Through command-line prompt Nmap, the tool provides multiple features such as exploring networks, finding open ports, ping sweeps, OS detection, and many more.
This post is focusing on how to use the Nmap command in the terminal with detailed examples. Let’s check them one by one:
How to install Nmap Command
Before exploring with Nmap commands, the Nmap scanner tool must have installed on your system. So, if it is not downloaded yet, get it by opening up the terminal and executing the following command:
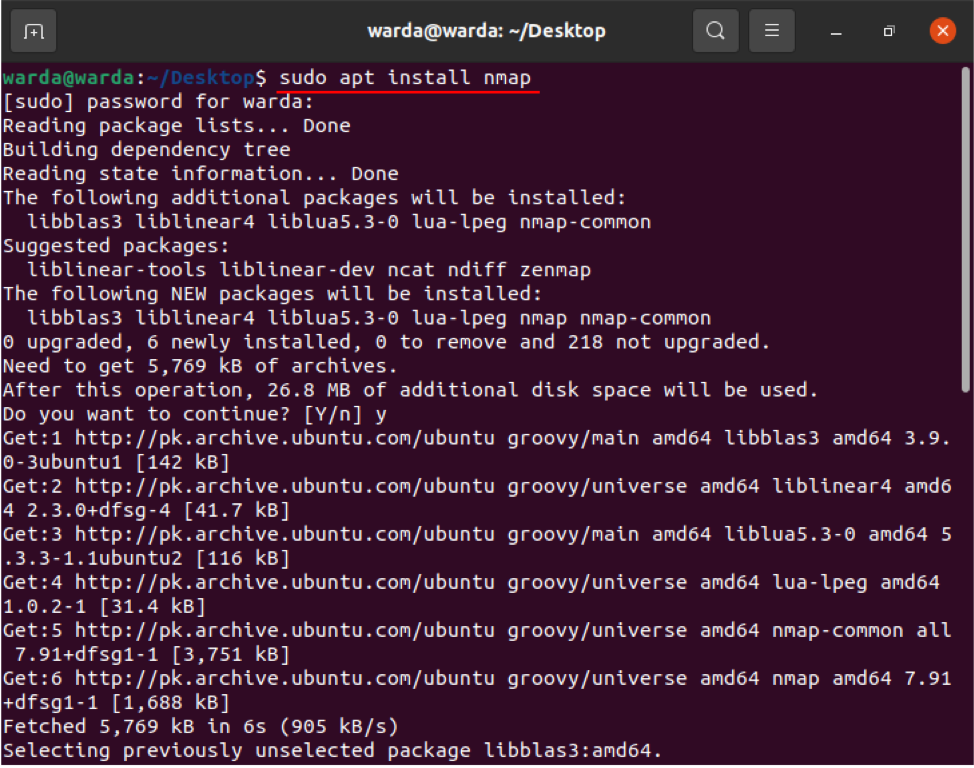
Once the download and installation are done, check the various functions and operations of the Nmap command with examples:
How to scan hostname using Nmap command
To perform a scan using hostname and IP address is the best way to run Nmap commands. For example, I set the hostname as “linuxhint.com”:
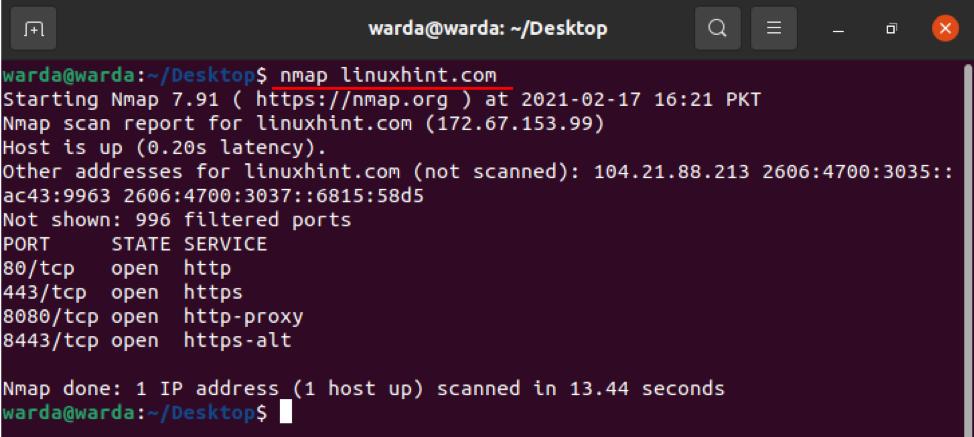
How to scan IP address using Nmap command
Use mentioned command in terminal to scan through IP address:
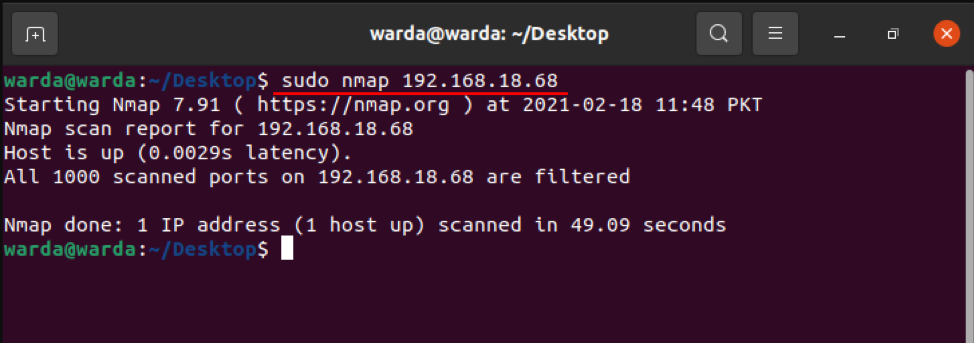
How to scan using the “–v” option with Nmap Command
The -v command is used to get a more elaborative detail about the connected machine. So, type command in terminal:
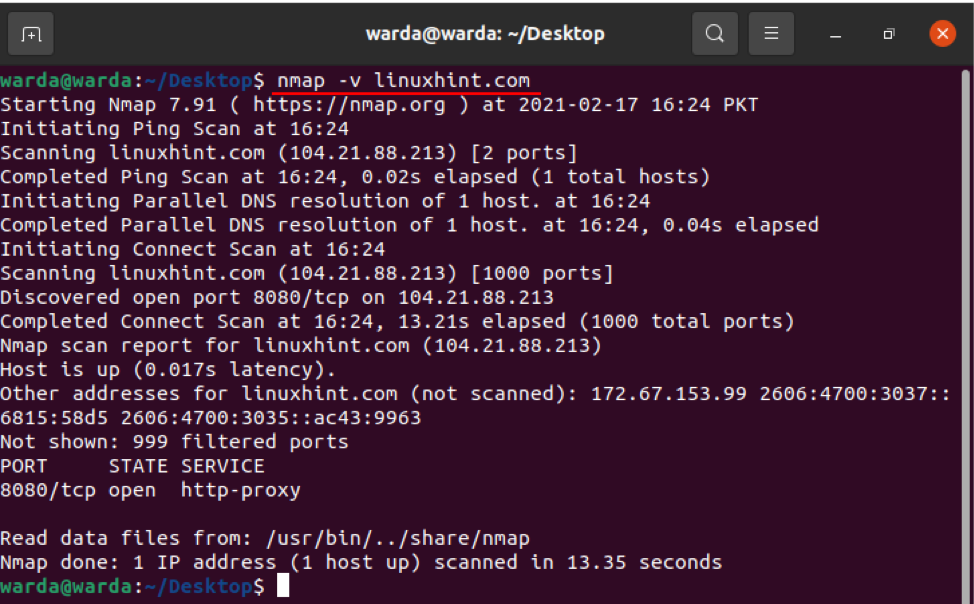
IP Address Range
It is easy to specify the IP range using the Nmap scanner tool, use the command given below:
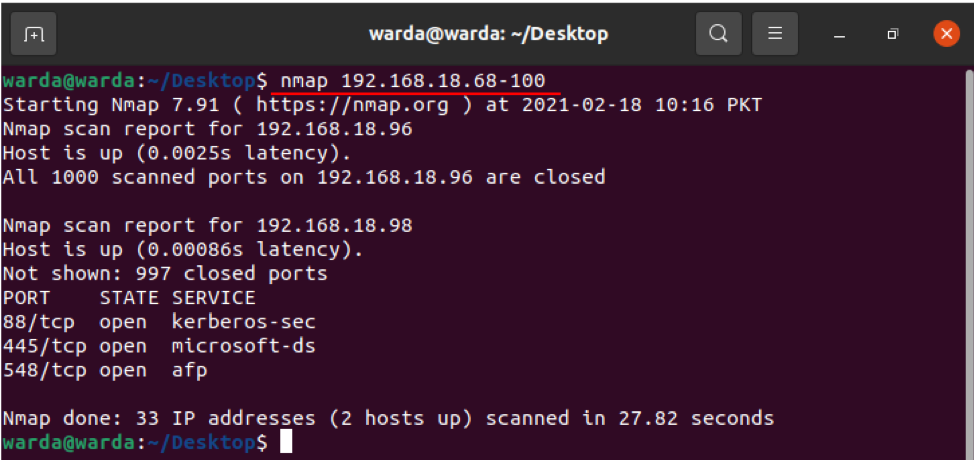
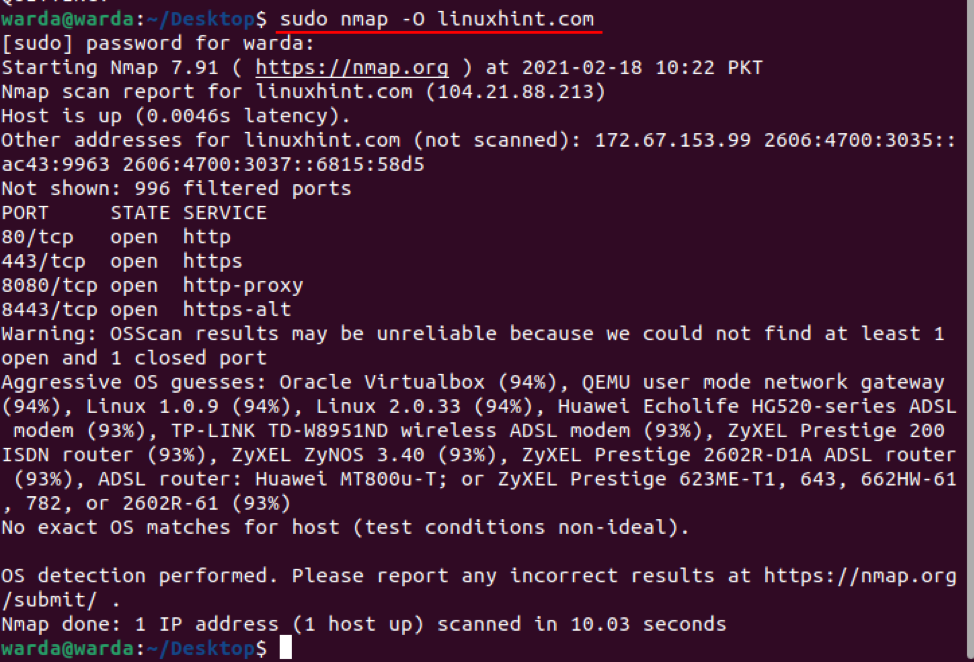
How to enable OS detection with Nmap
Nmap scanner tool helps to detect operating system and version as well running on the localhost. If you want to get OS details, you can use “-O”:
How to Detect Firewall
To check if the local host is using any Firewall, type “-sA” in the terminal with “nmap”:
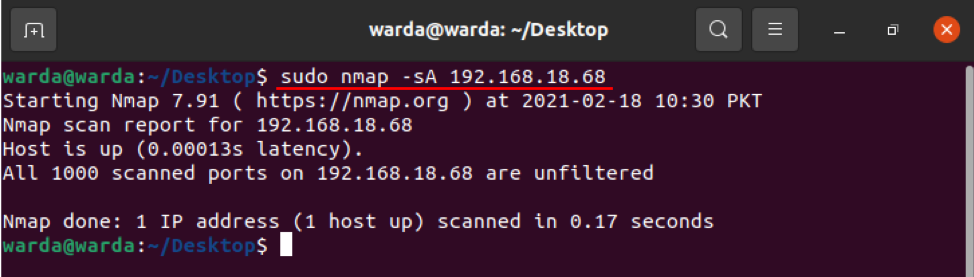
As it can be seen in the above result that no packet is filtered.
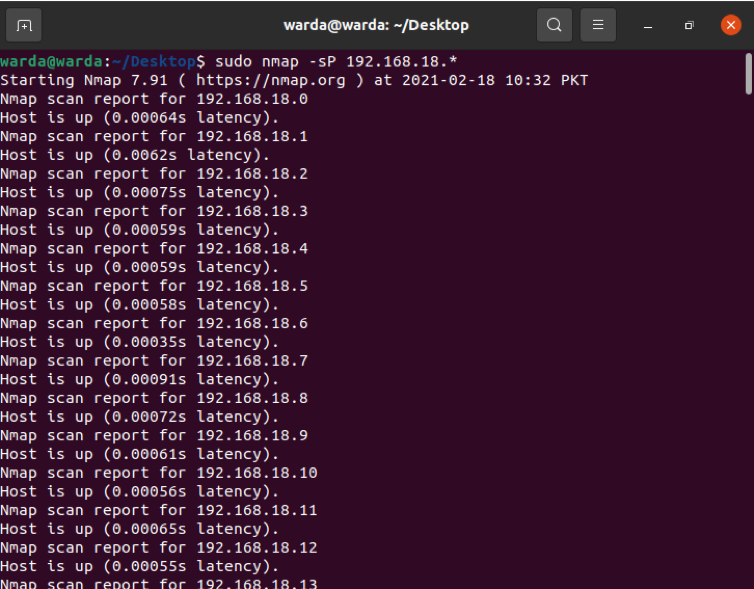
How to find a Live host
Type “-sP” to scan a list of all live and up hosts:
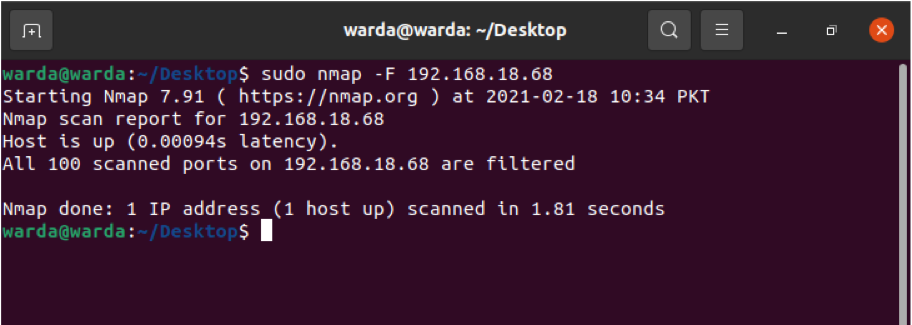
How to Perform Fast Scan with Nmap
Use the “-F” flag with Nmap in a terminal, and it will perform a fast scan for the ports listed in Nmap services:
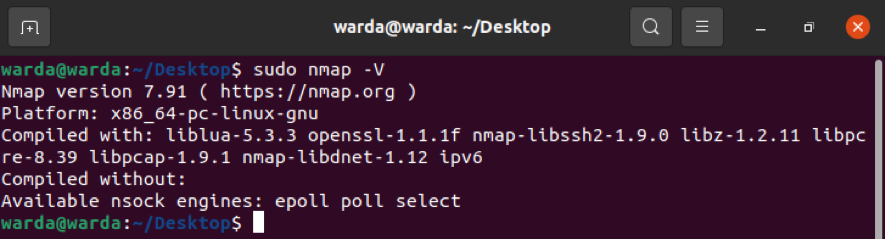
How to find Nmap Version
Find out the Nmap version to update the latest version of the previous one that is old.
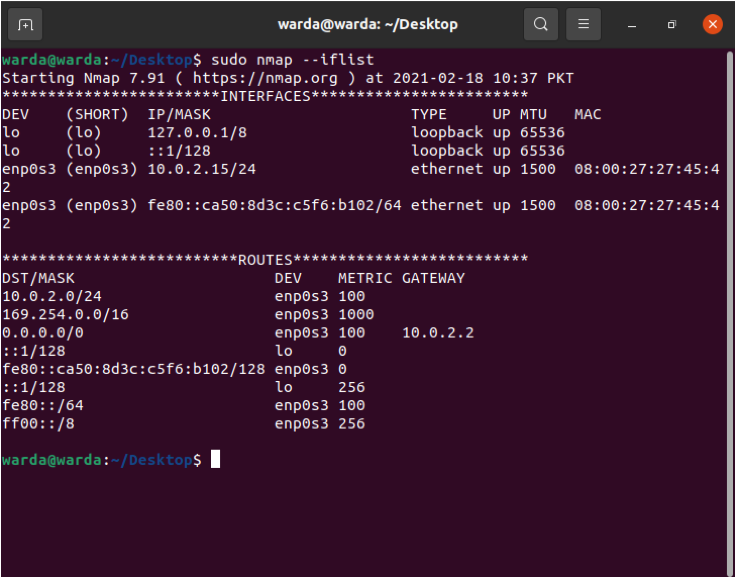
How to Print host interfaces and routes using Nmap
The “-iflist” command is used to find out routes and hosts interface information. Use the below-mentioned command to perform this scan:
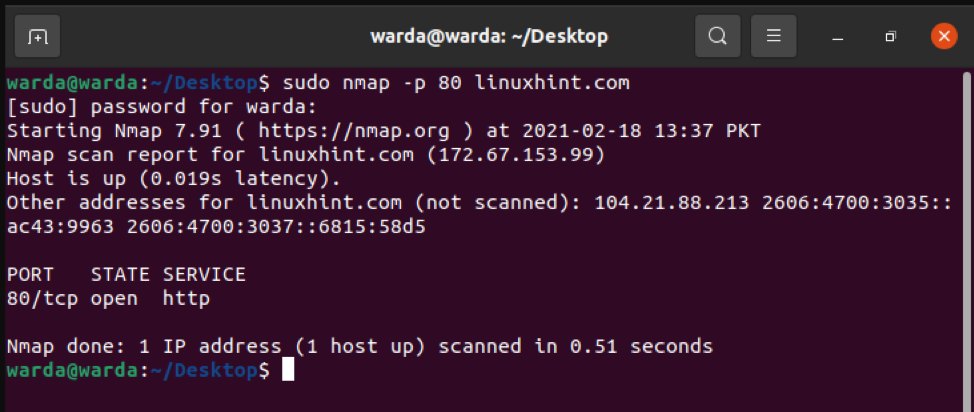
How to scan Specific Port with Nmap
If you want to list out details of a specific port, type “-p”; otherwise Nmap scanner will scan TCP ports by default:
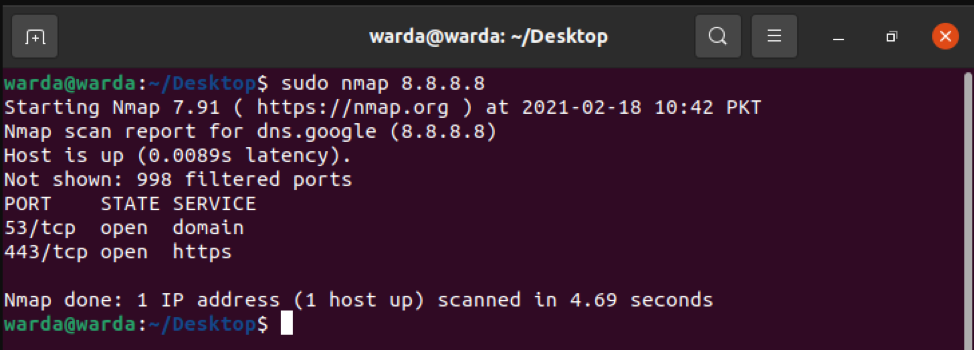
How to scan TCP Ports
All open ports TCP ports can be scanned through 8.8.8.8:
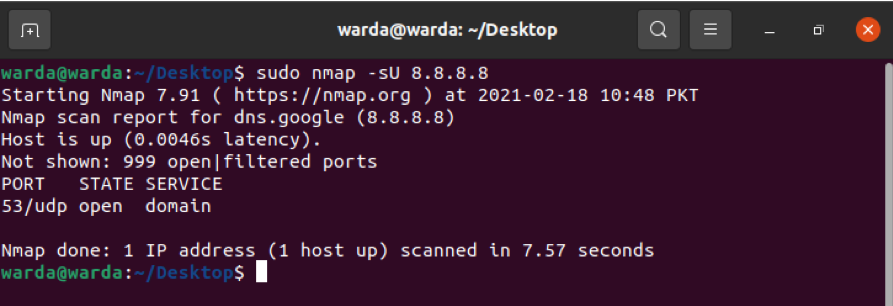
How to scan UDP Ports
All open ports UDP ports can be seen through the following command:
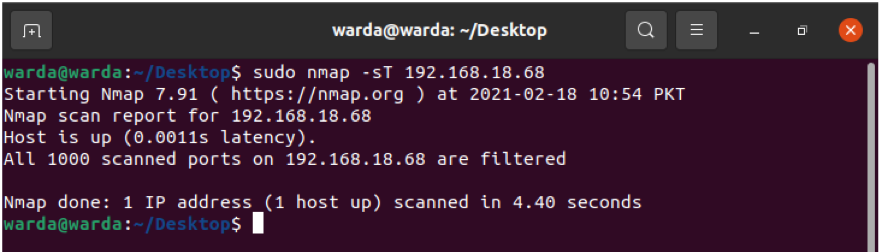
Most Common Ports with TCP Sync
Check the most commonly used ports through –sT that is sync with TCP ports.
Type:
TCP Null Scan to Fool a Firewall
Following -sN command will help to show TCP null scan to fool a firewall:

Conclusion
Nmap is a scanner tool used to help network administrators to secure their networks. Using this guide, we have learned that how the Nmap tool and its functionality work with examples.
from Linux Hint https://ift.tt/30GO6AQ




0 Comments