- Retrieving data from smart-watches that are using MTK chipsets.
- Retrieving data from IoT devices (Amazon Alexa and Google Home)
- Extracting data from the above 60 cloud sources, including Huawei, ICloud, MI cloud storage, Microsoft, Samsung, Email server Amazon drive, etc.
- Retrieving flight history with metadata, videos, and all the images.
- Retrieving data from drones, drone logs, drone mobile apps, and drone cloud storage like DJI cloud and SkyPixel.
- Analyzing call data records received from mobile service providers.
Data extracted using the Oxygen Forensics suite can be analyzed in a user-friendly and built-in analytical section that includes a proper timeline, graphs, and key evidence area. Here data of our need can be searched easily using various searching techniques like keywords, hash sets, regular expressions, etc. The data can be exported into different formats, such as PDFs, RTF, and XLS, etc.
Oxygen Forensics Suite runs on systems using Windows 7, Windows 10, and Windows 8. It supports USB cable and Bluetooth connections and also allows us to import and analyze data from various device backups(Apple iOS, Windows Operating system, Android Operating System, Nokia, BlackBerry, etc.) and Images (acquired by using other tools used for forensics). The current version of Oxygen Forensics Suite supports 25000+ mobile devices that could be running any kind of operating system like Windows, Android, iOS, Qualcomm chipsets, BlackBerry, Nokia, MTK, etc.
Installation:
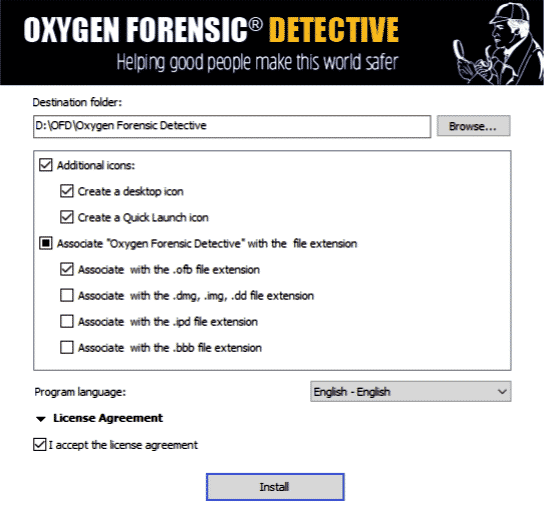
In order to use Oxygen Forensics Suite, the package must be bundled in a USB device. After having the package in a USB stick, plug it into a computer system and wait for the driver’s initialization then start the main program.
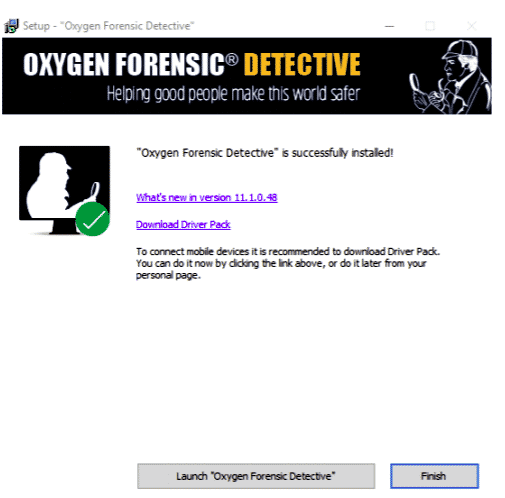
There will be options on the screen asking for a location where to install the software, the language you want to use, creating icons, etc. After reading them carefully, click Install.
Once the installation is completed, you may have to install a driver pack, which is best suitable as given. Another important thing to note is that you have to insert the USB drive the whole time you are working on Oxygen Forensics Suite.
Usage:
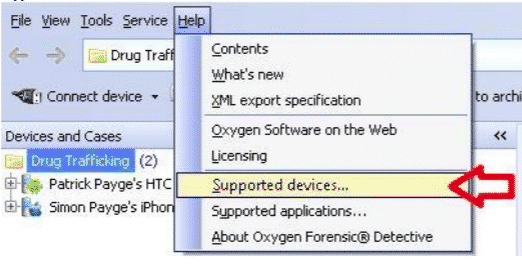
The first thing we need to do is to connect a mobile device. For this, we need to make sure all required drivers are installed and check if the device is supported or not by clicking on the HELP option.
To begin extracting the data, connect the device to the computer system with the Oxygen Forensics Suite installed in it. Attach a USB cable or connect via Bluetooth by turning it on.
The list of connections varies with device capabilities. Now choose the extraction method. In case the device is locked, we can bypass screen lock and security code and perform physical data retrieval in some android operating systems (Motorola, LG, and even Samsung) by selecting the Physical data acquisition option with our device type selected.
Now it will search for the device, and once it’s completed, it will ask for information about the case number, case, investigator’s name, date and time, etc. to help it manage the device information systematically.
At the point when all information is extracted, you can open the gadget for review and examining information or run the Export and Print Wizard on the off chance that you have to get a quick report about the gadget. Note that we can run Export or Print Wizard whenever while working with the gadget data.
Extraction Methods:
Android data extraction:
Android backup:
Connect an Android gadget and pick the Android backup extraction method in the program window. Oxygen Forensic Suite will gather the information accessible by means of this technique. Each application designer chooses which client information to place in the reinforcement. It implies there is no guarantee that application information will be retrieved. This method works on Android 4.0 or higher, and the device shouldn’t be locked by a security code or password.
OxyAgent method:
This is the technique that takes a shot at any supported Android System. On the off chance that different techniques come up short, this strategy will procure at any rate the base arrangement of information. OxyAgent has no entrance to the inside memory organizers; consequently, it won’t return the inward memory records and won’t recoup erased information. It will assist with retrieving just contacts, messages, calls, schedules, and records from streak drive. In case the USB port is broken, or it isn’t working there, we should insert an SD card, and that will do the work.
ROOT access:
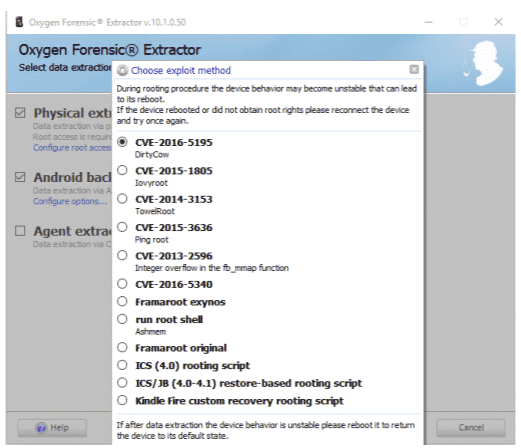
Having root access even for a small period of time will help investigators recover every bit of data, including files, folders, images documents, deleted files, etc. For the most part, this technique requires certain knowledge, but Oxygen Forensic Suite’s items can perform it naturally. The product utilizes a restrictive adventure to shell root Android gadgets. There is no 100% success guarantee, but for supported android versions (2.0-7.0), we can depend on it. We should follow these steps in order to perform this:
- Connect the android device to oxygen forensics software using a cable.
- Choose device acquisition so that the Oxygen Forensics Suite can automatically detect the device.
- Choose a physical method by rooting option and select the exploit from many exploits given (DirtyCow works in most of the cases).
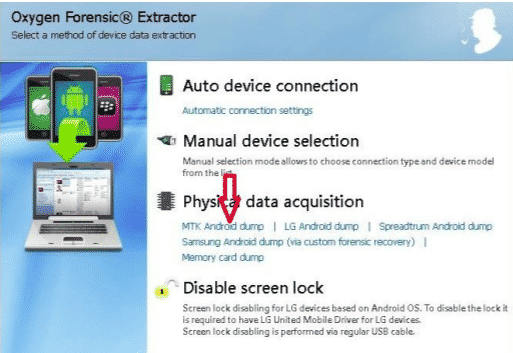
MTK Android dump:
We use this method to bypass any kind of screen locks, passwords, pins, etc. with devices using MTK chipsets. To use this method, the device must be connected in switched off mode.
This option can’t be used with a locked bootloader.
LG Android dump:
For LG models devices, we use the LG android dump method. In order for this method to work, we need to make sure that the device is placed into Device Firmware Update Mode.
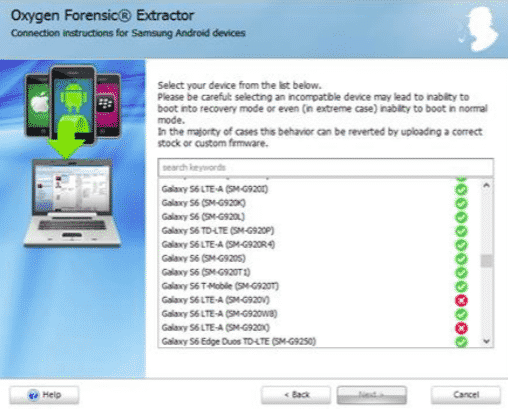
Samsung devices’ custom recovery:
Oxygen Forensics Suite provides a very good method for data retrieval from Samsung devices for supported models. The supported model’s list is increasing day by day. After selecting the Samsung Android dump from the Physical data acquisition menu, we will have a list of popular supported Samsung devices.
Choose the device of our need, and we are good to go.
Motorola Physical dump:
Oxygen Forensics Suite provides a way to extract data from password-protected Motorola devices supporting the latest Motorola devices (2015 onwards). The technique permits you to sidestep any screen lock secret key, locked bootloader, or introduced FRP and access the critical data, including application information and erased records. The information extraction from Motorola gadgets is performed consequently with a couple of manual controls on the analyzed gadget. Oxygen Forensics Suite transfers a Fastboot image into the device that must be exchanged into Fastboot Flash mode. The technique doesn’t influence any user data. Physical extraction is finished by utilizing Jet Imager, the most recent innovation in extricating information from Android gadgets that permits to procure the information in a few minutes.
Qualcomm Physical dump:
Oxygen Forensics Suite permits forensics investigators to use the non-obtrusive physical obtaining procedure by means of EDL mode and sidestep screen lock on 400+ extraordinary Android gadgets in view of Qualcomm chipset. Using EDL alongside information extraction is regularly a lot quicker than Chip-Off, JTAG, or ISP, and ordinarily doesn’t require telephone dismantling. Moreover, utilizing this technique doesn’t change user or system data
Oxygen Forensics Suite offers help for devices with the accompanying chipsets:
MSM8909, MSM8916, MSM8917, MSM8926, MSM8929, MSM8936, and so forth. The rundown of supported devices incorporates models from Acer, Alcatel, Asus, BLU, Coolpad, Gionee, Huawei, Infinix, Lenovo, LG, LYF, Micromax, Motorola, Nokia, OnePlus, Oppo, Swipe, Vivo, Xiaomi, and numerous others.
iOS data Extraction:
Classic Logical:
This is an all-inclusive technique and is suggested for all iOS gadgets and utilization iTunes reinforcement systems to obtain information. On the off chance that iTunes reinforcement is scrambled, the product will endeavor to discover password various supported attacks (brute force, dictionary attack, etc.). The strategy will return enough user information, including erased records and applications.
iTunes backup:
Backup records of iOS devices made in iTunes can be imported in Oxygen Forensic Analyst with the assistance of Oxygen Forensics Extractor. Any measurable inspector can helpfully dissect the information of Apple gadgets in the interface of Oxygen Forensic Suite or then again create reports of the obtained information. For this, go to:
Import File >> Import Apple backup >> import ITunes backup
For Backup images go to:
Import File >> Import Apple backup image
Windows data Extraction:
As of now, to get to important user data, the inspector must acquire a physical picture, either by noninvasive or obtrusive strategies. Most inspectors use JTAG strategies for the Windows Phone since it offers a non-obtrusive strategy for access to the gadget without requiring total dismantling, and numerous Windows Phone models are supported. Windows Phone 8 is just upheld right now, and the gadget must be opened. The system conducting the collection must be Windows 7 and higher.
Oxygen Forensics Suite can get information over a link or by getting to Windows
Phone cloud storage. The primary methodology permits us to get media documents over a link and phonebook contacts and to approach and actively bring over the Microsoft Bluetooth association. For this situation, the information is gained from devices associated locally both through USB cable and Bluetooth association. It is prescribed to consolidate the aftereffect of the two methodologies for a complete image.
The supported collection things include:
- Phone book
- Event logs
- File browser (media included (images, documents, videos))
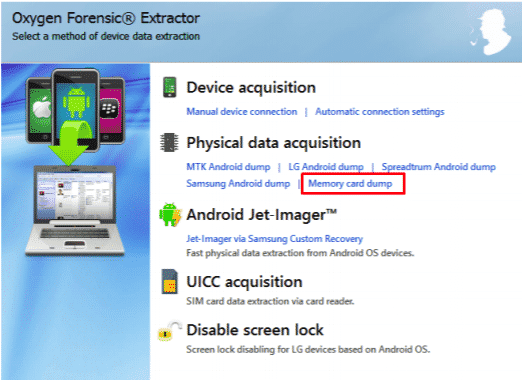
Memory card Extraction:
Oxygen Forensics Suite provides a way of extracting data from FAT32 and EXT formatted memory cards. For this, one has to connect the memory card to the Oxygen Forensics detective through a card reader. On startup, choose an option called “Memory card dump” in physical data acquisition.
The extracted data may contain anything a memory card holds like images, videos, documents, and also the geo-locations of data captured. Deleted data will be recovered with a recycle bin mark on it.
SIM Card data extraction:
Oxygen Forensics Suite provides a way of extracting data from SIM cards. For this, one has to connect the SIM card to the Oxygen Forensics detective (more than one sim card can be connected at a time). If it’s password-protected, a password entering option will be shown, enter the password, and you are good to go. The extracted data may contain calls, messages, contacts, and deleted calls and messages.
Importing Backups and Images:
Oxygen Forensics Suite provides not only a way for data extraction but a way for analyzing data by allowing the import of different backups and images.
Oxygen Forensics Suite supports:
- Oxygen Cloud backup (Cloud Extractor—OCB file)
- Oxygen Backup (OFB file)
- iTunes Backup
- Apple Backup/Image
o Non-Encrypted Apple DMG Image
o Apple File System Tarball/Zipo Decrypted Elcomsoft DMG
o Encrypted Elcomsoft DMG
o Decrypted Lantern DMG
o Encrypted Lantern DMG
o XRY DMG
o Apple Production DMG
- Windows Phone Backup
- Windows Phone 8 JTAG Image
- UFED backup/image
- Android Backup/Image
o Android Backup
o File System Image Folder
o File System Tarball/ZIP
o Android Physical Image /JTAG
o Nandroid Backup (CWM)
o Nandroid Backup (TWRP)
o Android YAFFS2
o Android TOT container
o Xiaomi backup
o Oppo backup
o Huawei backup
- BlackBerry Backup
- Nokia Backup
- Memory Card Image
- Drone image
Viewing and Analyzing extracted data:
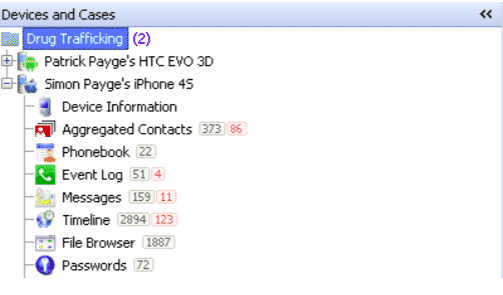
The devices section on the left side of the window will show all the devices by whom data was extracted. If we specify the case, then the case name will appear here also.
The Open Case button will help us in finding cases by the case number and case name assigned to them.
Save case – allows us to save a created case with a .ofb extension.
Add case – allows for creating a new case by adding a case name and case notes
Remove case – removes the selected case and devices from Oxygen Forensic software
Save device – saves information about devices into a .ofb backup file. The file can be used to restore the information later on with Extractor
Remove device – removes selected devices from the list
Devices storage – allows storing software databases on a different disk. Use it when you have a specific drive to hold the database (such as a removable flash drive), or when you are short on free disk space.
Save to Archive button helps in saving cases with .ofb extension so that we can share it with a friend having Oxygen Forensics Suits to open it.
Export or Print button allows us to export or print a specific section of evidence like key evidence or images section etc
Basic Sections:
There are various sections that show a specific type of extracted data.
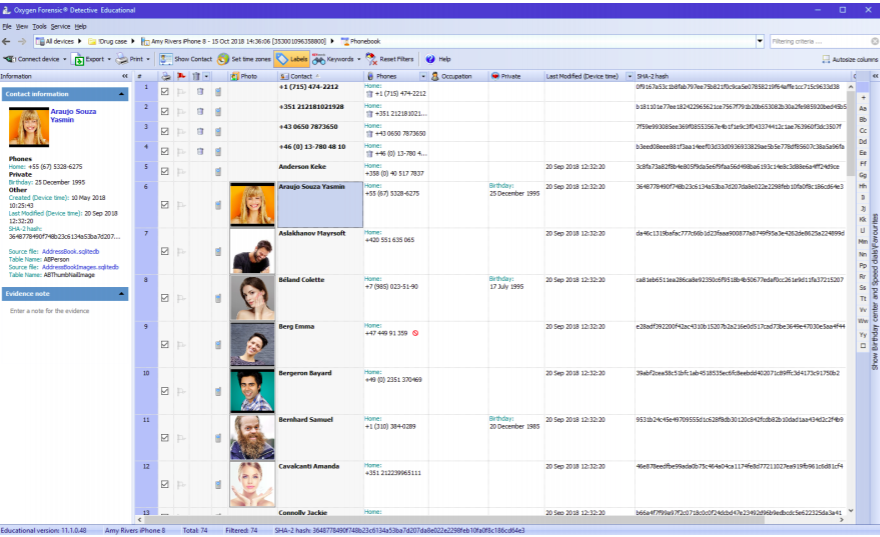
Phonebook Section:
The Phonebook section contains a contact list with personal pictures, custom field labels, and other data. Deleted contacts from Apple iOS and Android OS devices are marked by a “basket” icon.
Calendar Section:
The Calendar section displays all meetings, birthdays, reminders, and other events from the default device calendar as well as from the third-party ones.
Notes Section: The Notes section allows viewing notes with their date/time and attachments.
Messages Section: SMS, MMS, E-mail, iMessages, and messages of other types are shown in the Messages section. Deleted messages from Apple iOS and Android OS devices are highlighted with blue color and marked by a “basket” icon. They are automatically recovered from SQLite databases.
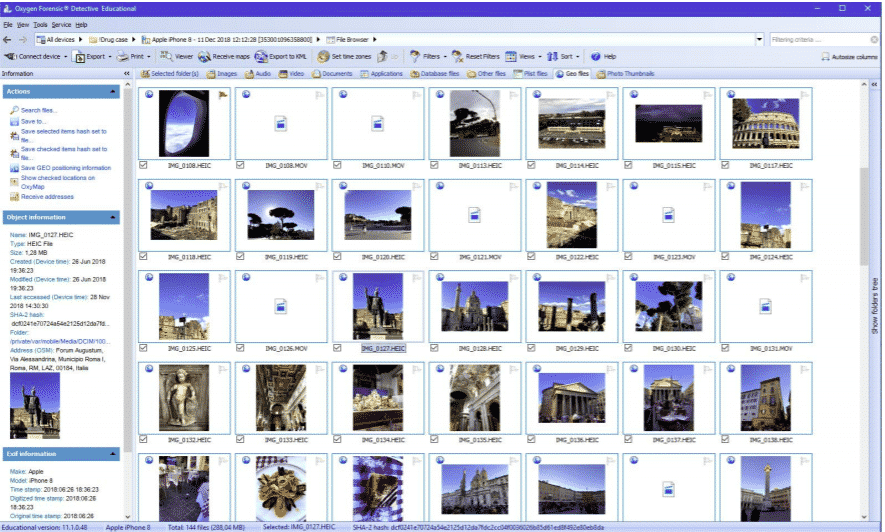
File Browser Section: It gives you access to the entire mobile device file system, including photos, videos, voice records, and other files. Deleted file recovery is also available but highly depends on the device platform.
Event Section: Incoming, outgoing, missed, Facetime calls history – all this information is available in the Event Log section. Deleted calls from Apple iOS and Android OS devices are highlighted with blue color and marked by the “recycle bin” icon.
Web Connections Section: Web Connections segment shows all web associations in a single rundown and permits analyzing hotspots on the guide. In this rundown, forensics analysts can discover when and where the user utilized the Internet to get to and identify his location. The first bookmark grants clients to examine all Wi-Fi associations. Oxygen Forensics Suite programming extricates an inexact geo area of where the Wi-Fi association was utilized. Scaled-down Google Maps are created and appeared by SSID, BSSID, and RSSI data separated from the cell phone. The other bookmark allows examining information about Locations. It presents information about all the network activity of the device (Cell, Wi-Fi, and GPS). It is supported by Apple iOS (jailbroken) and Android OS (rooted) devices.
Passwords Section: Oxygen Forensic® software extracts information about passwords from all possible sources: iOS keychain, apps databases, etc. Passwords can be retrieved from Apple iOS, Android OS, and Windows Phone 8 devices.
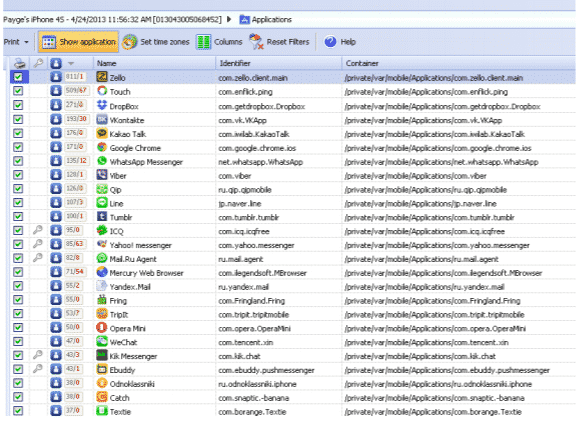
Applications Section: The Applications section shows detailed information about the system and user applications installed in Apple iOS, Android, BlackBerry 10, and Windows Phone 8 devices. Oxygen Forensics Suite supports 450+ applications with 9000+ app versions.
Each application has an extraordinary User Data tab where all parsed client information is found. This tab contains accumulated information of the application arranged for helpful examination (passwords, logins, all the messages and contacts, geo areas, visited places with directions and guides, erased information, and so forth.)
Other than the User Data tab Application watcher has:
- Application data tab shows the entire application vault from which information is parsed
- Application documents tab presents all the records (.plist, .db, .png, and so forth.) related to the application
Social Networks Section: This section contains data extracted from the most popular social platforms and dating applications, including Facebook, Instagram, Linkedin, Twitter, etc. The Facebook section allows examining the device owner’s friends list together with messages, photos, search history, geo-location, and other important information.
Messengers Section: The Messengers section includes sub-sections with data extracted from the most popular messengers: Facebook Messenger, Kik, Line, Skype, WeChat, Whatsapp, Viber, etc. WhatsApp Messenger allows viewing the contact list, messages, shared data, deleted info, and other evidence.
Notes Section: Evernote section permits seeing all the notes made, shared, and matched up by the device user. Each note is made with the geo-location of where the device owner is
found, and this data is accessible in Oxygen Forensics Suite. There is a chance to investigate erased notes also.
Web Browsers Section: Web Browsers section allows the user to extract and examine cache files such as a list of Internet sites and downloaded files of the most popular mobile web browsers (pre-installed as well as 3rd party ones) including, but not limited to Safari, Default Android Web Browser, Dolphin, Google Chrome, Opera, etc. It recovers the browser’s history as well.
Navigation Section: It includes data extracted from the most popular navigation apps (Google Maps, maps, etc.).
Multimedia Section: Multimedia section includes sub-sections with data extracted from the most popular multimedia apps: Hide It Pro, YouTube, etc. The Hide It Pro section shows the media files (images and video) that were hidden by the device owner. To see them on the device, the password is required. Oxygen Forensics Suite grants access to this hidden data bypassing the password.
Drone Section: The drone section includes sub-sections with data extracted from the most popular drone apps, like DJI GO, DJI GO 4, Free Flight Pro, etc. Forensic examiners can extract the drone flight history, pictures, and videos uploaded to the app, drone owner account details, and even deleted data. Oxygen Forensics suite can also extract and decrypt DJI tokens from drone mobile apps. This token will give access to DJI cloud data.
Organized data:
The Timeline:
Timeline section organizes all calls, messages, calendar events, application activities, web connections history, etc. in a chronological way, so it is easy to analyze the device usage history without any need to switch between different sections. The timeline section is supported for one or several mobile devices so you can easily analyze the group activity in a single graphical view. The data can be sorted, filtered, and grouped by dates, usage activity, contacts, or geo-data. The GEO Timeline tab allows experts to view all geo-location information from the device, locating places where the suspect used the mobile device. With the help of Maps and Routes, button investigators can build routes to track the device owner’s movements within a specified time frame or find frequently visited places.
Aggregated Contacts:
The program with its Aggregated Contacts section allows forensic specialists to analyze contacts from multiple sources such as the Phonebook, Messages, Event logs, various Messengers and Social Networks, and other apps. It also shows cross-device contacts from several devices and contacts in groups created in various applications. By enabling aggregated contacts analysis, the software greatly simplifies investigators’ work and allows discovering relations and dependencies that could otherwise escape the eye.
Key Evidence:
The Key Evidence area offers a perfect, uncluttered perspective on proof set apart as fundamental by forensic investigators. Measurable authorities can check certain things having a place with different areas as being basic proof, at that point, exploring them at the same time paying little heed to their unique area. Key Evidence is a totaled view that can show chosen things from all areas accessible in Oxygen Forensics Suite. The segment offers the capacity to audit important data at a solitary look, focusing one’s endeavors on the main thing and sifting through diverting immaterial information.
SQL Database Viewer:
The SQLite Database Viewer allows analyzing database files from Apple, Android, BlackBerry 10, WP 8 devices in SQLite format. The files have notes, calls, SMS in it.
PList Viewer:
The Plist Viewer allows analyzing .plist files from Apple devices. These files contain information about Wi-Fi access points, speed dials, the last cellular operator, Apple Store settings, Bluetooth settings, global application settings, etc.
Drone Logs Import:
The product additionally permits bringing in drone log .dat records legitimately into Oxygen Forensics Suite Maps to imagine areas and track an automaton course. Logs can be taken from the automaton dump or the DJI Assistant application introduced on the owner of the drone’s PC.
Search:
It’s a common situation for you to need to find some text, person, or phone number in the extracted mobile device information. OxygenForensics Suite has an advanced search engine. Global Search permits finding client information in each segment of the gadget. Apparatus offers to scan for text, telephone numbers, messages, geo coordinates, IP addresses, MAC addresses, Credit Card numbers, and hash sets (MD5, SHA1, SHA256, Project VIC). Standard articulations library is accessible for progressively custom pursuit. Specialists can look through the information in a device or more than one device. They can pick the segments where to look through the question, apply boolean terms, or pick any of predefined designs. Catchphrase list director permits making a special set of terms and performing a look for every one of these terms without a moment’s delay. For instance, these can be the arrangements of names or the arrangement of hostile words and expressions. Worldwide Search device spares all outcomes and offers printing and planning reports for any number of searches.
Some Important things to remember are
- Firstly make sure you have installed the drivers for the device. You can download the driver pack from your customer area

- If you connect a device press Connect device button on the toolbar to start Oxygen Forensics Suite
- If you connect the Apple iOS device, plug it in, unlock, and trust the computer on the device.
- If you connect to an Android OS device, enable Developer mode on it. Go to Settings > About Phone > Build number menu and tap it 7 Then go to Settings > Developer Options > USB Debugging menu on the device. Tap the USB Debugging checkbox and plug the device into the computer.
- If an Android OS device is password-protected, check if it is supported by the bypass methods located under Physical data acquisition in Oxygen Forensics Suite.
Conclusion:
The scope of analysis Oxygen Forensics Suite provides way bigger than any other forensic investigation tool, and we can retrieve much more information from a smartphone using the Oxygen Forensics suite than any other logical forensics investigation tool, especially in case of mobile devices. Using Oxygen Forensics Suite, one can acquire all the information about mobile devices, which includes geo-location of a cell phone, text messages, calls, passwords, deleted data, and data from a variety of popular applications. If the device is locked Oxygen Forensics Suite can bypass the lock screen passcode, password, pin, etc. and extract the data from a list of supported devices (android, IOs, Blackberry, Windows phones included), it’s a huge list and entries are increasing day by day. Oxygen Forensics has made a partnership with MITRE Corporation to deliver the fastest extraction method for Android devices. Thanks to the new Jet-Imager module, Android devices are acquired many times faster than the previous methods allowed. The Jet-Imager module allows users to create full physical dumps from Android devices, on average, up to 25% faster. The extraction speed depends on how much data the device has. Oxygen Forensics Suite is a go-to option for a forensic investigation on a mobile device for any forensic investigator.
from Linux Hint https://ift.tt/396V5GV







0 Comments