Sublist3r is a tool to search and list subdomains easily. Sublist3r uses search engines and databases like Google, Bing, Yahoo, Ask, Baidu, Virustotal, Netcraft. ThreatCrowd, DNSdumpster, and ReverseDNS. Brute force ability was added with the integration of subbrute to Sublist3r.
This tutorial explains:
- How to search for subdomains using Sublist3r.
- How to scan ports of found subdomains.
- Specifying what search engines Sublist3r must use.
- How to implement brute force to discover subdomains.
- Saving Sublist3r output in a file.
How to install Sublist3r
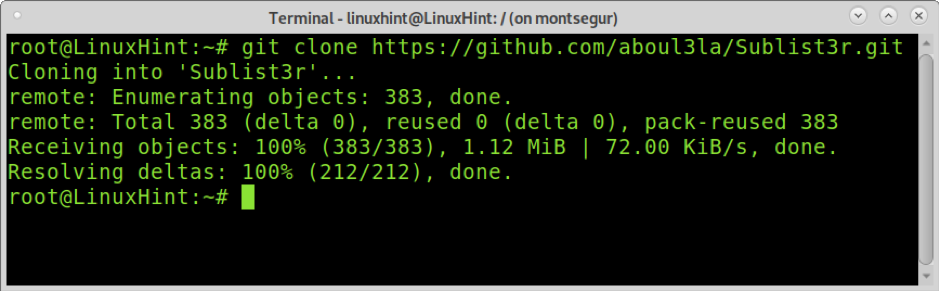
To start, use git to download Sublist3r as shown in the example below:
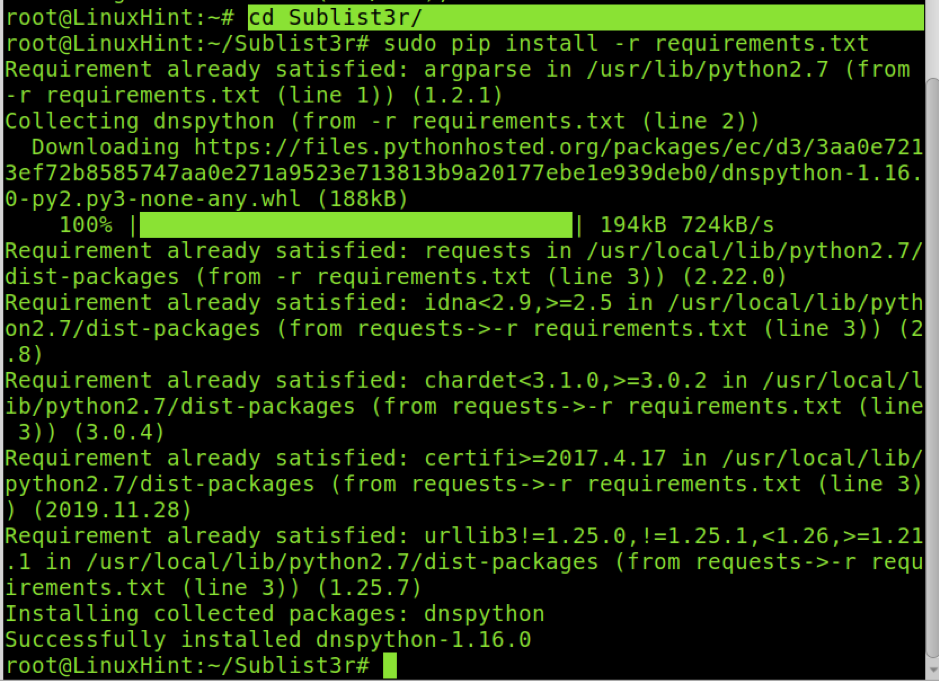
To install Sublist3r and dependencies, enter into Sublist3r directory using cd (Change Directory) and run the following pip as shown below:
sudo pip install -r requirements.txt
IMPORTANT: Currently, there is a bug preventing Sublist3r from gathering information from Virus Total. Official support channels explain users need a key provided by Virustotal you can get at https://www.virustotal.com/gui/. I tried to set the key and document all steps to add them to this tutorial, but adding the key didn’t work. That’s why you probably will see the error “Error: Virustotal probably now is blocking our requests.” Sublist3r will continue the task using the rest of the resources.
A conversation on this bug can be followed at https://github.com/aboul3la/Sublist3r/issues/288.
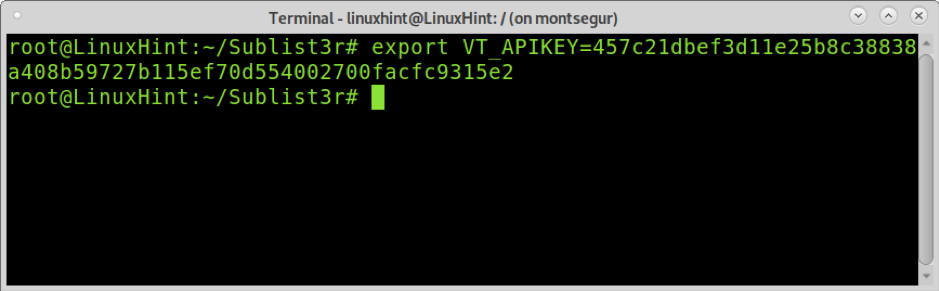
In case you still want to try, you can register for free at https://www.virustotal.com/gui/ to get the key and then export it:
Getting started with Sublist3r
To start, you can display the help menu with the -h argument by running the following command:
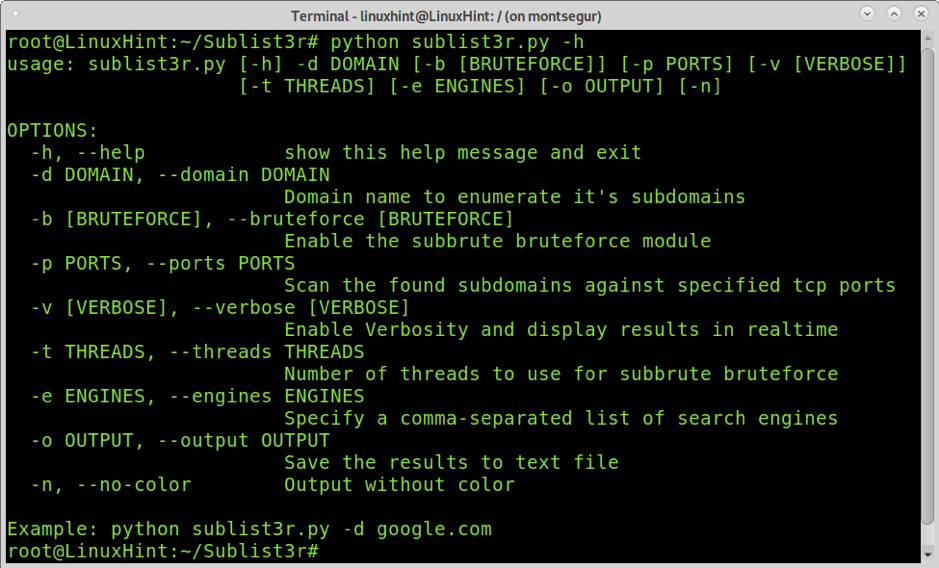
OPTIONS:
-d <DOMAIN>, –domain <Domain>: Domain name to enumerate its subdomains
-b <BRUTEFORCE>, –bruteforce <BRUTEFORCE>: Enable subbrute bruteforce module
-p <PORTS>, –ports <PORTS>: Scan the found subdomains against specified tcp ports
-v <VERBOSE>, –verbose <VERBOSE>: Enable Verbosity and display results in real-time -t <THREADS>, –threads <THREADS>: Number of threads to use for subbrute Bruteforce
-e <ENGINES>, –engines <ENGINES>: Specify a comma-separated list of search engines
-o <OutputFIle>, –output <OutputFIle>: save the results to text file
-n, –no-color: Output without color
The first example shows how to search subdomains of the website Godaddy by specifying it with the -d argument:
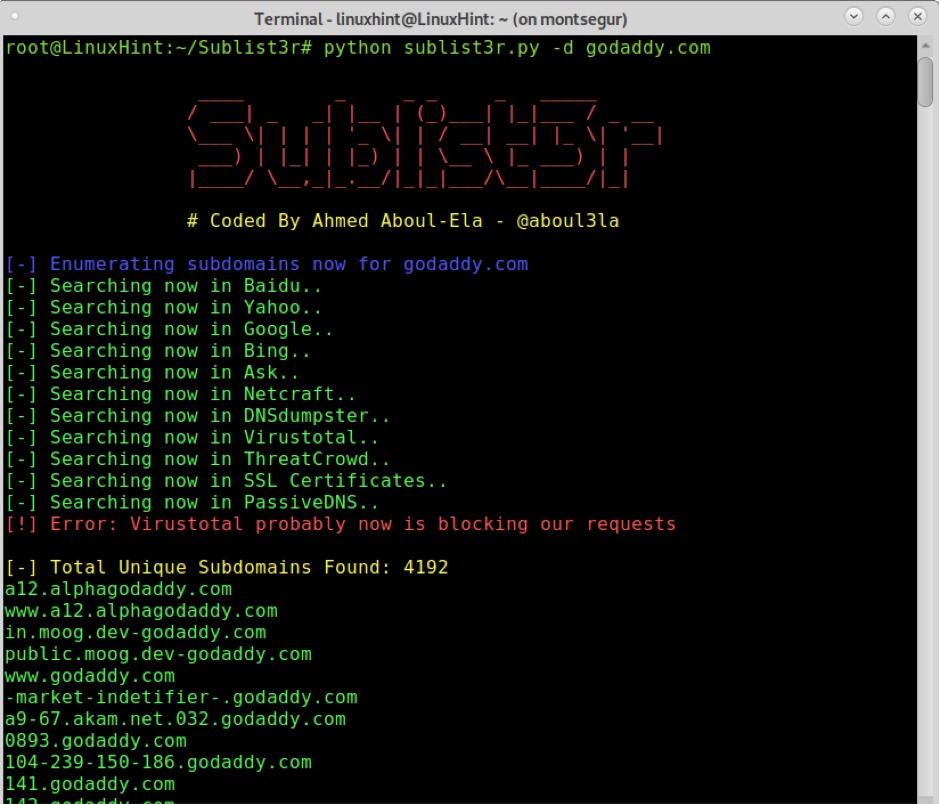
Sublist3r found 4192 Godaddy subdomains.
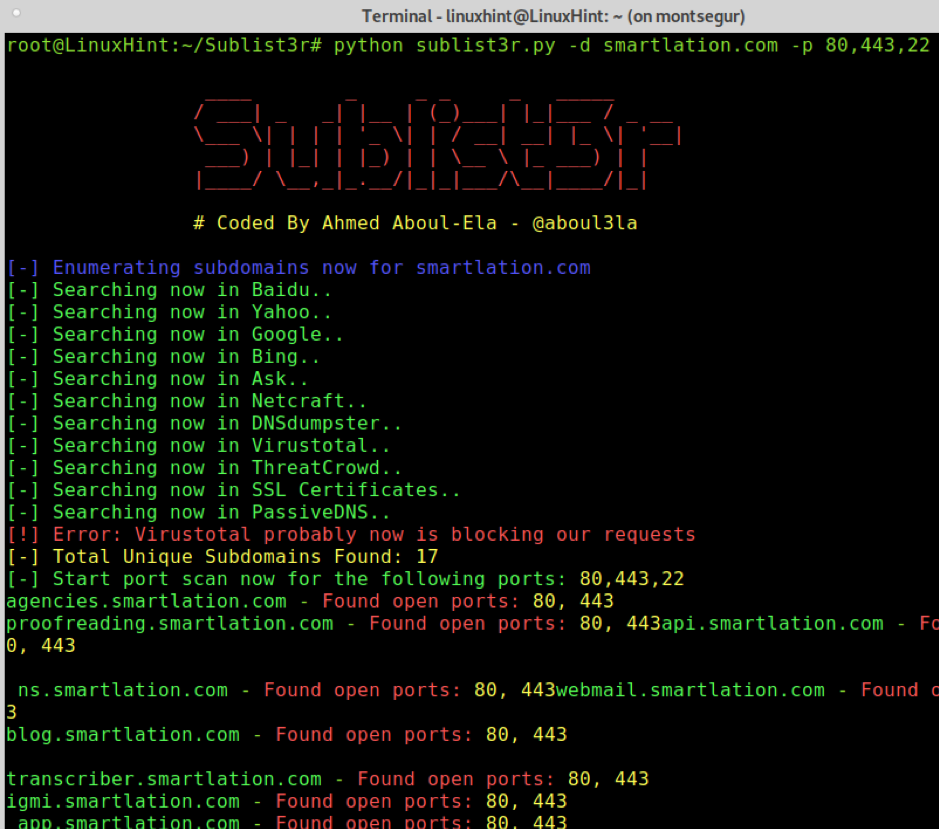
The following example shows how to implement the -p parameter instructing Sublist3r to scan all ports 80 (http) for all found subdomains on Smartlation:

As you can see, 17 unique subdomains were found, all of them with port 80 open.
You can specify several (TCP) ports to be scanned by using comma as shown in the following example in which ports 80 (http), 443 (https), and 22 (ssh) are scanned:
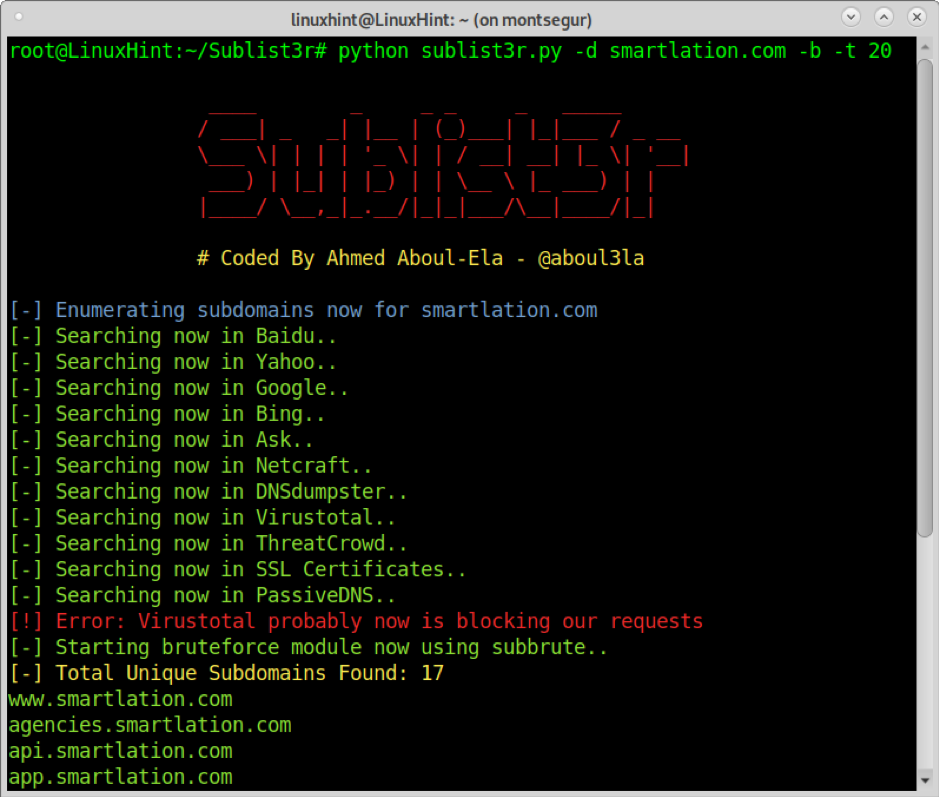
The following example shows how to execute a new search, but this time implementing brute force too by adding the argument -b with 100 threads (-t 100). The subdomain dictionary is called names.txt and contains 101,010 subdomains. Implementing brute force takes time; for descriptive purposes, I edited the names.txt file (located under the subbrute subdirectory), leaving only a dozen words.
As described in the help menu, you can define specific search engines using the argument -e. The following example shows a search for subdomains including brute force and limiting search engines to Google and Bing:

As you can see, only 4 subdomains were found because only Google and Bing search engines were included.
The next example shows a new search, including NetCraft, DnsDumpster, and Bing. The command also includes a port scan (-p) against port 22 for each found subdomain and brute force (-b) implementation. The argument -o instructs Sublist3r to save the results in the file Sublist3r-Tutorial.
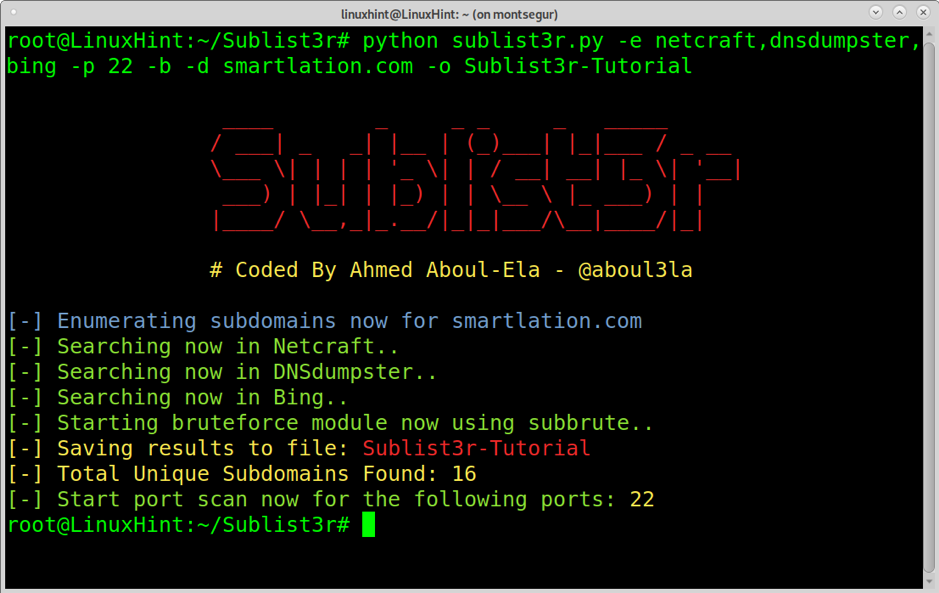
You can check the output by reading Sublist3r-Tutorial:
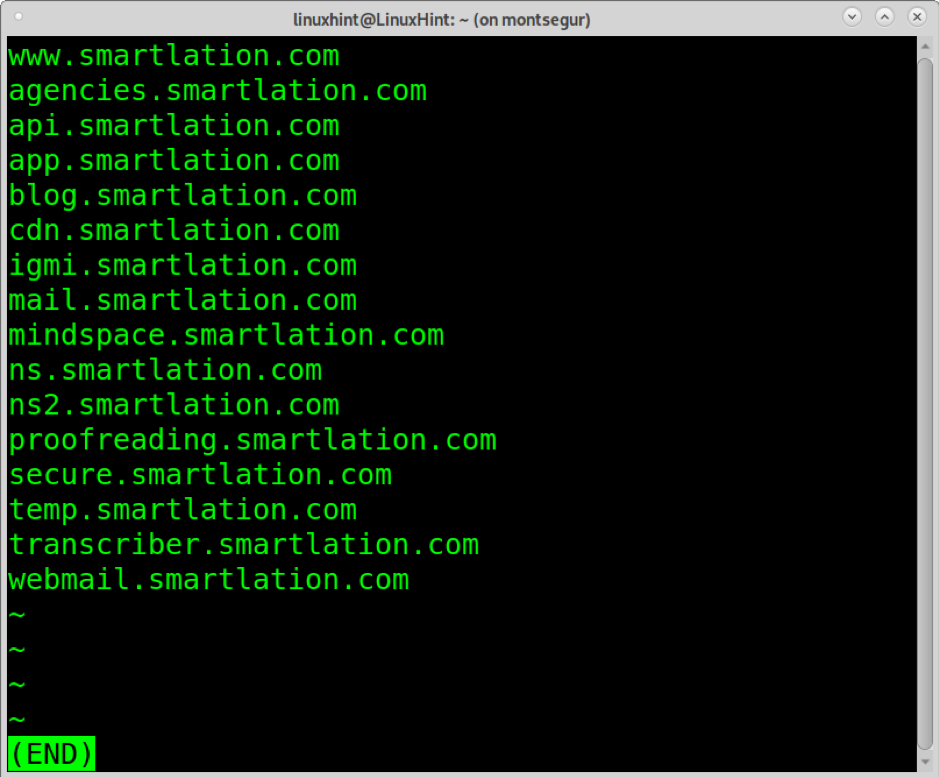
This time only 16 subdomains were found because we kept search engines limited to a few.
Conclusion
Sublist3r is a great option for searching subdomains. The program is accessible to all user levels, easy to run and implement its options. The brute force integration added interesting features comparable to DNS Brute and similar Nmap NSE scripts.
Some of the Sublist3r alternatives include Subfinder or AltDNS.
Alternatively, you can use web applications such as SHODAN or Spyse.
I hope this Sublist3r tutorial was useful; keep following LinuxHint for more Linux tips and tutorials.
from Linux Hint https://ift.tt/2S6RnsM




0 Comments