One of the most prominent and ever-present dangers of connecting to the internet is a comprised system where attackers can use your devices to steal personal information and other sensitive information.
Although there are various methods someone can use to attack a system, rootkits are a popular choice among malicious hackers. The essence of this tutorial is to help you enhance the security of your Linux device by using the RKhunter or Rootkit hunter.
Let’s get started.
What are Rootkits?
Rootkits are powerful and malicious programs and executables installed on a compromised system to preserve access even if a system have a security vulnerability patch.
Technically, rootkits are some of the most amazing malicious tools used in the second to the final step in the penetration testing stage (Maintaining Access).
Once someone installs a rootkit into a system, it gives the attacker remote control access to the system or network. In most cases, rootkits are more than a single file that performs various tasks including creating users, starting processes, deleting files, and other actions harmful to the system.
Fun Reference: One of the best illustrations of how harmful rootkits are is in the TV show Mr. Robot. Episode 101. Minutes 25-30. Quote Mr. Robot (“Sorry, It’s a malicious code that completely takes over their system. It could delete system files, install programs, viruses, worms…It’s fundamentally invisible, you can’t stop it.”)
Type of Rootkits
There are various types of rootkits, each performing various tasks. I will not dive into how they work or how to build one. They include:
Kernel Level Rootkits: These types of rootkits operate at the kernel level; they can perform operations at the core part of the operating system.
User Level Rootkits: These rootkits operate in normal user mode; they can perform tasks like navigating directories, deleting files, etc.
Memory Level Rootkits: These rootkits reside in your system’s main memory and hog your system’s resources. As they do not inject any code into the system, a simple reboot can help you remove them.
Bootloader Level Rootkits: These rootkits mainly target the bootloader system and mainly affect the bootloader and not system files.
Firmware Rootkits: They are a very severe type of rootkits that affect system firmware, thus infecting all other parts of your system, including hardware. They are highly undetectable under a normal AV program.
If you wish to experiment with rootkits developed by others or build yours, consider learning more from the following resource:
https://awesomeopensource.com/project/d30sa1/RootKits-List-Download
NOTE: Test rootkits on a virtual machine. Use at your own risk!
What is RKhunter
RKhunter, commonly known as RKH, is a Unix utility that allows users to scan systems for rootkits, exploits, backdoors, and keyloggers. RKH works by comparing hashes generated from files from an online database of unaffected hashes.
Learn more about how RKH works by reading its wiki from the resource provided below:
https://sourceforge.net/p/rkhunter/wiki/index/
Installing RKhunter
RKH is available in major Linux distributions and you can install it using popular package managers.
Install on Debian/Ubuntu
To install on debian or ubuntu:
sudo apt-get install rkhunter -y
Install on CentOS/REHL
To install on REHL systems, download the package using curl as shown below:
Once you have the package downloaded, unpack the archive and run the installer script provided.
[centos@centos8 ~]$ cd rkhunter-1.4.6/
[centos@centos8 rkhunter-1.4.6]$ sudo ./installer.sh --install
Once the installer completes, you should have rkhunter installed and ready to use.
How to Run a System Check Using RKhunter
To run a system check using the RKhunter tool, use the command:
Executing this command will launch RKH and run a full system check on your system using an interactive session as shown below:

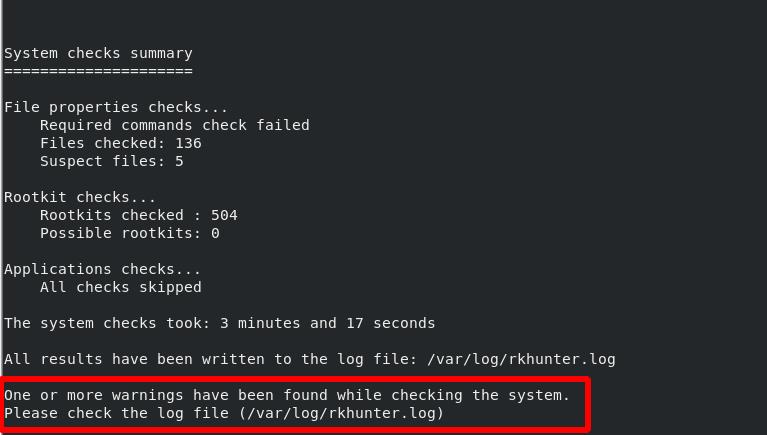
After completion, you should get a full system check report and logs in the location specified.
Conclusion
This tutorial has given you a better idea of what rootkits are, how to install rkhunter, and how to perform a system check for rootkits and other exploits. Consider running a deeper system check for critical systems and fix them.
Happy rootkit hunting!
from Linux Hint https://ift.tt/3tTUXmQ




0 Comments