’s MAC address.
- SRC= This field displays a connection source IP address.
- DST= Displays the destination IP address of a connection.
- LEN= This field shows the packet’s length.
- TOS= (Type of Service) This field is used for packet classification, and it is deprecated.
- PREC= This field shows the Precedence Type of Service.
- TTL= This field shows Time To Live.
- ID= This field shows a unique ID for the IP datagram, which is shared by fragments of the same packet.
- PROTO= This field shows the used protocol.
To read the last log entries, run the following command:
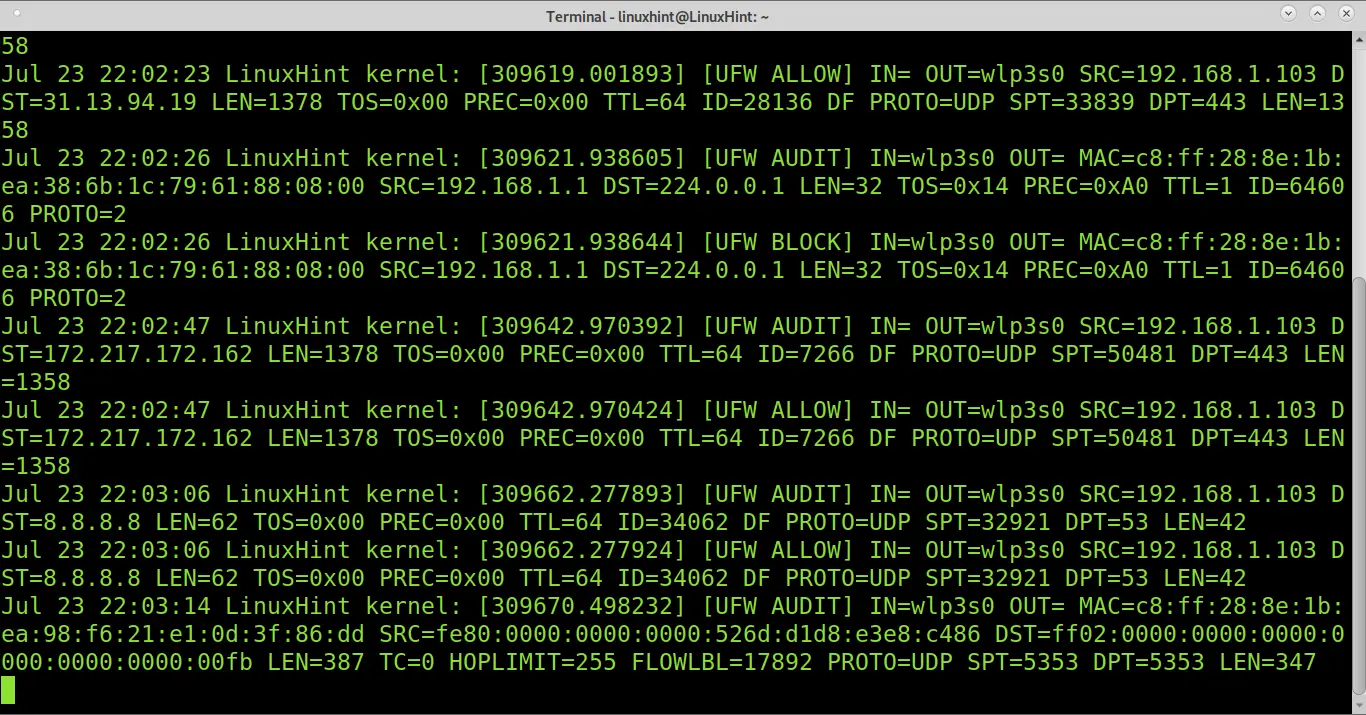
The new fields SPT and DPT, which were not explained previously, show the source and destination ports.
A different command to read UFW logs using grep would be:
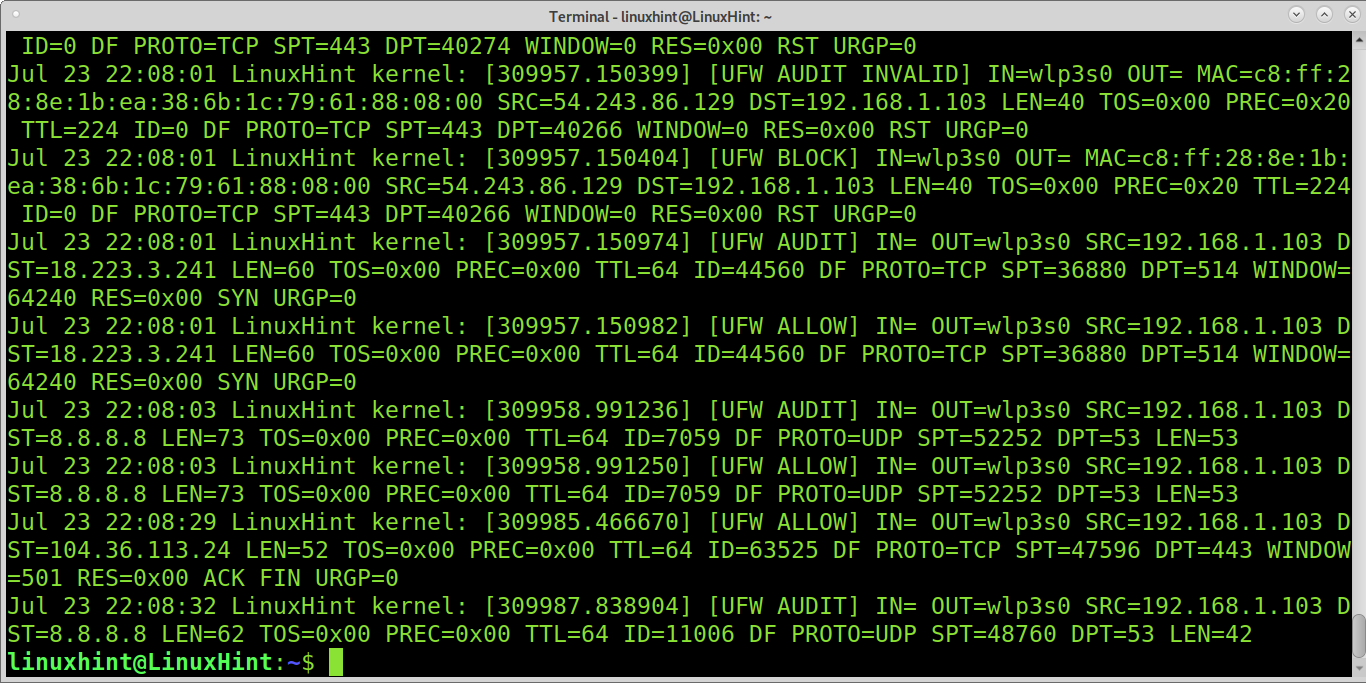
Or the following command:
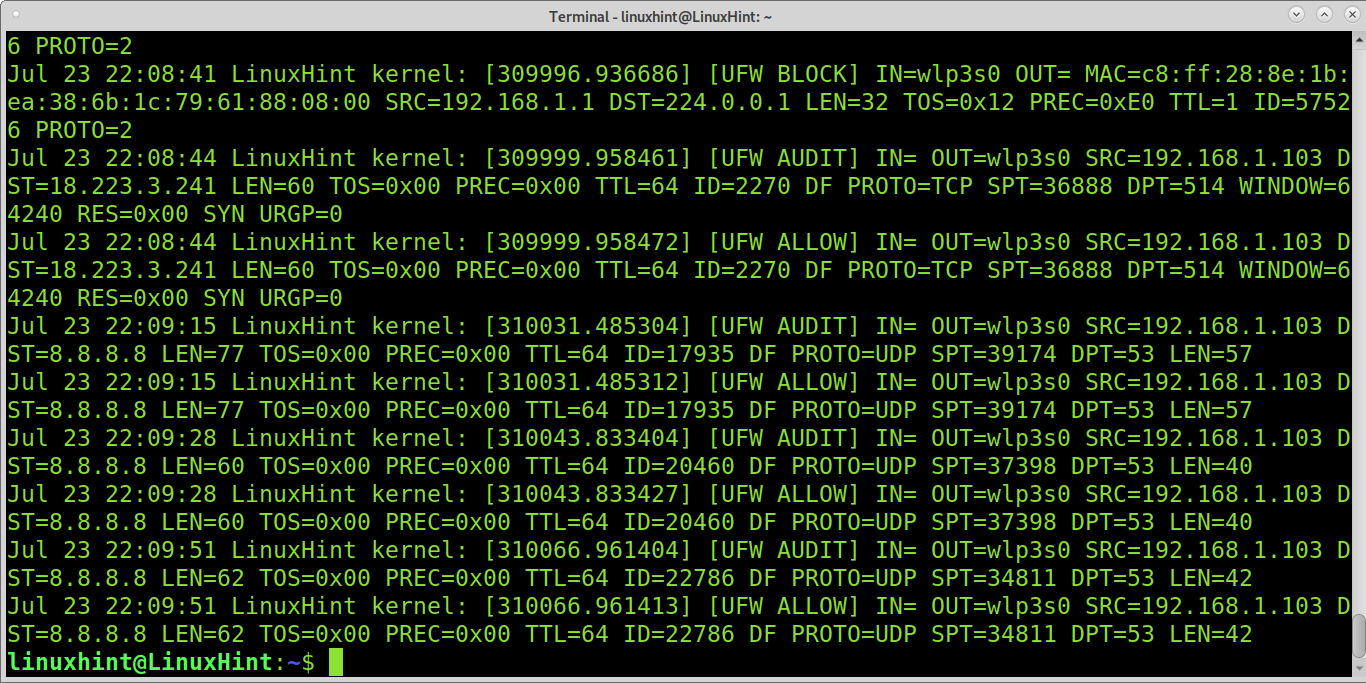
You also can run:
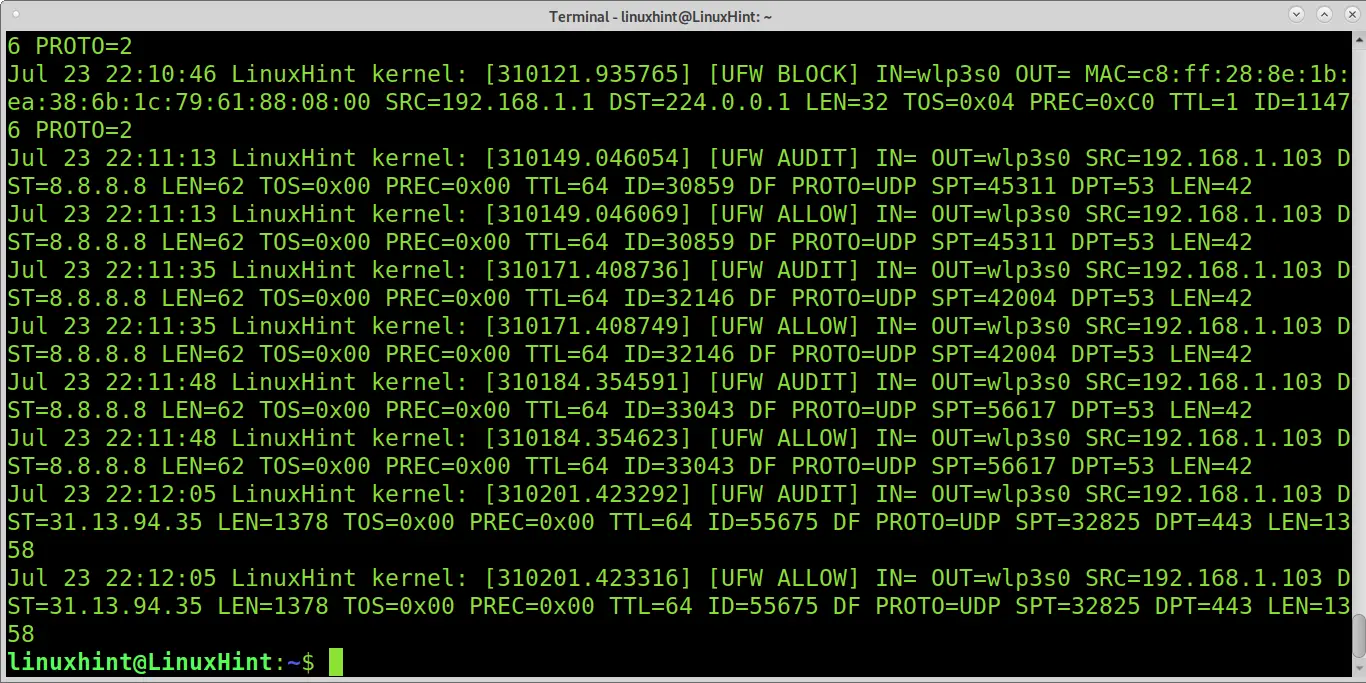
Conclusion:
UFW is the easiest CLI firewall front-end for Iptables in the market. Using it is even faster and simpler than using any other firewall, including GUI software. Some users ignore the logging feature, and it must be enabled and properly configured to get correct logs from UFW. It is also important to remember rsyslog must be enabled for this feature to work.
As you can see, UFW allows us to manage the verbosity level, and it provides a very detailed report on connections. UFW is an excellent tool for non-advanced users to control their network traffic and protect their system by implementing rules or actions with an easy syntax. Learning to use this Iptables front-end is a great way for new users to be introduced into the firewalls world before going through Iptables and Netfilter. UFW has a simple GUI interface (GUFW) to apply rules and actions and manage your firewall, despite the CLI version being even easier to use for any Linux user level.
I hope this tutorial explaining how to check UFW logs was useful. Keep following Linux Hint for more Linux tips and tutorials.
from Linux Hint https://ift.tt/3yvzqnu




0 Comments