Metasploit Framework:
Metasploit framework is a penetration testing tool that can exploit and validate vulnerabilities. It contains the basic infrastructure, specific content, and tools which are necessary for penetration testing and vast security assessment. It is one of the most famous exploitation frameworks and is updated regularly; new exploits are updated as soon as they are published. It has many tools that are used for creating security workspaces for vulnerability testing and penetration testing systems.
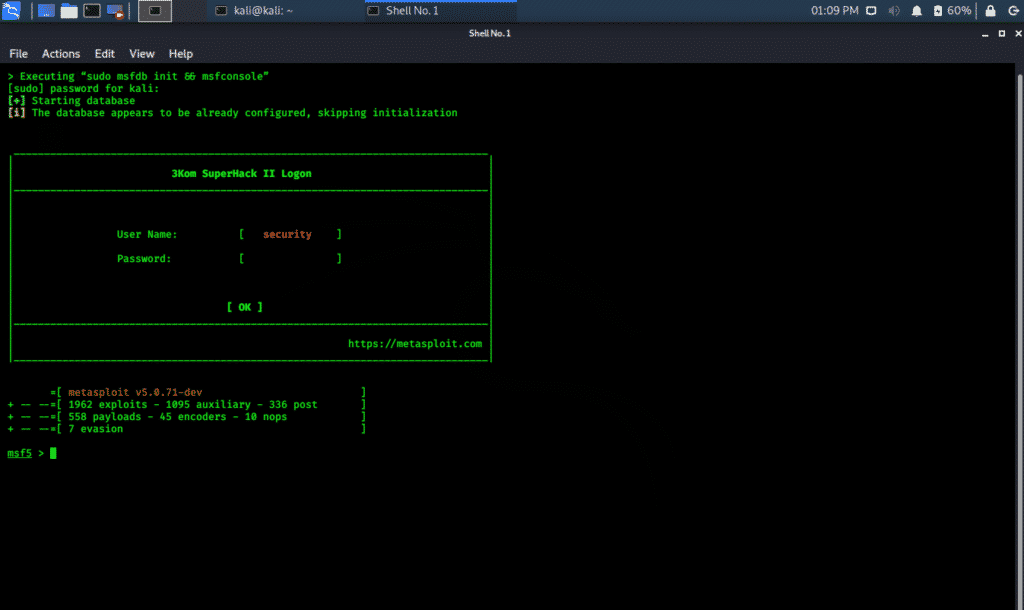
The Metasploit Framework can be accessed in Kali Whisker Menu as well as can be launched directly from the terminal.
Check the following commands for various tools included in Metasploit Framework.
Metasploit is a very powerful framework in terms of exploitation and contains a larger number of exploits for different platforms and devices.
Nmap tool (Network Mapper):
Nmap short for network mapper is an open-source utility that is used for scanning and discovering vulnerabilities in a network. Nmap is used by Pentesters and other security professionals to discover devices running in their networks. It also displays the services and ports of every host machine, exposing potential threats.
Nmap is highly flexible, from monitoring a single host machine to a wide network that consists of more than a hundred devices. The core of Nmap contains a port-scanning tool that gathers information by using packets to a host machine. Nmap collects the response of these packets and shows whether a port is closed, open, or filtered.
Performing a basic Nmap Scan:
Nmap is capable of scanning and discovering a single IP, a range of IP addresses, a DNS name, and scan content from text documents. I will show how to perform a basic scan on Nmap by using localhost IP.
Step one: Open terminal window from Kali Whisker menu
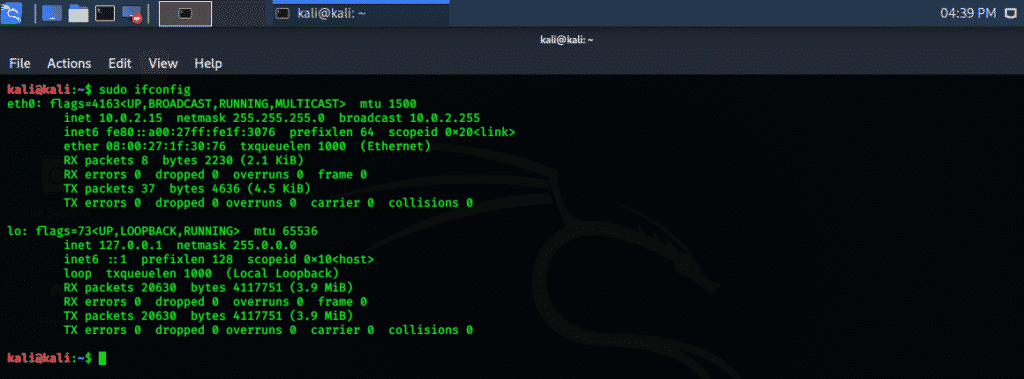
Step two: Enter the following command to display your localhost IP. Your IP address is display in “eth0” as “inet xx.x.x.xx,” in my case 10.0.2.15, as displayed below.
Step three: Note down this IP address and write the following command in the terminal. It scans the first 1000 ports on the localhost machine and returns a result.
Step four: Analyze the results.
Nmap scans only the first 1000 ports by default, but this can be changed using different commands.
Scanning “scanme” with Nmap:
Nmap can scan the “scanme” domain of Nmap and shows all the open, closed, and filtered ports. It also shows the encryption algorithms associated with those ports.
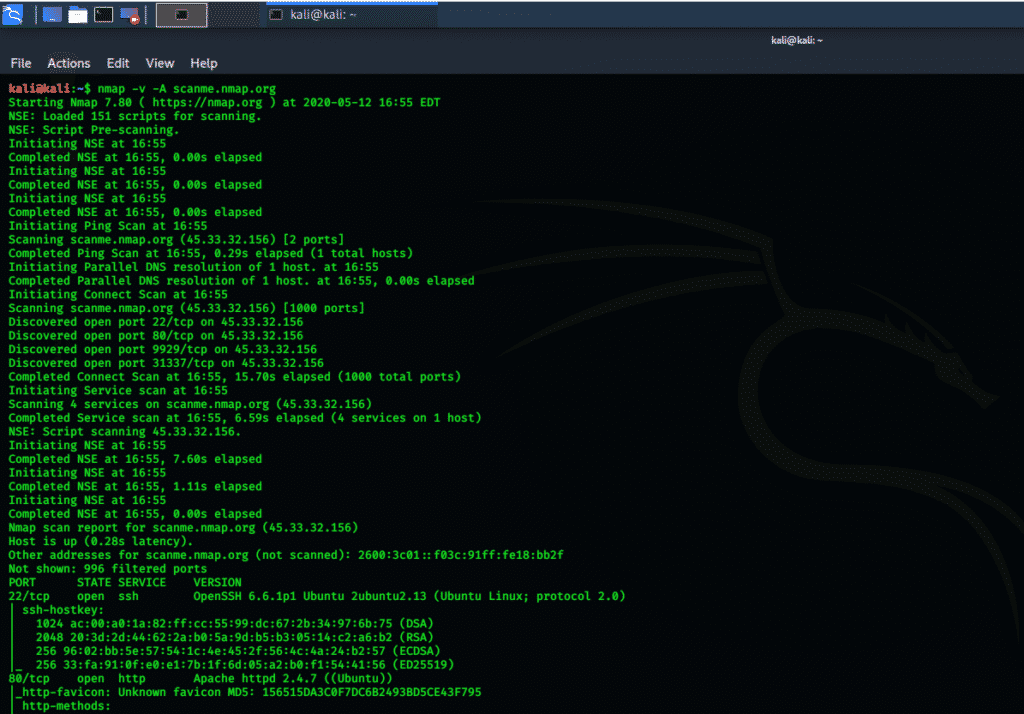
Step one: Open a terminal window and execute the following command.
Step two: Analyze the results. Check in the above terminal window for PORT, STATE, SERVICE, and VERSION part. You will see the open ssh port and also the OS information. Below you can see ssh-hostkey and its encryption algorithm.
Using Nmap and Metasploit in Kali Linux 2020.1 tutorial:
Now that you have obtained a basic view of the Metasploit framework and Nmap, I will show you how to use Nmap and Metasploit, and a combination of these two is very necessary for the security of your network. Nmap can be utilized within the Metasploit framework.
Step one: Open the Kali Whisker menu, and in search bar type Metasploit, press enter, and Metasploit will open in the terminal window.
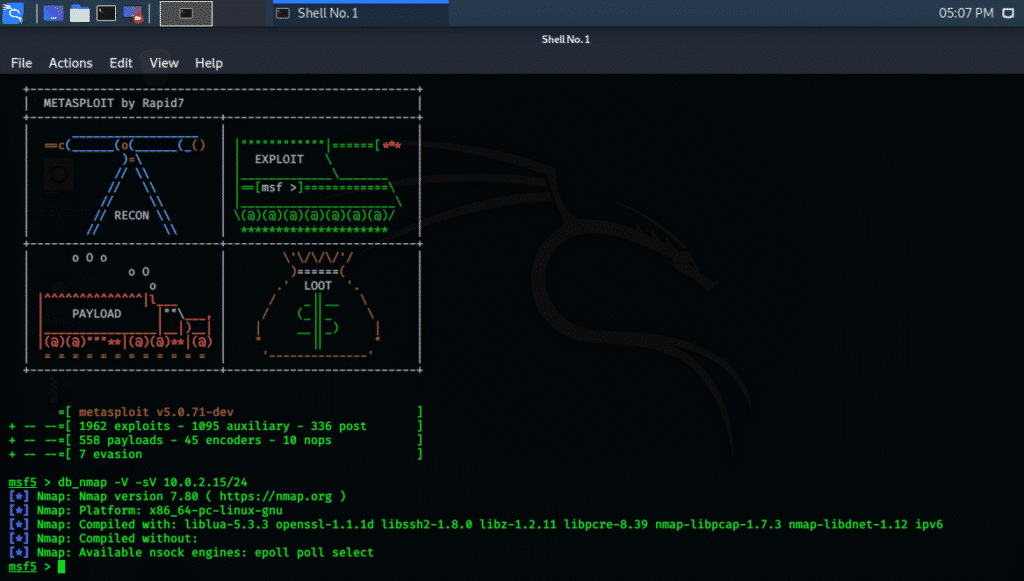
Step two: In the Metasploit window type command written below, replace the current IP address with your localhost IP. The following terminal window will show you the results.
The DB stands for database, -V stands for verbose mode, and -SV stands for service version detection.
Step three: Analyze all the results. The above command shows the version number, platform, and kernel information, libraries used. This data is further used from executing exploits using the Metasploit framework.
Conclusion:
By using Nmap and Metasploit framework, you can secure your IT infrastructure. Both of these utility applications are available on many platforms, but Kali Linux provides a pre-installed configuration for testing the security of a network.
from Linux Hint https://ift.tt/2N8wlno





0 Comments