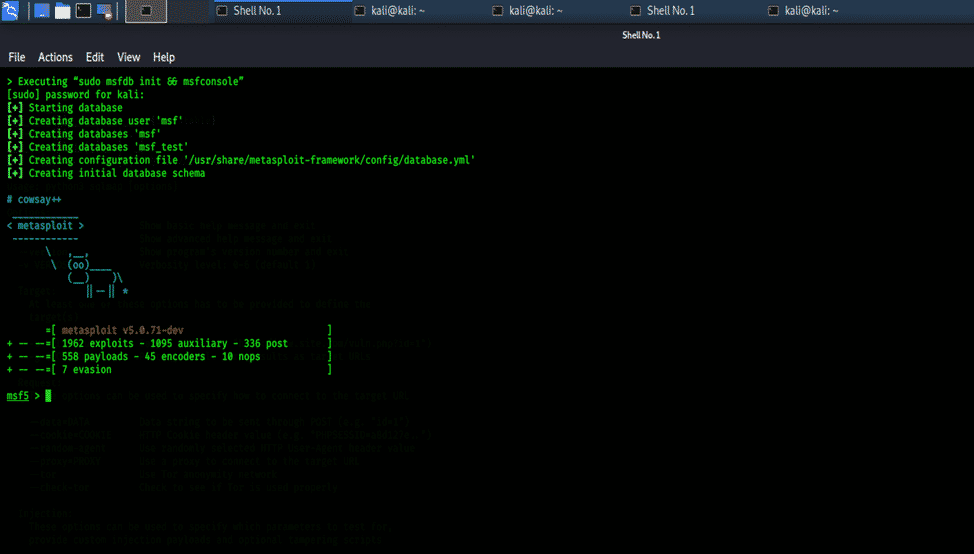
Metasploit MSF:
Metasploit Framework is a penetration testing tool that can exploit and validate vulnerabilities. It has most of the options required for social engineering attacks and is considered one of the most famous exploitation as well as social engineering framework. MSF is updated regularly; new exploits are updated as soon as they are published. It has many tools that are used for creating security workspaces for vulnerability testing and penetration testing systems.
Metasploit Framework can be accessed in Kali Whisker Menu as well as can be launched directly from the terminal.
Check the following commands for various tools included in Metasploit Framework.
$ msfdb
$ msfrpc -h
$ msfvenom -h
$ msfrpcd -h
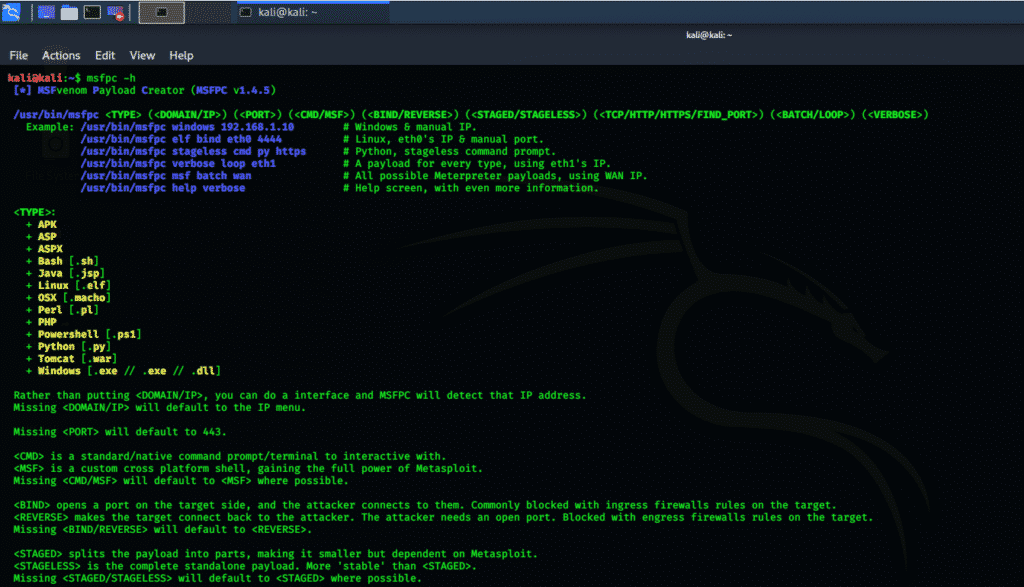
msfpc:
MSFPC is a package that contains several tools that generate various payloads based on user-specific options. It is also called MSFvenom payload creator, and its goal is to automate the processes involved in working with Metasploit and msfvenom. Msfpc help command can be launched using the following console as follows.
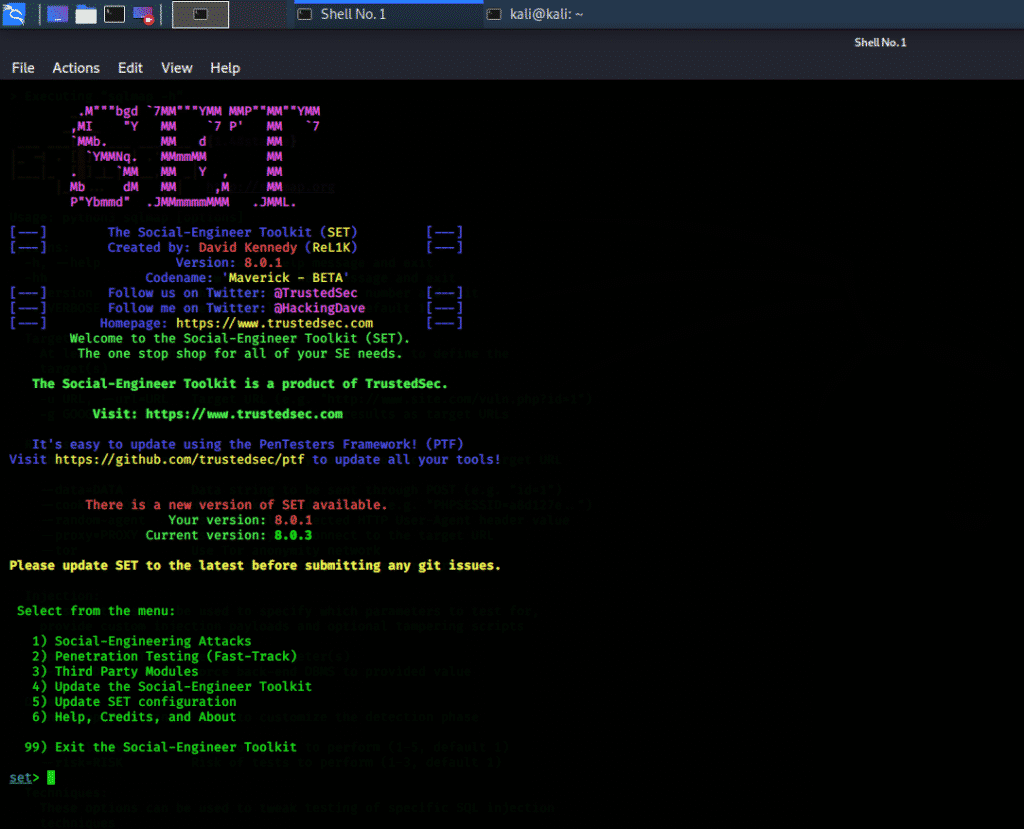
Social engineering toolkit SET:
SET or social engineering toolkit is an open-source and free-ware penetration testing tool for social engineering and custom attacks. Social engineering toolkit has several custom attack vectors that can help in making a successful attack in no time. It is very fast and has two main types of attacks. Social engineering attacks and penetration testing or fast-track attacks. It can be started directly from the terminal window using the following command.
It has three main options to select from; option 1 is for social engineering attacks, option 2 is for penetration testing attack, and option 3 involves 3rd party apps or tools that can help in inserting malicious code into target web email or web page. One of the best attacks it has is called the spear-phishing attack in which one module creates a special email message and sends them to a wide range of people with attached malicious code. For configuration of spear phishing, the SENDMAIL option must be turned on.
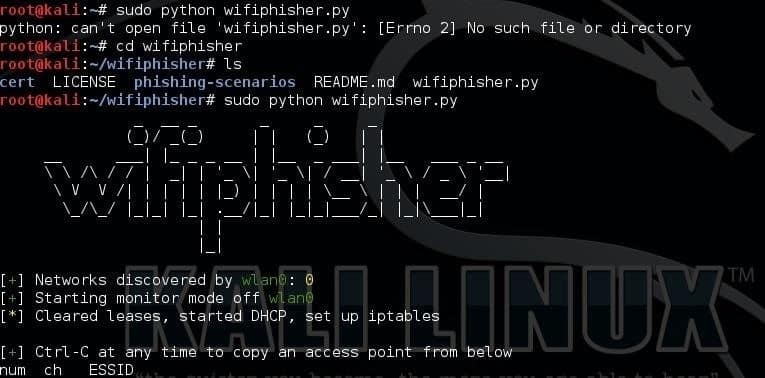
Wifiphisher:
It is a unique social engineering tool that configures an automated phishing attack on Wi-Fi internetworks to get the credentials of a target user with the help of Malware. This social engineering attack tool gets WPA/WPA2 passwords and doesn’t perform brute force attacks for finding passwords. It is done with the help of a man-in-the-middle attack with the addition of the evil twin attack. It is performed in 3 main steps which are stated below:
The target device becomes unauthenticated from their access points.
Wifiphisher creates a rogue AP for the target device and copies all the information.
The target device is taken to a realistic page which contains the phishing page disguised.
The following command will launch the python script:
Maltego:
This social engineering framework is created for delivering a complete picture of the threat to an organization’s workspace. Maltego gathers information about a network or individual, and it is an open-source tool. It draws a graph that can assist in analyzing the link between various chunks of data online. It has a special capability of demonstrating the complexity of failure points and trust relationships present in a network.
Maltego can work in networks as well as resource-based entities and can locate and visualize information. It shows the relationship between people, social networks, organizations, websites, domains, DNS names, IP addresses, affiliations, documents, and files. Maltego can be launched directly from Kali Whisker Menu.
Maltego is a very easy and fast software; it has a graphical interface and shows the direct graphs clearly. It can be modified to your requirements and a very flexible framework. It is used to gather information about all the modules related to the security of an entity. The links found using open intelligence is represented with a graph that shows detailed visual information. The results are concise and clear with authenticity.
Conclusion:
All of these tools are very easy to use and require a little bit of work. These are the best tools for social engineering attacks.
from Linux Hint https://ift.tt/2zMpBZi




0 Comments