While SQL Injection can be dangerous, executing different commands by web page input to perform SQLi can be a very hectic job. From gathering data to developing the right payload can be a very time-taking and sometimes frustrating job. This is where the tools come into play. There are numerous tools available for testing and exploiting different types of SQL Injections. We will discuss some of the best ones.
Havij:
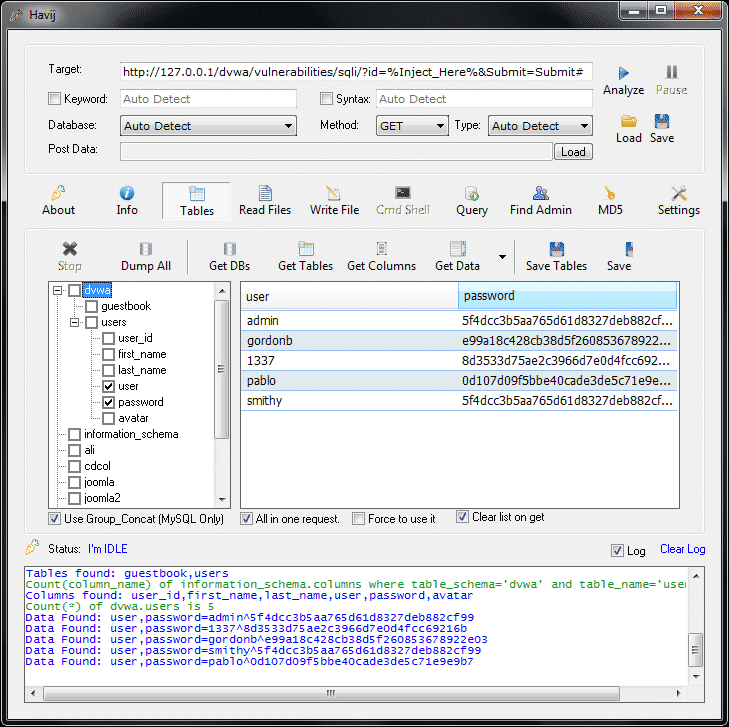
Havij (which means carrot in Persian) is a tool by ITSecTeam, an Iranian security company. It is a GUI enabled, fully automated SQLi tool and supports a variety of SQLi techniques. It was developed to assist penetration testers in finding vulnerabilities on web pages. It is a user-friendly tool and includes advanced features also, so its good for both beginners and professionals. Havij also has a Pro version. The exciting thing about Havij is the 95% successful injection rate on vulnerable targets. Havij is only made for windows but one can use wine to make it work on Linux. Though ITSecTeam’s official site has been down for a long time, Havij and Havij Pro are available on many websites and GitHub Repos.
BBQSQL:
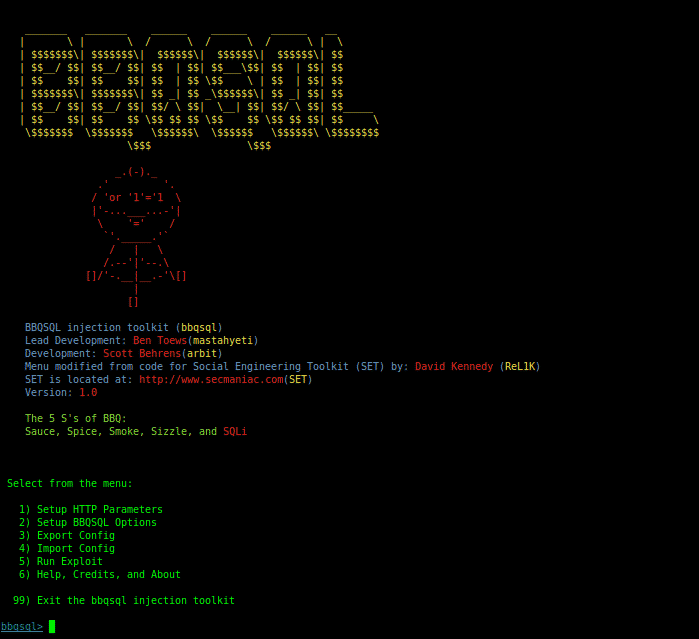
BBQSQL known as ‘Blind SQL’ injection framework helps you to address issues when the available exploitation tools don’t work. Written in python, it is a sort of semi-automatic tool which allows customization to some extent for any complex SQL injection findings. BBQSQL asks several questions in a menu-driven approach and then creates the injection/attack according to the user’s response. It is a very versatile tool with built-in UI to make its usage easier. And the use of python gevent makes it pretty fast. It provides information regarding Cookies, Files, HTTP Auth, Proxies, URL, HTTP Method, Headers, Encoding methods, Redirects behavior, etc. The pre-usage requirements include setting up parameters, options, then configure the attack as required. The tool’s configuration can be changed to use either a frequency or a binary search technique. It can also determine if the SQL injection worked by just looking for some specific values in the HTTP responses from the application. An Error message is displayed by the database which complains about the incorrect syntax of SQL Query if the attacker successfully exploits SQL Injection. The only difference between Blind SQL and normal SQL injection is the way the data is being retrieved from the database.
Install BBQSQL:
Leviathan:
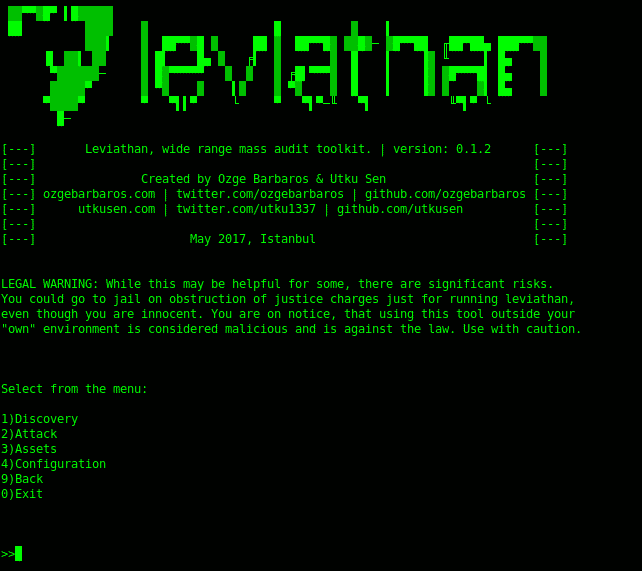
The word Leviathan refers to a sea creature, sea devil, or sea monster. The tool is so named due to its attacking feature. The tool was first launched at Black Hat USA 2017 Arsenal. It is a framework that consists of many open source tools including masscan, ncrack, DSSS, etc to perform different actions including SQLi, custom exploit, etc. The tools can be used in combination too. It is commonly used for penetration testing tasks, like discovering machines and identifying the vulnerable ones, enumerating services working on these devices, and finding attack possibilities through attack simulation. It can identify vulnerabilities in Telnet, SSH, RDP, MYSQL, and FTP. Leviathan is highly proficient in checking SQL vulnerabilities on URLs. The basic objective of the Leviathan tool is to perform massive scans on many systems at once. The proficiency of checking for SQL vulnerabilities makes leviathan. The dependencies required to use Leviathan Framework are bs4, shodan, google-API-python-client, lxml, paramiko, requests.
Install Leviathan:
$ cd leviathan
$ pip install -r requirements.txt
WhiteWidow:
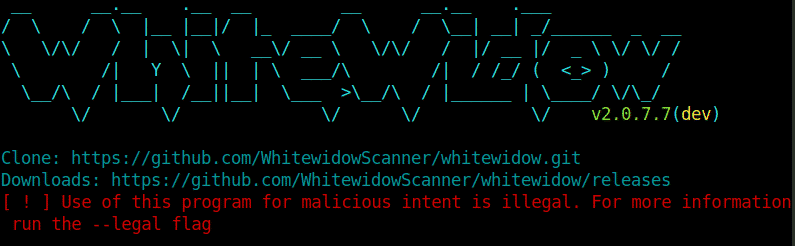
Whitewidow is a commonly used tool for vulnerability scanning in application security and penetration testing. Most people interested in this tool are pen-testers and security professionals. Whitewidow is also open-source and is an automated SQL vulnerability scanner that can use a file list or Google to scrape potentially vulnerable websites. The prime objective of this tool was learning and to tell users what vulnerability looks like. WhiteWidow requires some dependencies to work, such as: mechanize, nokogiri, rest-client, webmock, rspec, and vcr. It is developed in a ruby programming language. Thousands of carefully researched queries are used to scrape Google for finding vulnerabilities in different websites. When you Launch Whitewidow, it will start checking for vulnerable sites straightaway. They can be later exploited manually.
Install WhiteWidow:
$ cd whitewidow
$ bundle install
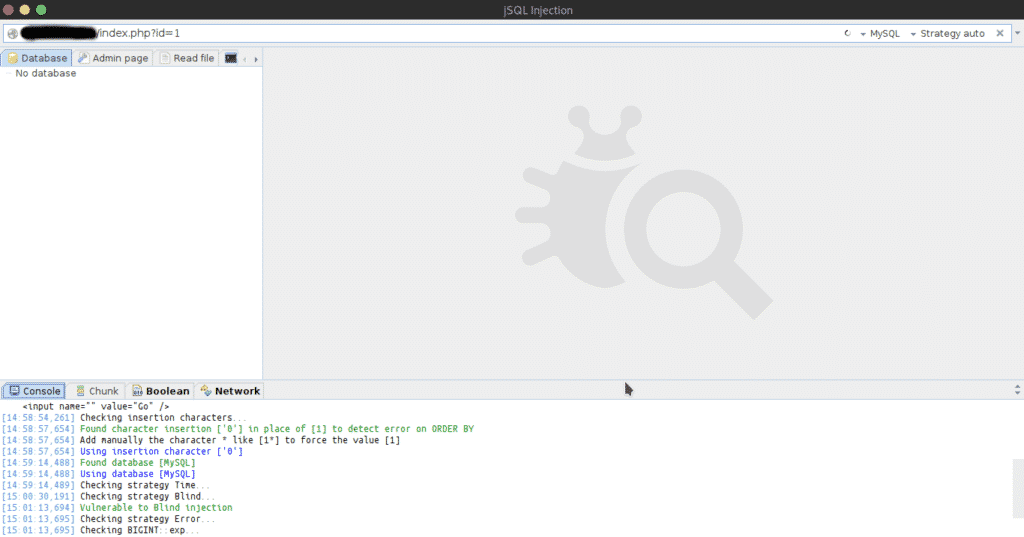
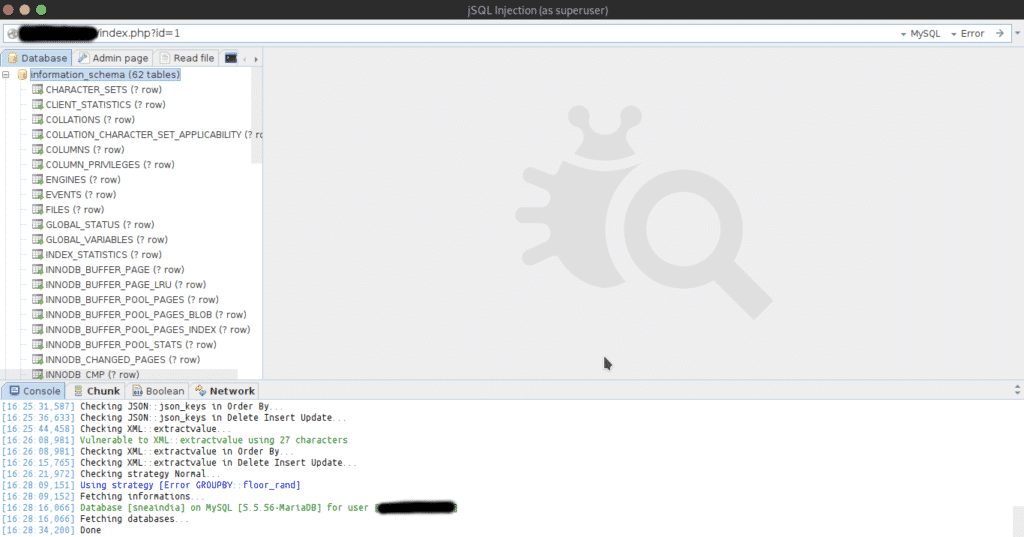
jSQL Injection:
jSQL is a java-based automatic SQL Injection tool, hence the name jSQL.
It is FOSS and is cross-platform compatible. It is assembled using libraries like Hibernate, Spock, and Spring. jSQL Injection supports 23 different databases including Access, MySQL, SQL Server, Oracle, PostgreSQL, SQLite, Teradata, Firebird, Ingris, and many more. jSQL Injection is placed on GitHub and uses platform Travis CI for continuous integration. It checks for multiple injection strategies: Normal, Error, Blind, and Time. It has other features such as searching for administration pages, brute-force of password hash, creation and visualization of Web shell and SQL shell, etc. jSQL Injection can also read or write files.
jSQL injection is available in Operating Systems like Kali, Parrot OS, Pentest Box, BlackArch Linux, and other pen-testing distros.
Install jSQL:
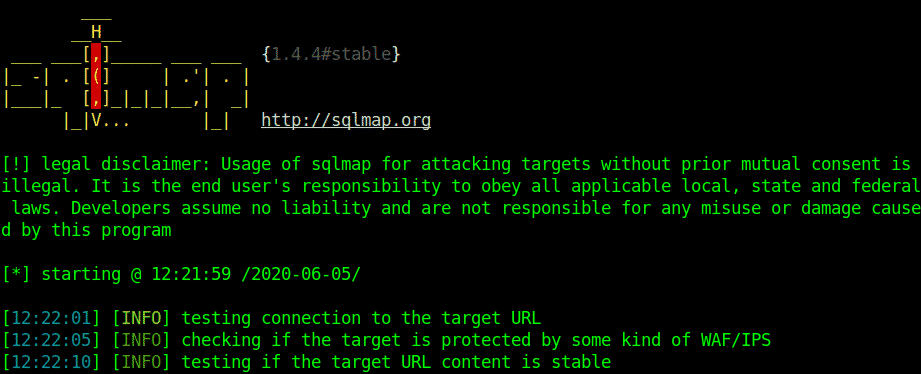
SQLmap
SQLmap is an automated tool written in python that automatically checks for SQL vulnerabilities, exploits them, and takes over database servers. It is free and open-source software and is probably the most commonly used tool for pen-testing SQLi vulnerable targets. It is free and open-source software with an amazingly powerful detection engine. Created by Daniele Bellucci in 2006, it was later developed and promoted by Bernardo Damele. The most notable step in development for sqlmap was Black Hat Europe 2009, coming to the spotlight with all the media attention. SQLmap supports most types of Databases, SQL Injection techniques, and password cracking based on dictionary-based attacks. It can also be used to edit/download/upload files in a database. Meterpreter’s (Metasploit) getsystem command is used for Privilege Escalation. For ICMP tunneling, an impacket library is added. SQLmap provides retrieval of results using DNS recursive resolution much faster than time-based or boolean-based methods. SQL queries are used to trigger required DNS requests. SQLmap is supported by python 2.6,2.7 and python 3 onwards.
According to Ed Skoudis, a complete SQLmap attack depends on a 5-step model:
- Reconnaissance
- Scanning
- Exploit
- Keeping access
- Covering tracks
Install SQLmap:
Or
$ cd sqlmap
$ python sqlmap.py
Though this list is a compact one, it consists of the most popular tools that are used for detecting and exploiting SQLi. SQL Injection is a very common vulnerability and comes in a variety of shapes, so the tools are really helpful for the detection of these vulnerabilities and help a lot of penetration testers and script-kiddies do the job in a really easy way.
Happy Injecting!
Disclaimer: The above-written article is only for educational purposes. It is the user’s responsibility to not use the above-given tools on a target without permission.
from Linux Hint https://ift.tt/37MsndC




0 Comments