IPS or Intrusion Prevention System is a technology used in network security to examine network traffic and prevent different attacks by detecting malicious inputs. Apart from just detecting malicious inputs as Intrusion Detection System does, it also prevents the network from malicious attacks. It can prevent the network from brute-force, DoS (Denial of Service), DDoS (Distributed Denial of Service), Exploits, worms, viruses, and other common attacks. IPS are placed just behind the firewall, and they can send alarms, drop malicious packets and block offending IP addresses. In this tutorial, we will use Fail2ban, which is an Intrusion Prevention Software package, to add a security layer against different brute force attacks.
How Fail2ban Works
Fail2ban reads the log files (e.g. /var/log/apache/error_log) and gets the offending IPs that are attempting too many failed passwords or seeking for exploits. Basically, Fail2ban updates firewall rules to block different IPs on the server. Fail2ban also provides filters using which we can use for a specific service (e.g., apache, ssh, etc.).
Installing Fail2ban
Fail2ban does not come pre-installed on Ubuntu, so before using it, we have to install it.
ubuntu@ubuntu:~$ sudo apt-get install fail2ban
After installing Fail2ban, start and enable the Fail2ban service using the command line.
ubuntu@ubuntu:~$ sudo systemctl enable fail2ban
Now check the status of the fail2ban service to confirm whether it started or not.
Configuring Fail2ban For SSH
We can configure Fail2ban by modifying /etc/fail2ban/jail.conf file. Before modifying it, take a backup of this file.
Now we will configure Fail2ban to prevent sshd service from malicious inputs. Open /etc/fail2ban/jail.local file in your favourite editor.
Go to the [default] section and enter configuration parameters under [default] section.
ignoreip = 127.0.0.1/8 192.168.18.10/32
bantime = 300
maxretry = 2
findtime = 600
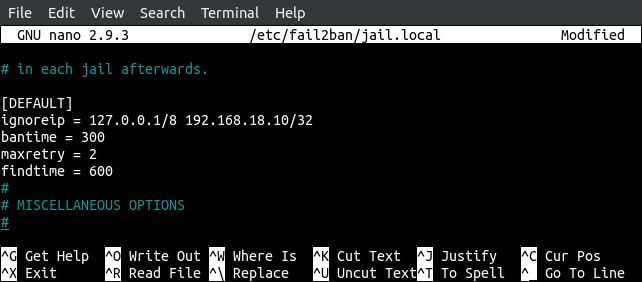
ignoreip is the list of cidr mask, ip address, or DNS host separated by a space character. Add your trusted IPs to this list, and these IPs will be whitelisted and will not be blocked by fail2ban even if they perform a brute force attack on the server.
bantime is the time an IP will be blocked after making a specific amount of failed attempts to the server.
maxretry is the number of maximum failed attempts after which an IP is blocked by fail2ban for a specific amount of time.
findtime is the amount of time during which if a host makes maxretry failed attempts, it will be blocked.
After configuring the above parameters, now we will configure the service on which the above rules are going to apply. By default, Fail2ban has pre-defined filters for different services, so we do not need to enter any specific entries for services. We only enable or disable different services in the configuration file. Open /etc/fail2ban/jail.local file in your favourite editor.
Find the [sshd] section in the file and enter the following parameters in the section.
enable = true
port = ssh
filter = sshd
logpath = /var/log/auth.log
maxretry = 3

enabled defines whether this service is being protected by fail2ban or not. If enabled is true, then the service is being protected; otherwise, it is not being protected.
port defines service port.
filter refers to the configuration file fail2ban will use. By default it will use /etc/fail2ban/filter.d/sshd.conf file for ssh service.
logpath defines the path to logs, fail2ban will monitor to protect service from different attacks. For ssh service, authentication logs can be found at /var/log/auth.log, so fail2ban will monitor this log file and will update the firewall by detecting failed login attempts.
maxretry defines the number of failed login attempts before being blocked by the fail2ban.
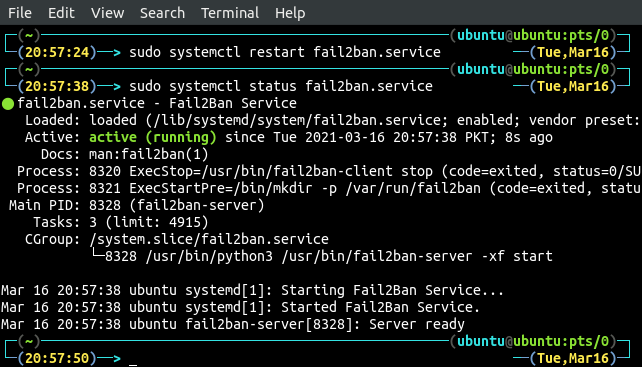
After applying the above configuration for fail2ban, restart the service to save changes.
ubuntu@ubuntu:~$ sudo systemctl status fail2ban.service
Testing Fail2ban
We have configured fail2ban to protect our system against brute force attacks on ssh service. Now we will make failed login attempts on our system from another system to check whether fail2ban is working or not. After making some failed login attempts now, we will check fail2ban logs.

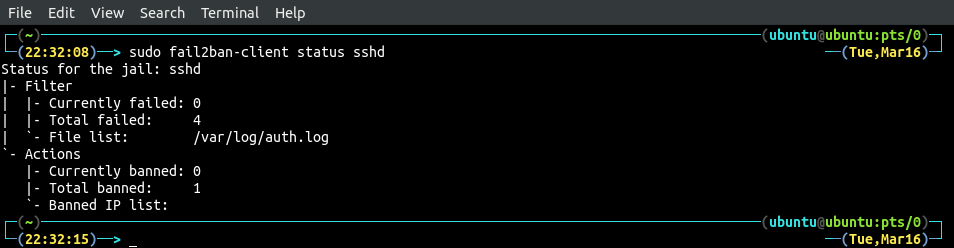
We can see that after failed login attempts, the IP has been blocked by fail2ban.
We can get a list of all the services for which fail2ban is enabled for by using the following command.

The above figure shows that we have enabled fail2ban only for sshd service. We can get further information about the sshd service by specifying the service name in the above command.
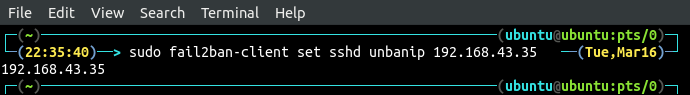
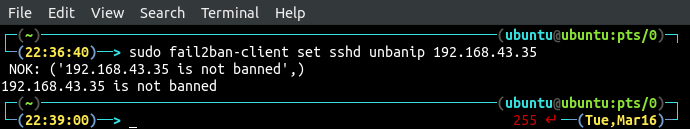
Fail2ban automatically unban the banned IP address after bantime, but we can unban any IP at any time using the command line. This will give more control over fail2ban. Use the following command to unban the IP address.
If you try to unban an IP address that is not blocked by fail2ban, it will just tell you that the IP is not blocked.
Conclusion
For a system administrator or a security engineer, it is a big challenge to maintain the security of the servers. If your server is being protected by the password, not by public and private key pair, then your server is more vulnerable to brute force attackers. They can get into your system by applying different password combinations. Fail2ban is a tool that can restrict attackers from launching different kinds of attacks, including brute force attacks and DDoS attacks on your server. In this tutorial, we discussed how we could use Fail2ban to protect our server from different attacks. We can also use Fail2ban to protect other services such as apache, nginx, etc.
from Linux Hint https://ift.tt/399rkGs



0 Comments